The Flipper Zero portable wireless pen-testing and hacking tool can be used to aggressively spam Bluetooth connection messages at Apple iOS devices, such as iPhones and iPads.
The technique was devised by a security researcher using the ‘Techryptic’ moniker, who published the following YouTube video showcasing how it works.
Spamming Bluetooth notifications
Apple devices supporting Bluetooth Low Energy (BLE) technology utilize advertising packets (ADV packets) to announce their presence to other devices.
ADV packets are used extensively in the Apple ecosystem to exchange data via AirDrop, connect the Apple Watch or AppleTV, activate Handoff, and many more scenarios.
Flipper Zero, being a wireless and radio-capable tool, can spoof ADV packets and transmit them according to the BLE protocol. Hence, BLE-enabled devices in range will perceive these broadcasts as legitimate connection requests.
This can be used to confuse a target by sending them bogus requests, making it difficult to discern legitimate devices among a large number of fakes or mimic trusted devices to perform phishing attacks.
Techryptic focuses on the pranking aspect of the attack, claiming that if a large volume of requests is generated, the target device will display numerous non-stop notifications, which can severely disrupt the user experience.
“For iOS users, this mimicry can be more than just an annoyance. It can lead to confusion, disrupt workflows, and in rare cases, pose security concerns,” reads Techryptic’s writeup.
“It underscores the importance of being aware of the devices around us and the potential vulnerabilities inherent in wireless communications.”
The researcher says that to perform the attack, the Flipper Zero firmware needs to be updated to enable Bluetooth functionality, and the ‘gap.c’ file has to include the code that will generate the fake notification.
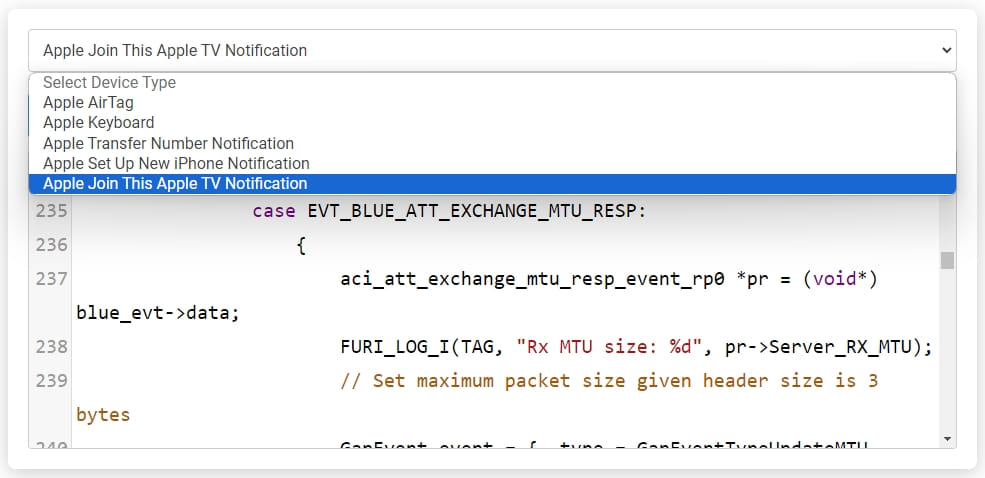
Techryptic has created and shared code for generating the following notifications:
- AirTag connection request
- Apple Keyboard connection request
- Transfer number notification
- “Set up new iPhone” notification
- “Join this Apple TV” notification
Flipper Zero users who want to experiment with this attack may copy the code generated on Techryptic’s site for each notification choice to the ‘gap.c’ and patch their firmware, so minor tweaking is required.
While most of these attacks require the Flipper Zero to be in close proximity to an iOS device, the researcher told TechCrunch that he developed a technique that would work over thousands of feet using an amplifier. However, the researcher does not plan on releasing this method due to its greater risk for abuse.
The researcher noted on X that the attack works even if the target device is in airplane mode, as Apple has no mitigations or safeguards in place to prevent this unlikely abuse scenario.
BleepingComputer has contacted Apple with a request for a comment on the above, but we have not heard back by publication time.
