Security researchers have identified a severe pre-authentication SQL injection vulnerability in Fortinet’s FortiWeb Fabric Connector, designated as CVE-2025-25257, that allows unauthenticated attackers to execute unauthorized SQL commands and potentially achieve remote code execution.
The vulnerability affects multiple versions of FortiWeb, including 7.6.0 through 7.6.3, 7.4.0 through 7.4.7, 7.2.0 through 7.2.10, and 7.0.0 through 7.0.10, with patches available in newer versions.
FortiWeb’s Fabric Connector serves as integration middleware between FortiWeb web application firewalls and other Fortinet ecosystem products, enabling dynamic security policy updates based on real-time infrastructure changes and threat intelligence.
Technical Details of the SQL Injection Flaw
The vulnerability stems from improper input sanitization in the get_fabric_user_by_token function within FortiWeb’s authentication mechanism.
Researchers discovered that the function directly incorporates user-controlled input from HTTP Authorization headers into SQL queries without proper validation or escaping.
The vulnerable code uses a format string approach, constructing queries like select id from fabric_user.user_table where token='%s' where the %s placeholder is replaced with attacker-controlled data from the Authorization Bearer token.
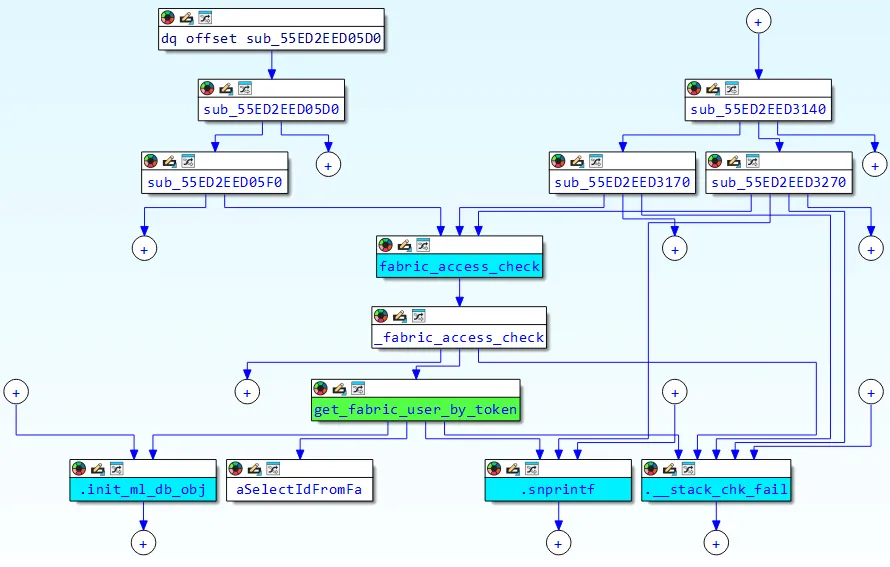
The authentication process extracts tokens from Authorization headers using the format Bearer %128s, which presents both opportunities and constraints for exploitation.
While the sscanf function limits input to 128 characters and stops parsing at the first space character, attackers can bypass these restrictions using MySQL comment syntax (/**/) to replace spaces in their injection payloads.
This allows for complex SQL injection attacks despite the apparent input limitations.
Fortinet has addressed the vulnerability in patched versions by replacing the vulnerable format string queries with prepared statements using MySQL’s mysql_stmt_prepare function.
The updated implementation uses parameterized queries with placeholders (SELECT id FROM fabric_user.user_table WHERE token = ?) that properly separate SQL code from user data, preventing injection attacks.
Escalation from SQL Injection to Remote Code Execution
Security researchers demonstrated how this SQL injection vulnerability can be escalated to achieve full remote code execution through a sophisticated attack chain.
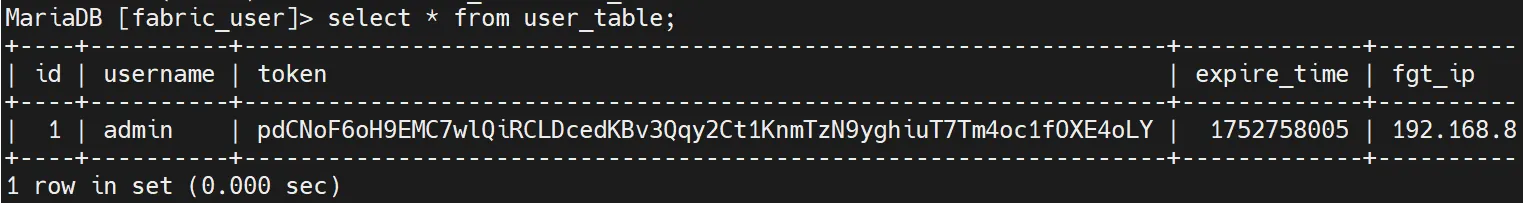
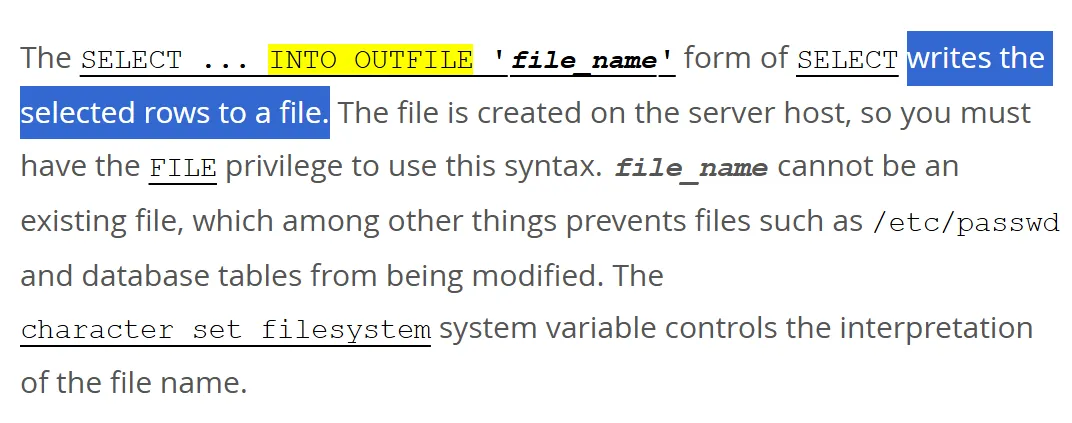
The exploitation leverages MySQL’s INTO OUTFILE statement to write arbitrary files to the target system, combined with Python’s site-specific configuration hooks for code execution.
Key steps in the attack chain include:
- Using SQL injection to write a malicious
.pthfile into Python’s site-packages directory. - Crafting payloads using MySQL’s
UNHEX()function to sidestep character restrictions. - Storing code in database columns and then dumping the contents via
INTO OUTFILEwith relative file paths. - Triggering Python code execution by accessing the exposed
/cgi-bin/ml-draw.pyscript, which loads the malicious.pthfile as part of its startup routine.
This exploitation chain bypasses several system restrictions and demonstrates how a simple injection can rapidly escalate into a full compromise of the affected system.
Organizations running affected FortiWeb versions should immediately implement detection measures and apply available patches.
The vulnerability can be detected by monitoring for specific HTTP requests to fabric-related API endpoints, particularly /api/fabric/device/status, /api/fabric/authenticate, and /api/v[0-9]/fabric/widget paths.
Security teams should watch for Authorization headers containing SQL injection indicators such as single quotes, MySQL comment syntax (/**/), or boolean logic statements like 'or'1'='1.
Successful exploitation attempts typically return HTTP 200 responses with JSON data containing device information, while failed attempts on patched systems return HTTP 401 Unauthorized responses.
Fortinet has released patches for all affected versions, with users advised to upgrade to FortiWeb 7.6.4 or above, 7.4.8 or above, 7.2.11 or above, or 7.0.11 or above depending on their current deployment.
As an immediate mitigation, organizations can restrict access to fabric API endpoints until patches are applied, though this may impact legitimate integration functionality with other Fortinet products.
Stay Updated on Daily Cybersecurity News. Follow us on Google News, LinkedIn, and X.
