A large social media campaign was launched to promote a free Artificial Intelligence (AI) video editor. If the “free” part of that campaign sounds too good to be true, then that’s because it was.
Instead of the video editor, users got information stealing malware. Lumma Stealer was installed on Windows machines and Atomic Stealer (AMOS) on Macs.
The campaign to promote the AI video editor was active on several social media platforms, like X, Facebook, and YouTube…
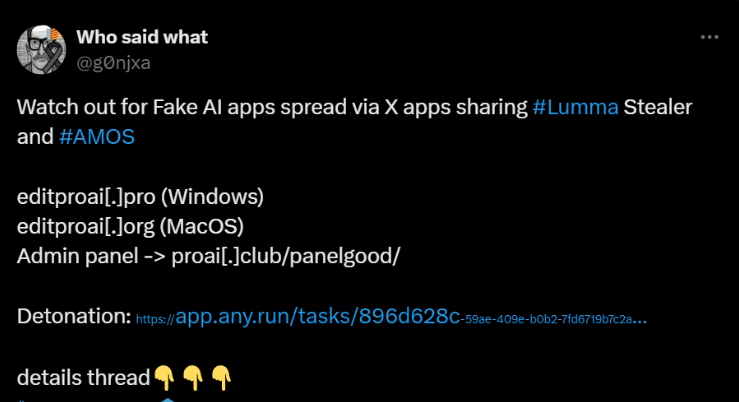
…and had been active for quite a while. as you can see from this tweet.

The criminals seem to have used a lot of accounts to promote their “product” as you can see from this search on X.

Some accounts were expressly created for this purpose, while others look like they may have been compromised accounts.
The campaign looks well organized, and looks so legitimate that it took quite a while before a researcher found out and tweeted about the threat.
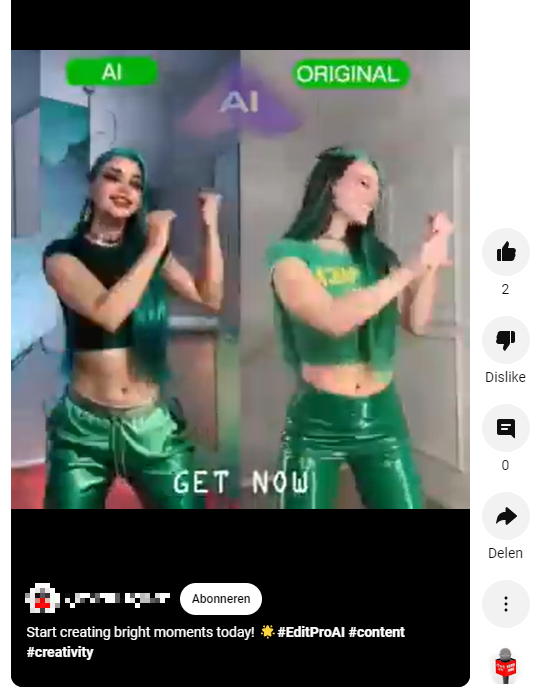
When interested individuals follow the links, they’ll end up on a professional looking website—exactly what you would expect.

But if they click the “GET NOW” button, they’ll download the information stealer and infect their device. The file is called “Edit-ProAI-Setup-newest_release.exe” for Windows, and “EditProAi_v.4.36.dmg” for macOS.
Lumma is available through a Malware-as-a-Service (MaaS) model, where cybercriminals pay other cybercriminals for access to malicious software and its related infrastructure. Lumma steals information from cryptocurrency wallets and browser extensions, as well as two-factor authentication details. Lumma is often distributed via email campaigns, but nothing stops the cybercriminals from spreading it as a download for an AI editor, as they did here.
AMOS makes money for its operators by finding and stealing valuable information on the computers it infects, such as credit card details, authentication cookies, passwords and cryptocurrency. Besides stealing data from the web browsers themselves, AMOS can also steal data from browser extensions (plugins).
What if you installed one of these?
Both stealers are after login credentials and financial information, so there are a few things you’ll need to do.
- Monitor your accounts. Banking and cryptocurrency information is a prime target for these information stealers, so check your accounts and monitor them closely.
- Change all your passwords starting with the important ones, and if you’re not using a password manager already, now might be a good time to get one. It can help you create and store strong passwords.
- Enable multi-factor-authentication (MFA) on all your important accounts.
- Log out of all your important accounts on infected devices. These information stealers are capable of taking over some accounts by stealing cookies, even if you have MFA enabled.
Malwarebytes for Windows and Malwarebytes for Mac can detect the information stealers, and they block the EditProAI websites.
