A previously undocumented Android banking trojan dubbed “FvncBot.” First observed in late 2025, this sophisticated malware disguises itself as a security application from mBank, a major Polish financial institution.
Unlike many recent threats that recycle code from leaked sources like Ermac or Hook, FvncBot appears to be a completely new creation, demonstrating that threat actors are continuing to invest in original development to bypass modern defenses.
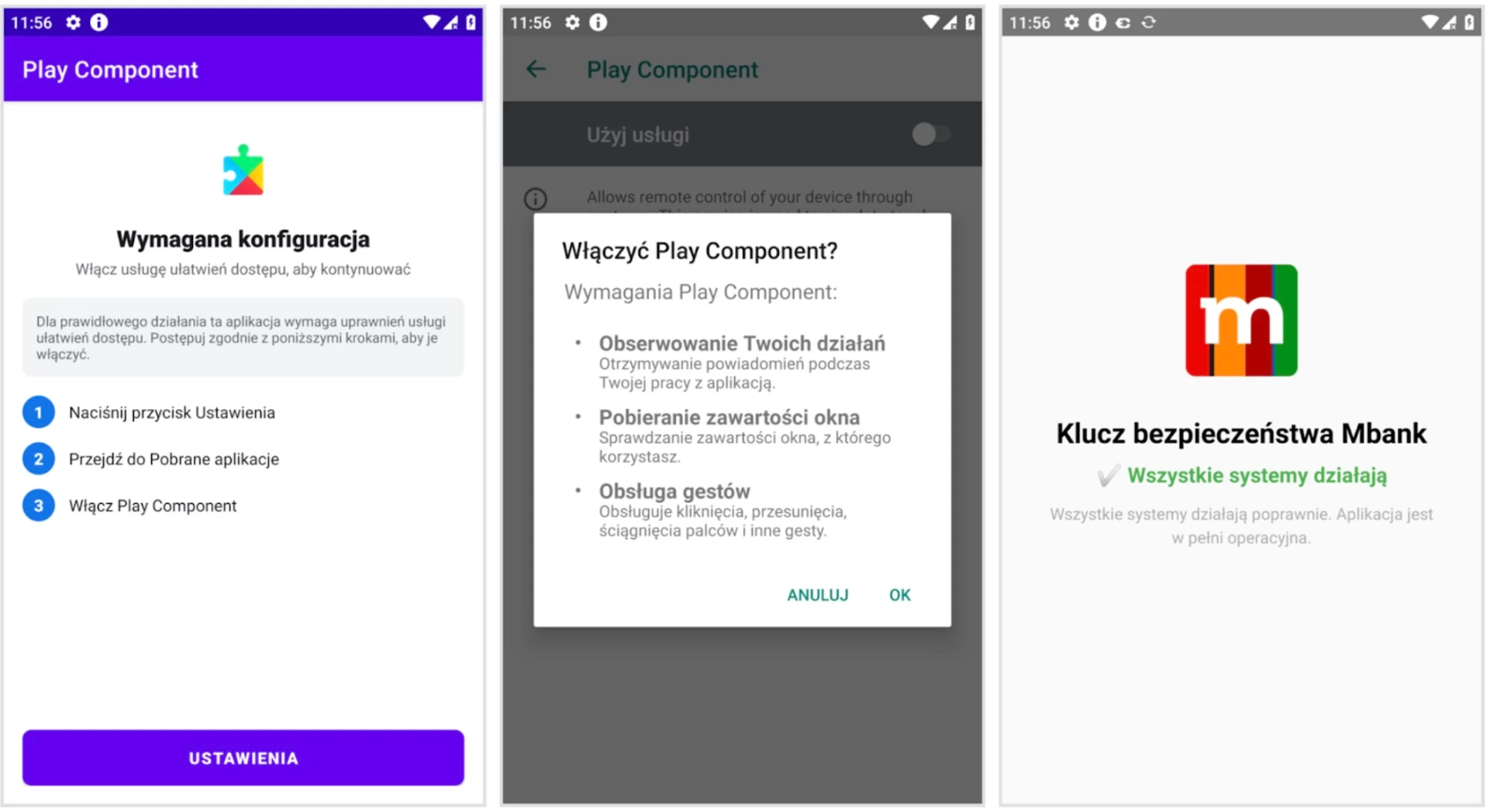
The attack begins with a malicious loader disguised as “Klucz bezpieczeństwa Mbank” (mBank Security Key).
Once the user installs the initial app, it prompts them to download a “Play” component for stability. This action deploys the actual FvncBot payload, which is stored unencrypted in the app’s assets.
Once the loader application was launched, the user was shown information asking to install a “Play” component which ensures security and stability of the app. By clicking the green button “ZAINSTALUJ KOMPONENT” (Eng. Install component), the installation process began.
Both the loader and the payload are obfuscated using the APK0day crypting service, suggesting a potential link between the malware developers and the GoldenCrypt actor.
FvncBot Targets Android Users
On Nov. 25, 2025, Intel 471 researchers observed a malicious application acting as a loader for an unattributed Android banking trojan.
Researchers made appropriate patches in the dynamically loaded Dalvik executable (DEX) file to dump log messages and display them with the logcat tool.
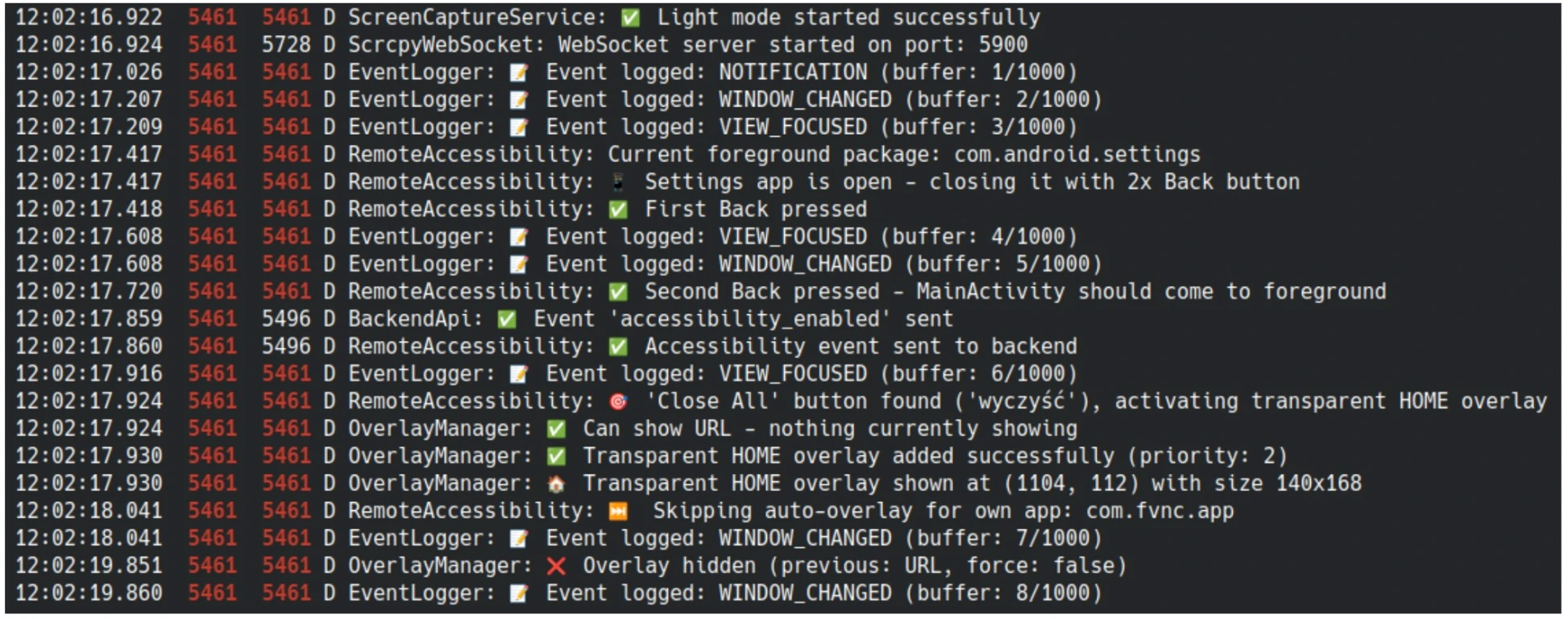
Once installed, FvncBot notes heavily on abusing Android’s Accessibility Services. It coerces the victim into granting these high-level privileges, effectively handing over control of the device. Key capabilities include:
- Keylogging: The malware captures sensitive inputs, such as passwords and OTPs, by sniffing text fields. Data is buffered and exfiltrated in batches.
- Web-Injects: By monitoring for specific target applications, the bot can launch overlay windows that mimic legitimate banking interfaces to steal credentials.
- HVNC (Hidden Virtual Network Computing): A “text mode” feature allows attackers to inspect the UI tree even in apps that block screenshots (using FLAG_SECURE). This allows them to reconstruct the screen remotely without triggering security alerts.
- Screen Streaming: The malware implements H.264 video encoding via the MediaProjection API, allowing for high-efficiency, low-latency live streaming of the victim’s device to the attacker.
Communication Infrastructure
FvncBot utilizes a dual-channel communication structure. Standard data exfiltration occurs via unencrypted HTTP POST requests containing JSON objects.
However, for real-time control, the malware uses Firebase Cloud Messaging (FCM) to receive commands. One such command initiates a WebSocket connection using a Fast Reverse Proxy (FPR) tool embedded in the malware.
This bidirectional connection is crucial for the bot’s remote control features, allowing attackers to perform gestures (swipes, clicks) and navigate the device live.
Currently, the campaign targets Polish users, indicated by the call_pl build identifier. However, the modular nature of the web-injects fetched dynamically from the C2 server means the operators can easily pivot to target other regions or institutions.
The emergence of FvncBot highlights a persistent trend: attackers are successfully masking malware as security tools and leveraging accessibility APIs to circumvent OS-level protections.
Security professionals should monitor for indicators associated with this new family, particularly regarding the specific package name com.fvnc.app and traffic to naleymilva.it.com.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.


