Check Point Research has uncovered a sophisticated malware distribution campaign leveraging the YouTube Ghost Network to deploy GachiLoader, a novel, heavily obfuscated Node.js-based loader designed to deliver the Rhadamanthys infostealer to unsuspecting victims.
The campaign, which commenced in December 2024, represents a significant evolution in malware delivery tactics and demonstrates how threat actors continue to adapt their arsenals using non-traditional programming languages and platforms.
The campaign spans over 100 malicious videos distributed across 39 compromised YouTube accounts, accumulating approximately 220,000 views since its inception.
Videos were designed to mimic game cheat advertisements and cracked software offerings, luring viewers into downloading password-protected archives containing the malware payload.
Following Check Point’s responsible disclosure, most videos have been removed from the platform, though researchers expect new uploads to emerge on newly compromised accounts.
Technical Architecture
GachiLoader is bundled into self-contained executables ranging from 60 to 90 megabytes using the nexe packer, which compiles Node.js applications into standalone binaries complete with integrated runtime environments.
GachiLoader first obtains information about the host it is running on, such as antivirus products and the OS version, and sends them via a POST request to the /log endpoint of its C2 (Command and Control) addresses.
This substantial file size avoids raising suspicion, as victims expect legitimate software packages. The JavaScript source code remains heavily obfuscated, complicating manual analysis efforts and enabling the malware to evade detection systems.
To combat the analytical challenges posed by obfuscated Node.js malware, Check Point Research developed an open-source Node.js tracer tool that dynamically analyzes malware behavior, bypasses anti-analysis mechanisms, and significantly reduces manual deobfuscation efforts. This tool is now available to the security research community.
GachiLoader implements comprehensive anti-analysis capabilities including system resource checks for minimum RAM (4GB) and CPU cores (2 or more), alongside comparisons against sandboxed usernames, hostnames, and analysis tools.
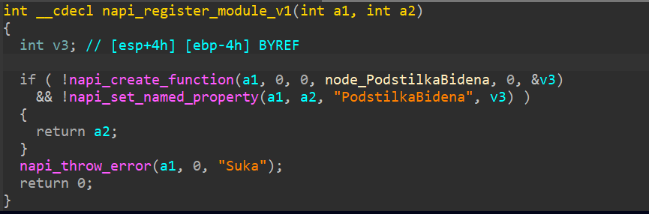
.node files are native addons for Node.js, which are essentially just DLLs that can be called from Node.js code via dlopen. Therefore, they can be used by developers whenever the Node-API does not expose sufficient functionality.
The malware performs PowerShell-based system enumeration via Windows Management Instrumentation, querying port connectors, disk drive manufacturers, and video controllers to identify virtual machine environments.
When sandbox detection occurs, the malware enters an endless loop sending HTTP GET requests to benign websites, effectively stalling execution.
For defense evasion, GachiLoader terminates Windows Defender SecHealthUI process and adds broad exclusions for system directories and file extensions, specifically targeting C:Users, C:ProgramData, and C:Windows paths to prevent detection of subsequent payloads.
Dual Payload Delivery Mechanisms
The campaign employs two operational variants. The first variant retrieves payloads from remote command-and-control servers via authenticated HTTP requests using unique X-Secret headers.
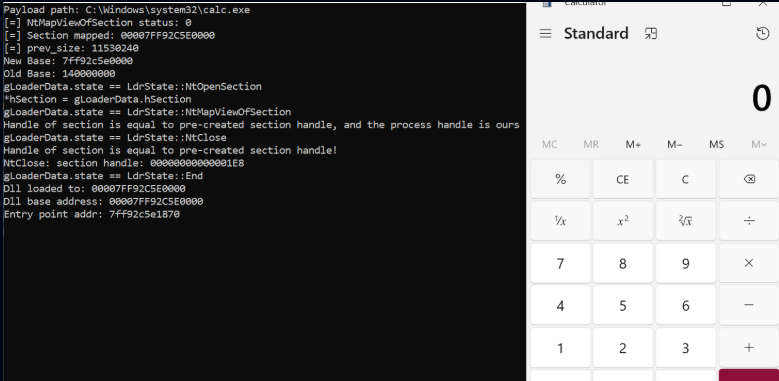
Completely unrelated to this campaign, we found a file with an original filename of HookPE.exe, which is a 64-bit PoC version of the technique with debug prints that uses the technique to load calc.exe into memory.
The second variant deploys Kidkadi, an additional loader implementing a previously undocumented PE injection technique called Vectored Overloading.
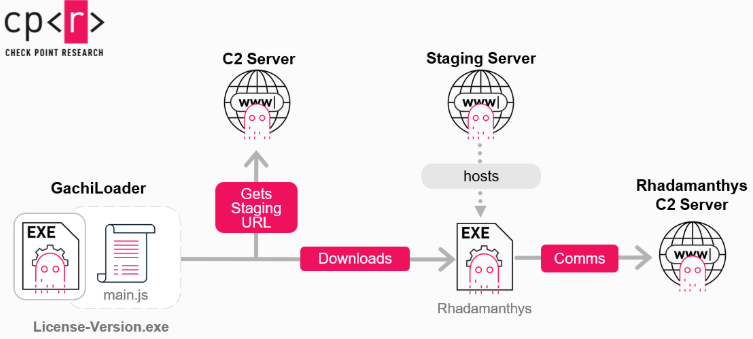
All analyzed samples ultimately delivered Rhadamanthys infostealer, a credential-stealing malware designed to exfiltrate user information to malicious command-and-control infrastructure.
This technique abuses Vectored Exception Handlers to manipulate Windows loader behavior, replacing legitimate DLL sections with malicious payloads using hardware breakpoints on kernel functions like NtOpenSection and NtMapViewOfSection.
GachiLoader samples contain multiple redundant C2 addresses for operational resilience. Final payloads are downloaded as random-named executables mimicking legitimate software such as KeePass.exe or GoogleDrive.exe, protected with commercial packers including VMProtect and Themida.
Samples demonstrate rapid deployment cycles with frequent payload and C2 rotation strategies.
The campaign illustrates the persistent threat landscape targeting users seeking unauthorized software through unofficial distribution channels, reinforcing the necessity for endpoint security solutions and user awareness regarding the dangers of downloading cracked software.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
