In a recent report by the Government Accountability Office (GAO), the Cybersecurity and Infrastructure Security Agency (CISA) has been urged to enhance its workforce capabilities to protect better operational technology (OT) systems critical to the nation’s infrastructure.
The GAO’s findings highlight significant challenges and offer recommendations to bolster the defense against cyber threats.
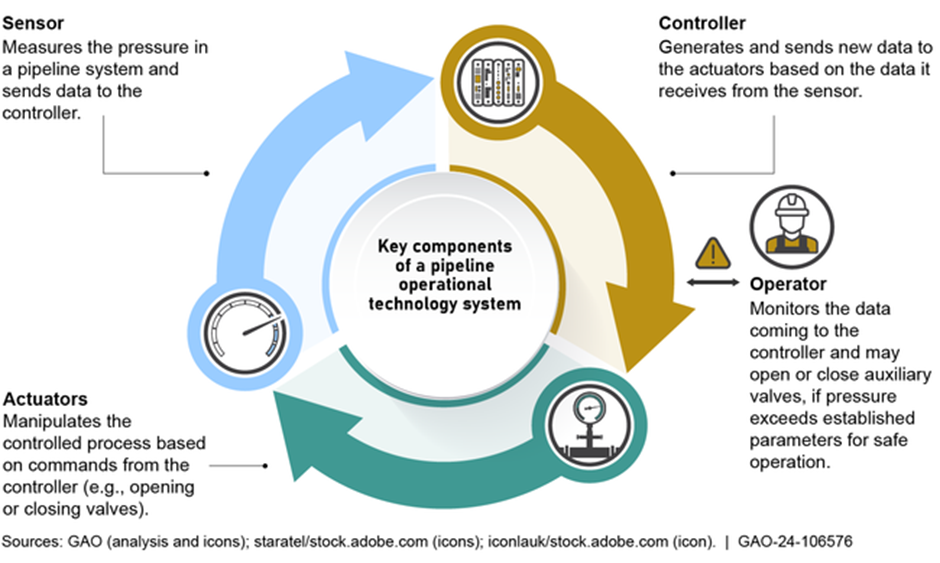
Operational technology systems, encompassing sensors, controllers, and actuators, play a pivotal role in managing the processes and production of critical infrastructure, such as oil pipelines and electric power generation.
These systems are increasingly targeted by cyberattacks, posing a substantial threat to national security and public safety.

Challenges in CISA’s Current Approach
Despite CISA’s efforts to provide technical assistance to infrastructure owners and operators, several challenges hinder its effectiveness.
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data
If you want to test all these features now with completely free access to the sandbox:
The GAO report, based on feedback from 13 selected nonfederal entities, reveals two main issues:
- Delayed Vulnerability Disclosures: Entities reported experiences where vulnerabilities took over a year from initial report to public disclosure, significantly delaying remediation efforts.
- Insufficient Skilled Staff: CISA’s limited staff with the necessary OT skills struggles to respond to significant attacks, impacting its ability to offer timely and practical support.
Recommendations for Improvement
The GAO’s analysis suggests that CISA’s approach to addressing OT risks falls short in several areas, including customer service measurement and workforce planning.
To enhance its services, the GAO recommends:
- Measuring Customer Service: CISA should evaluate the effectiveness of its OT products and services and use feedback to drive improvements.
- Effective Workforce Planning: Developing OT competency and staffing requirements, assessing gaps, and strategizing to fill these gaps are crucial steps for CISA.

The report also identifies challenges in CISA’s collaboration with other agencies responsible for protecting critical infrastructure.
Ineffective information sharing and a lack of clear processes for collaboration were noted as significant barriers.
Adopting leading collaboration practices and developing clear guidance and policies for cooperation are essential steps recommended by the GAO.
Moving Forward
The Department of Homeland Security (DHS), under which CISA operates, has concurred with the GAO’s recommendations and outlined plans to address these challenges.
Implementing these recommendations is crucial for strengthening the nation’s defense against the growing threat to operational technology systems.
This article aims to shed light on the critical findings and recommendations of the GAO’s report, emphasizing the importance of enhancing CISA’s capabilities to protect the nation’s operational technology infrastructure.
As cyber threats evolve, so too must our defenses, with skilled personnel and effective collaboration at the forefront of this ongoing battle.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter
