Germany’s domestic intelligence agency is warning of suspected state-sponsored threat actors targeting high-ranking individuals in phishing attacks via messaging apps like Signal.
The attacks combine social engineering with legitimate features to steal data from politicians, military officers, diplomats, and investigative journalists in Germany and across Europe.
The security advisory is based on intelligence collected by the Federal Office for the Protection of the Constitution (BfV) and the Federal Office for Information Security (BSI).

“A defining characteristic of this attack campaign is that no malware is used, nor are technical vulnerabilities in the messaging services exploited,” the two agencies inform.
According to the advisory, the attackers contact the target directly, pretending to be from the support team of the messaging service or the support chatbot.
“The goal is to covertly gain access to one-to-one and group chats as well as contact lists of the affected individuals,”
There are two versions of these attacks: one that performs a full account takeover, and one that pairs the account with the attacker’s device to monitor chat activity.
In the first variant, the attackers impersonate Signal’s support service and send a fake security warning to create a sense of urgency.
The target is then tricked into sharing their Signal PIN or an SMS verification code, which allows the attackers to register the account to a device they control. Then they hijack the account and lock out the victim.
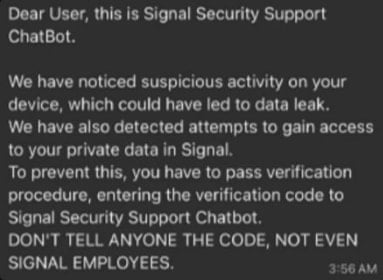
Source: BSI
In the second case, the attacker uses a plausible ruse to convince the target to scan a QR code. This abuses Signal’s legitimate linked-device feature that allows adding the account to multiple devices (computer, tablet, phone).
The result is that the victim account is paired with a device controlled by the bad actor, who gets access chats and contacts without raising any flags.
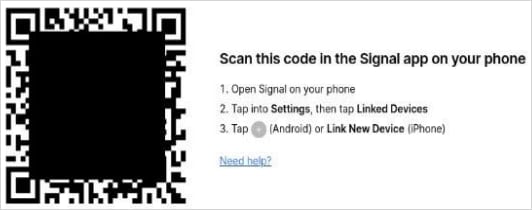
Source: BSI
Although Signal lists all devices attached to the account under Settings > Linked devices, users rarely check it.
Such attacks were observed to occur on Signal, but the bulletin warns that WhatsApp also supports similar functionality and could be abused in the same way.
Last year, Google threat researchers reported that the QR code pairing technique was employed by Russian state-aligned threat groups such as Sandworm.
Ukraine’s Computer Emergency Response Team (CERT-UA) also attributed similar attacks to Russian hackers, targeting WhatsApp accounts.
However, multiple threat actors, including cybercriminals, have since adopted the technique in campaigns like GhostPairing to hijack accounts for scams and fraud.
The German authorities suggest that users avoid replying to Signal messages from alleged support accounts, as the messaging platform never contacts users directly.
Instead, recipients of these messages are recommended to block and report these accounts.
As an extra security step, Signal users can enable the ‘Registration Lock’ option under Settings > Account. Once active, Signal will ask for a PIN you set whenever someone tries to register your phone number with the application.
Without the PIN code, the Signal account registration on another device fails. Since the code is essential for registration, losing it can result in losing access to the account.
It is also strongly recommended that users regularly review the list of devices with access to your Signal account under Settings → Linked devices, and remove unrecognized devices.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.




