A new Android spyware campaign that uses romance scams and fake chat profiles to spy on users in Pakistan. The malicious app, named GhostChat and detected as Android/Spy.GhostChat.A, disguises itself as a dating chat platform but is actually built for data theft and surveillance.
Instead of being listed on Google Play, it is distributed as an APK that users install manually after enabling installation from unknown sources, making it easier for attackers to bypass normal app-store checks.
GhostChat copies the icon of a legitimate app called “Dating Apps without payment” to appear trustworthy, but it does not offer genuine dating features.
Once launched, the app immediately requests multiple permissions and shows a login screen where victims must enter a username and password.
However, these credentials are hardcoded in the app (username “chat”, password “12345”) and are never sent to a remote server. This indicates that the attacker likely distributes both the APK and the login details together as part of a controlled, targeted operation.
ESET researchers have uncovered an Android spyware campaign leveraging romance scam tactics to target individuals in Pakistan.
After logging in, the victim sees 14 female profiles, each with a photo, name, and age. All profiles appear as locked, and tapping any of them prompts the user to enter an unlock code. These codes are also hardcoded inside the app and not verified online.
How the App Locks Devices
This design creates the illusion of “exclusive access,” where the attacker can share specific codes with selected victims to make the scam feel more personal and private.
All profiles are marked as Locked, and tapping on one of them prompts the victim to enter an unlock code.
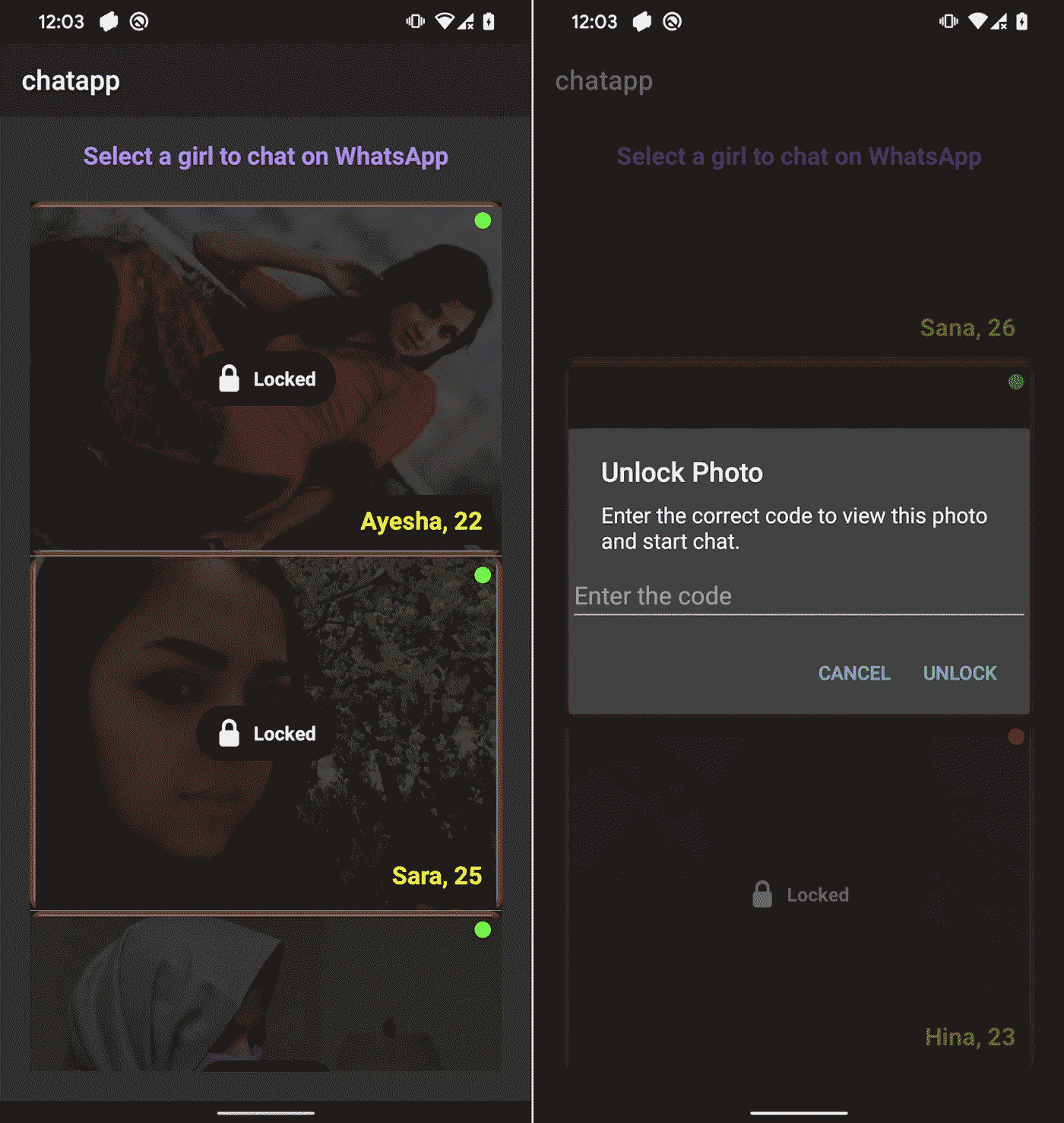
Each profile is linked to a WhatsApp number with a Pakistani (+92) country code, further reinforcing the impression that the “girls” are real and local.
Once the correct code is entered, GhostChat simply redirects the victim to WhatsApp to start a conversation with the associated number, presumably controlled by the threat actor.
While the victim believes they are chatting with a romantic interest, the spyware is already active in the background.
Even before login, GhostChat silently connects to its command-and-control (C&C) server, exfiltrating the device ID, contact list, and files stored on the device, including images, PDFs, and Office documents.
It also sets up continuous monitoring, watching for new images and scanning for new documents every five minutes to upload them automatically.
ESET’s investigation shows that GhostChat is part of a broader espionage operation that extends beyond Android.
The same C&C infrastructure is linked to malicious batch scripts and DLL files designed to infect Windows systems.
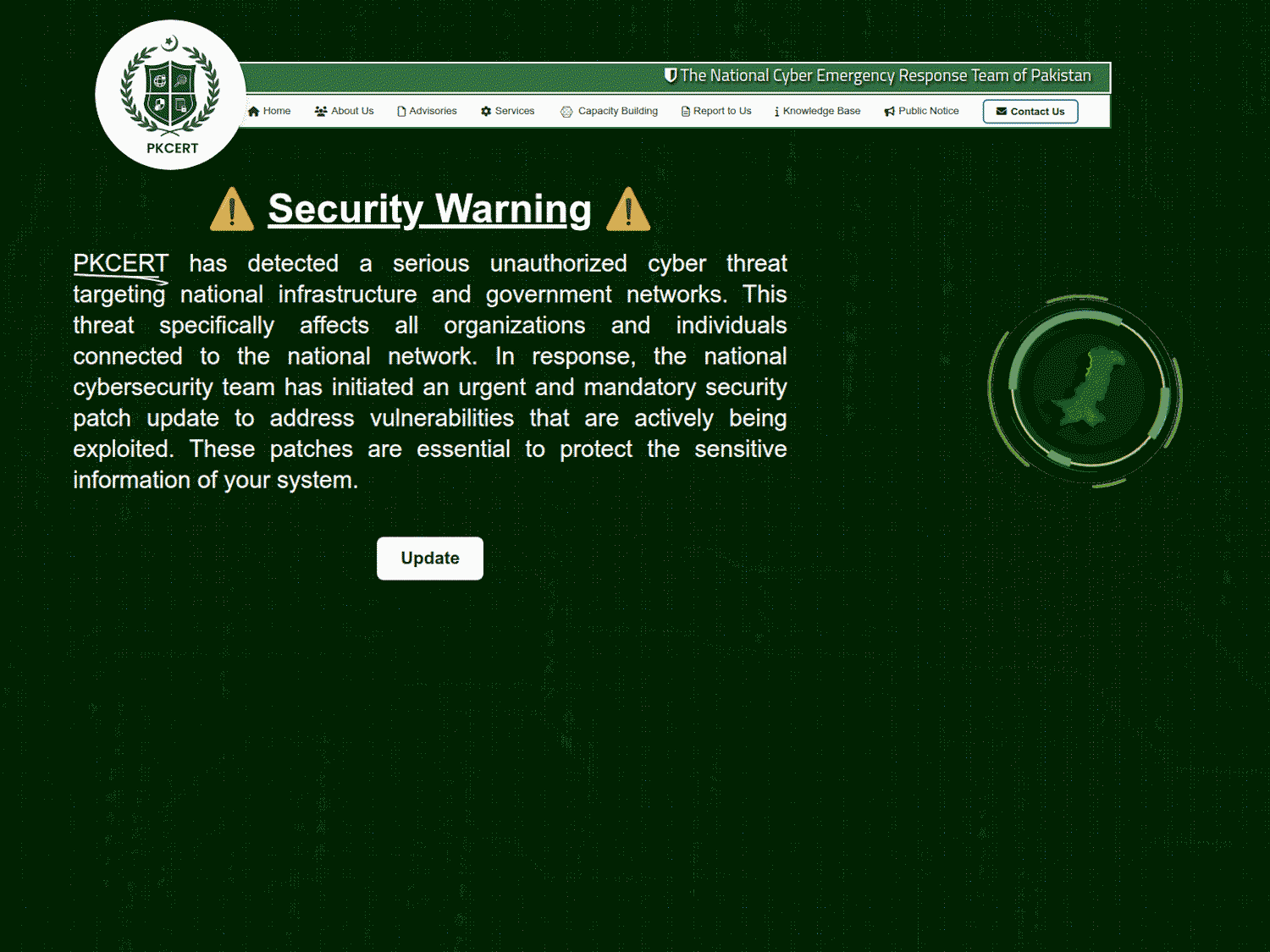
In one case, a ClickFix-style attack used a fake website impersonating Pakistan’s Computer Emergency Response Team (PKCERT) to display a bogus critical alert and trick users into following “update” instructions.
Passcode Phishing Tactics
These steps led to downloading and running a DLL payload capable of remote code execution via base64-encoded PowerShell commands, giving attackers flexible control over infected machines.
The attackers also abused WhatsApp’s link-to-device feature in a separate campaign dubbed GhostPairing. A fake website posing as a Pakistan Ministry of Defence channel lured users into scanning a QR code to “join” a community.
In reality, the QR code linked the victim’s WhatsApp to the attacker’s device, granting them full visibility over messages and contacts until the session was revoked.
This method mirrors past operations where threat actors secretly linked messaging accounts to spy on communications without installing traditional malware.
Although the campaign seems focused on users in Pakistan, ESET has not yet attributed it to a known group. GhostChat has never been available on Google Play, and Google Play Protect now detects known versions of the spyware by default.
Users are strongly advised to avoid installing apps from unknown sources, be skeptical of unsolicited APKs and “exclusive” chat offers, and regularly review linked devices in WhatsApp settings to detect suspicious access.
IOCs
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| B15B1F3F2227EBA4B69C85BDB638DF34B9D30B6A | Live Chat.apk | Android/Spy.GhostChat.A | Android GhostChat spyware. |
| 8B103D0AA37E5297143E21949471FD4F6B2ECBAA | file.dll | Win64/Agent.HEM | Windows payload that executes PowerShell commands from the C&C. |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



