The compromise of GitHub Action tj-actions/changed-files has impacted only a small percentage of the 23,000 projects using it, with it estimated that only 218 repositories exposed secrets due to the supply chain attack.
Despite the small number, the potential security repercussions are still significant as some repositories are very popular and could be used in further supply chain attacks.
That said, owners of exposed repositories must take immediate action to rotate their secrets before attackers get the chance to exploit the leakage.
GitHub supply chain attack
GitHub Action’ tj-actions/changed-files’ was compromised by attackers who added a malicious commit on March 14, 2025, to dump CI/CD secrets from the Runner Worker process to the repository.
If workflow logs were set to be publicly accessible, those secrets could be accessed and read by anyone.
Subsequent investigation showed that the attack was likely made possible via another supply chain attack targeting the “reviewdog/action-setup@v1” GitHub Action.
That breach may have compromised a GitHub personal access token (PAT) used by a bot that had the privilege to perform changes on ‘tj-actions/changed-files.’
Small percentage exposed
According to data shared by Endor Labs that monitored the exposure of secrets resulting from said supply chain attack, the impact of the incident appears to be limited yet still significant.
During the timeframe of the exposure, between March 14, 04:00 PM UTC, and March 15, 02:00 PM UTC, 5,416 repositories across 4,072 distinct organizations referenced the targeted GitHub Action.
Endor reports that some repositories have over 350,000 stars and 63,000 forks, so their compromise could impact many users.
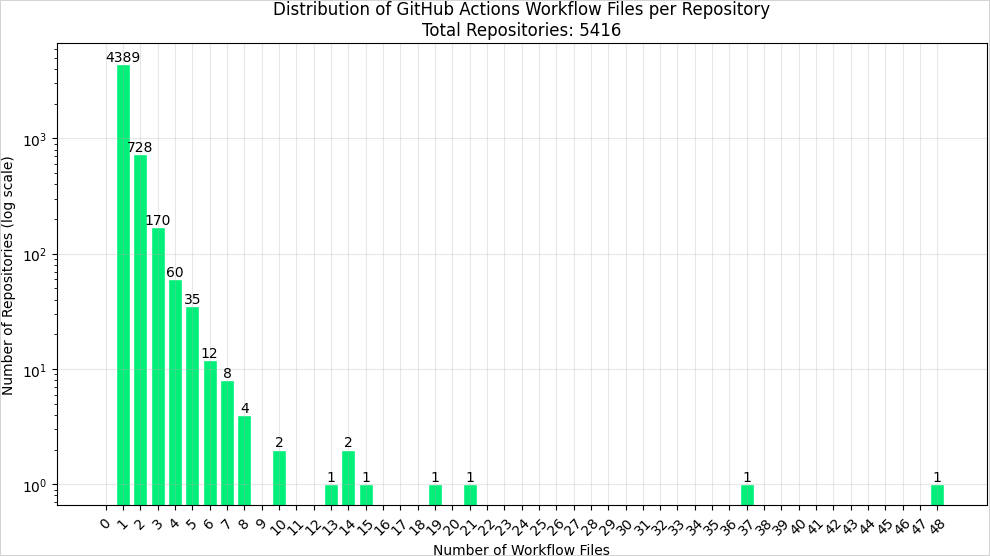
Source: Endor Labs
Out of the 5,416 repositories referencing the GitHub Action, 614 ran the respective workflow in the given timeframe, many of those multiple times as well.
Of those 614, Endor says 218 actually printed secrets to the console log, with the rest being protected by following ‘best-practice recommendations’ that acted as a failsafe to prevent the exposure of secrets.
“Having executed the action does not necessarily mean that any credentials were printed to the console log,” explains Endor.
“Some repositories followed best-practice recommendations and referenced the commit SHA instead of a mutable tag.”
“Others were run before the attacker tampered with all of the version tags such that they point to the malicious commit.”
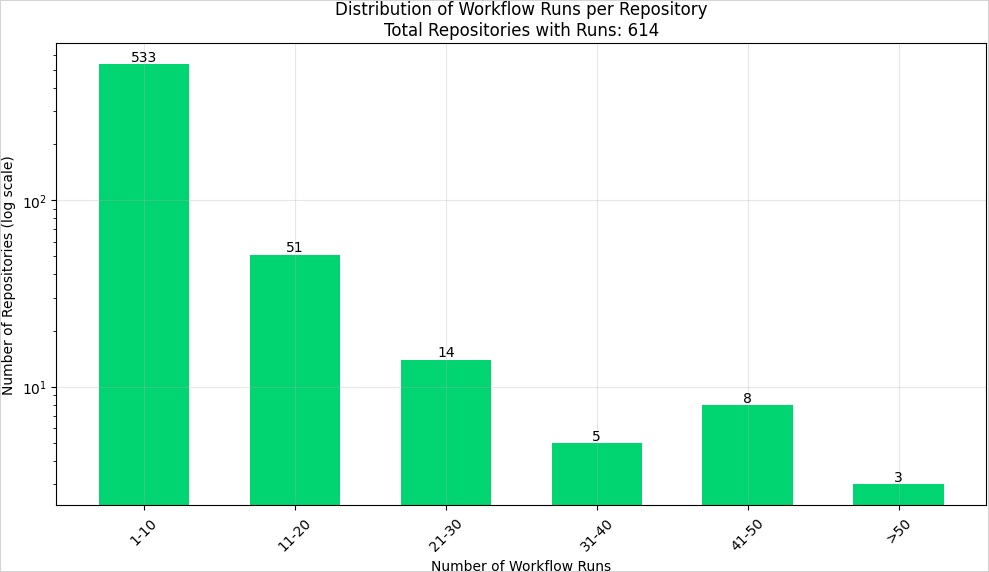
Source: Endor Labs
In most cases, the exposed secrets were GitHub install access tokens, which Endor says expire within 24 hours, leaving attackers only a limited exploitation window.
In some cases, though, credentials for DockerHub, npm, and AWS were leaked, which poses a higher security risk.
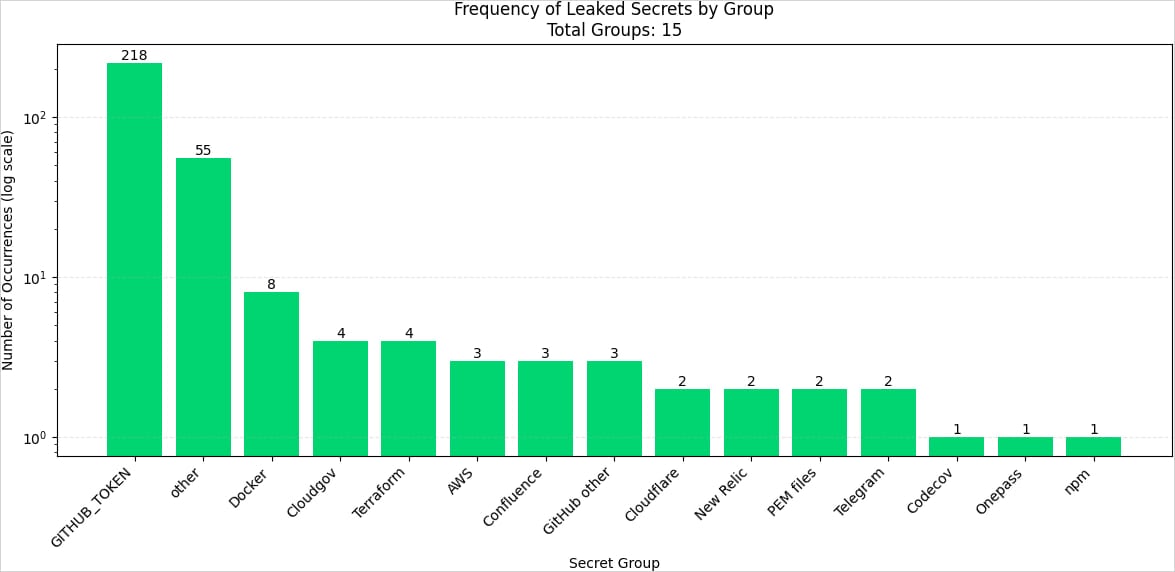
Source: Endor Labs
There are still questions about whether the initial Reviewdog breach led to other compromises beyond tj-actions and if any of the 218 projects exposed by the tj-actions attack also suffered a compromise.
Those using GitHub Actions are strongly recommended to review GitHub’s security hardening advice and restrict access to files and folders that could expose sensitive information.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
