A malware campaign dubbed GitVenom uses hundreds of GitHub repositories to trick users into downloading info-stealers, remote access trojans (RATs), and clipboard hijackers to steal crypto and credentials.
According to Kaspersky, GitVenom has been active for at least two years, targeting users globally but with an elevated focus on Russia, Brazil, and Turkey.
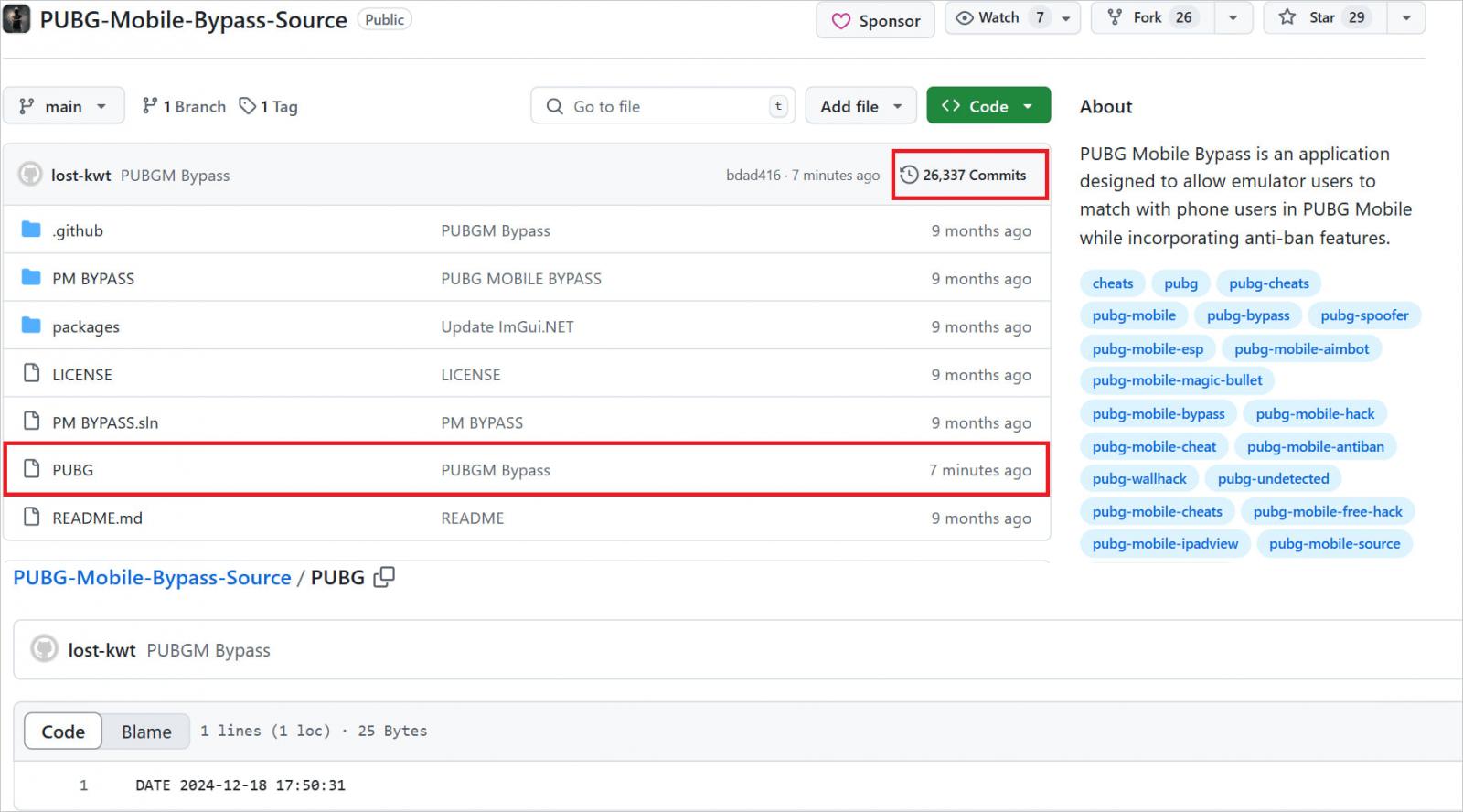
“Over the course of the GitVenom campaign, the threat actors behind it have created hundreds of repositories on GitHub that contain fake projects with malicious code – for example, an automation instrument for interacting with Instagram accounts, a Telegram bot allowing to manage Bitcoin wallets, and a hacking tool for the video game Valorant,” describes Kaspersky’s Georgy Kucherin.
Source: Kaspersky
The researcher explains that the fake repositories are crafted with care, featuring details and appropriately written readme files, likely with the help of AI tools.
Moreover, the threat actors employ tricks to artificially inflate the number of commits submitted to those repositories, creating a fake image of high activity and increasing credibility.
Source: Kaspersky
Malware in GitHub projects
Kaspersky’s analysis of multiple repositories supporting the GitVenom campaign revealed that the malicious code injected into the projects is written in various languages, including Python, JavaScript, C, C++, and C#.
Different languages are believed to be used to evade detection by specific code-reviewing tools or methods.
Once the victim executes the payload, the injected code downloads the second stage from an attacker-controlled GitHub repository.
Kaspersky found the following tools used in GitVenom:
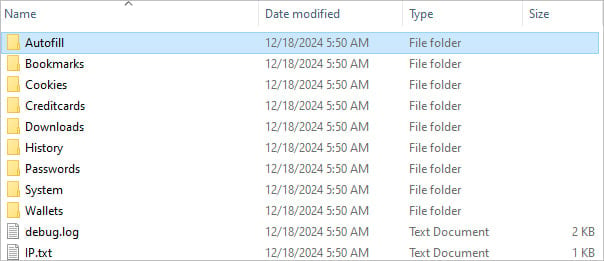
- Node.js stealer – Infostealer that targets saved credentials, cryptocurrency wallet information, and browsing history. It compresses the data into a .7z archive and exfiltrates it via Telegram.
- AsyncRAT – Open-source RAT allowing remote control, keylogging, screen capturing, file manipulation, and command execution.
- Quasar backdoor – Open-source RAT with capabilities similar to those of AsyncRAT.
- Clipboard hijacker – Malware that monitors the victim’s clipboard for cryptocurrency wallet addresses and replaces any with an attacker-controlled address, redirecting funds to the hacker.
The report highlights one case from November 2024 when the attacker’s Bitcoin wallet received 5 BTC, valued at half a million USD.
Source: Kaspersky
Staying safe from this campaign
Although malware hiding in GitHub repositories under the guise of regular software or even PoC exploits isn’t new, GitVenom’s duration and size prove that legitimate platform abuse continues to be very effective.
It is crucial to thoroughly vet a project before using any of its files by inspecting repository contents, scanning files with antivirus tools, and executing downloaded files in an isolated environment.
Red flags include obfuscated code, unusual automated commits, and excessively detailed Readme files that appear AI-generated.
