A sophisticated modular botnet known as GoBruteforcer is actively targeting Linux servers worldwide, with researchers estimating that more than 50,000 internet-facing servers remain vulnerable to these coordinated attacks.
The threat, which has evolved significantly since its initial discovery in 2023, poses a growing danger to organizations that rely on exposed database and file-transfer services.
GoBruteforcer, also referred to as GoBrut, systematically brute-forces user passwords for critical services, including FTP, MySQL, PostgreSQL, and phpMyAdmin, on Linux servers.
The botnet operates through a sophisticated infection chain involving web shells, downloaders, IRC bots, and bruteforcer modules that work in concert to compromise vulnerable systems.
The attack surface is substantial. Recent data from Shodan reveals approximately 5.7 million FTP servers, 2.23 million MySQL servers, and 560,000 PostgreSQL servers are publicly exposed to the internet on their default ports.
These services, combined with tens of thousands of phpMyAdmin panels, form the primary hunting ground for GoBruteforcer operators.
AI-Generated Configurations
Two critical factors drive the current wave of GoBruteforcer campaigns. First, the mass adoption of AI-generated server deployment examples has inadvertently propagated common usernames and weak default credentials across production environments.
When researchers tested mainstream large language models for MySQL server Docker deployment instructions, both produced near-identical configuration snippets featuring standard username patterns like “appuser” and “myuser” – the exact credentials GoBruteforcer actively exploits.
Second, legacy web server software stacks such as XAMPP continue powering numerous websites despite shipping with preinstalled FTP servers and default credentials that essentially function as backdoors waiting to be exploited.
Check Point Research observed a targeted GoBruteforcer campaign specifically attacking databases of cryptocurrency and blockchain projects.
On one compromised host, investigators recovered Go-based tools including a TRON balance scanner and token-sweep utilities for TRON and Binance Smart Chain, alongside a file containing approximately 23,000 TRON addresses.
As a result, utilities such as System Monitor display that value instead of the real executable name a behavior that helps the binary blend in with legitimate system processes:
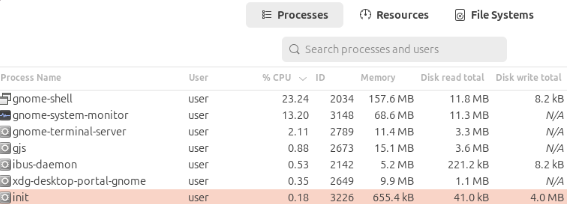
On-chain transaction analysis confirmed that at least some of these financially motivated attacks successfully drained funds from victim wallets.
Enhanced 2025 Variant
The mid-2025 variant demonstrates significant technical advancement over earlier versions.
The IP generation function essentially performs an “infinite dice throw” over the 4 octets until it comes up with an address that is not in any forbidden range.
The updated botnet features a heavily obfuscated IRC bot entirely rewritten in Go, improved persistence mechanisms utilizing cron jobs, sophisticated process-masking techniques that disguise malicious processes as legitimate system services, and dynamic credential lists delivered by command-and-control servers.
The botnet maintains operational resilience through architecture-specific worker pools, with 64-bit systems running approximately 95 concurrent bruteforce threads.
Analysis comparing GoBruteforcer’s credential lists against 10 million leaked passwords revealed a 2.44% overlap rate, translating to approximately 54,600 vulnerable MySQL instances and 13,700 PostgreSQL instances that could accept passwords in the botnet’s arsenal.
This finding aligns with Google’s 2024 Cloud Threat Horizons report, which identified weak or missing credentials as accounting for 47.2% of initial access vectors in compromised cloud environments.
Security professionals urge organizations to audit internet-facing services immediately, implement strong authentication protocols, disable default accounts, and deploy network segmentation to minimize exposure to these persistent brute-force campaigns.
Operators rotate campaign profiles multiple times weekly, cycling between broad spray campaigns using common operational usernames and sector-focused attacks targeting specific industries like cryptocurrency platforms or WordPress installations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
