A sophisticated and widespread smishing campaign originating from China has emerged as a significant threat to users worldwide.
Researchers have attributed the ongoing attack to a group known as the Smishing Triad, which has demonstrated unprecedented scale and complexity through a decentralized infrastructure capable of registering and churning thousands of malicious domains daily.
Since January 2024, security analysts have identified over 194,000 malicious domains linked to this operation, with the campaign actively targeting U.S. residents since April 2024 while rapidly expanding its global reach and victim base.
The attack operates through fraudulent toll violation and package misdelivery notices delivered via SMS, creating artificial urgency to manipulate victims into immediate action.
Over the past six months, the channel has evolved from a dedicated phishing kit marketplace into a highly active community that gathers diverse threat actors within the PhaaS ecosystem.
Attackers impersonate legitimate international services across critical sectors including banking, cryptocurrency platforms, e-commerce, healthcare, law enforcement, and social media.
The social engineering tactics employed have evolved significantly, incorporating personalized information, technical jargon, and realistic phishing pages designed to extract sensitive data such as National Identification Numbers, home addresses, payment details, and login credentials.
Global Scale and Infrastructure Sophistication
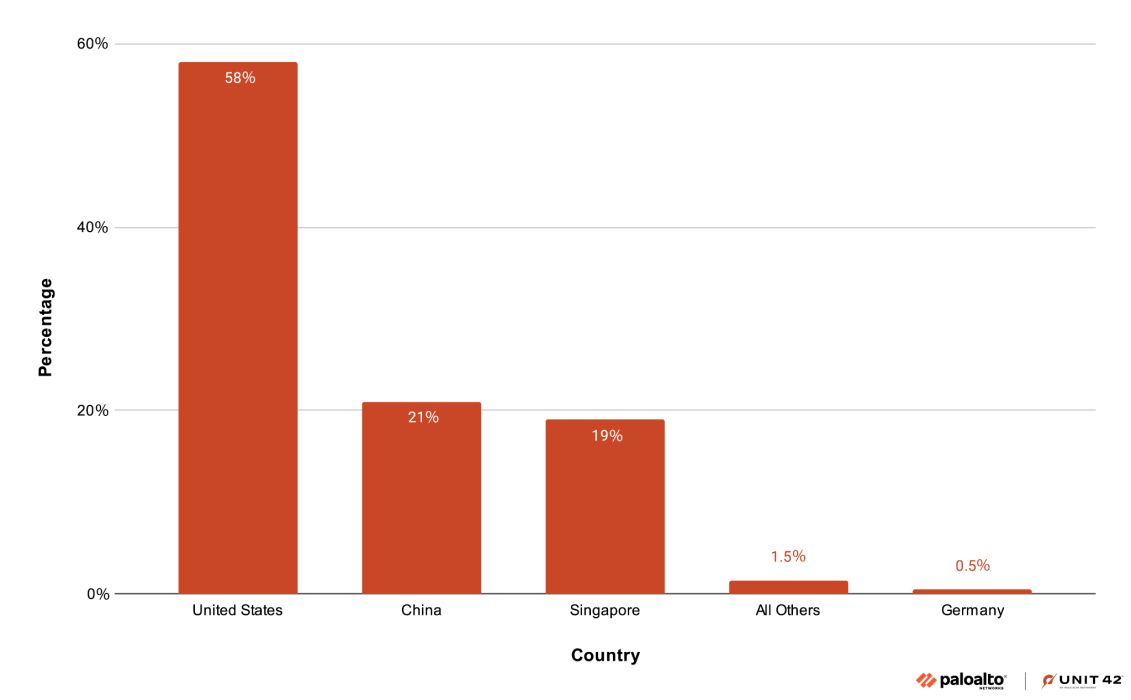
The infrastructure supporting this campaign reveals a highly organized operation. Although domains are registered through a Hong Kong-based registrar and utilize Chinese nameservers, the actual attack infrastructure is primarily hosted on U.S. cloud services, particularly within the Cloudflare network.
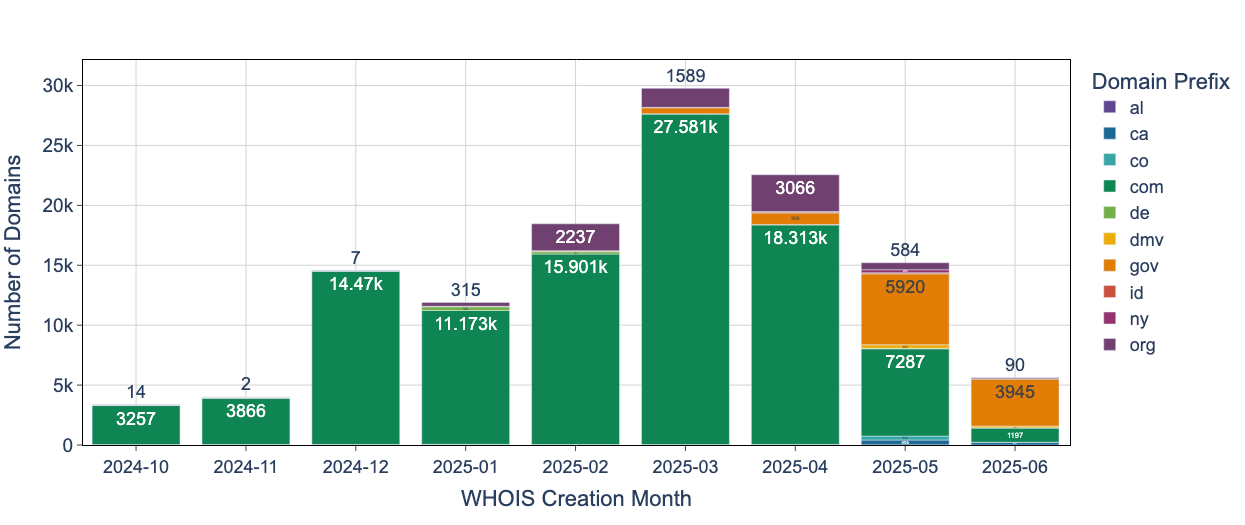
The WHOIS creation dates reveal an interesting shift. We have picked the top 10 most popular domain prefixes in this campaign.

The campaign demonstrates remarkable decentralization, with no single point of control and an ever-evolving array of hosting providers.
Attackers register domains primarily through Dominet Limited, a Hong Kong-based registrar, accounting for approximately 68 percent of identified root domains.
The remaining registrations are distributed across Namesilo and Gname, enabling rapid domain rotation to evade detection and blocking mechanisms.
Domain analysis reveals intentional design patterns aimed at deceiving victims. Many domains follow a hyphenated naming structure with prefixes mimicking legitimate services.
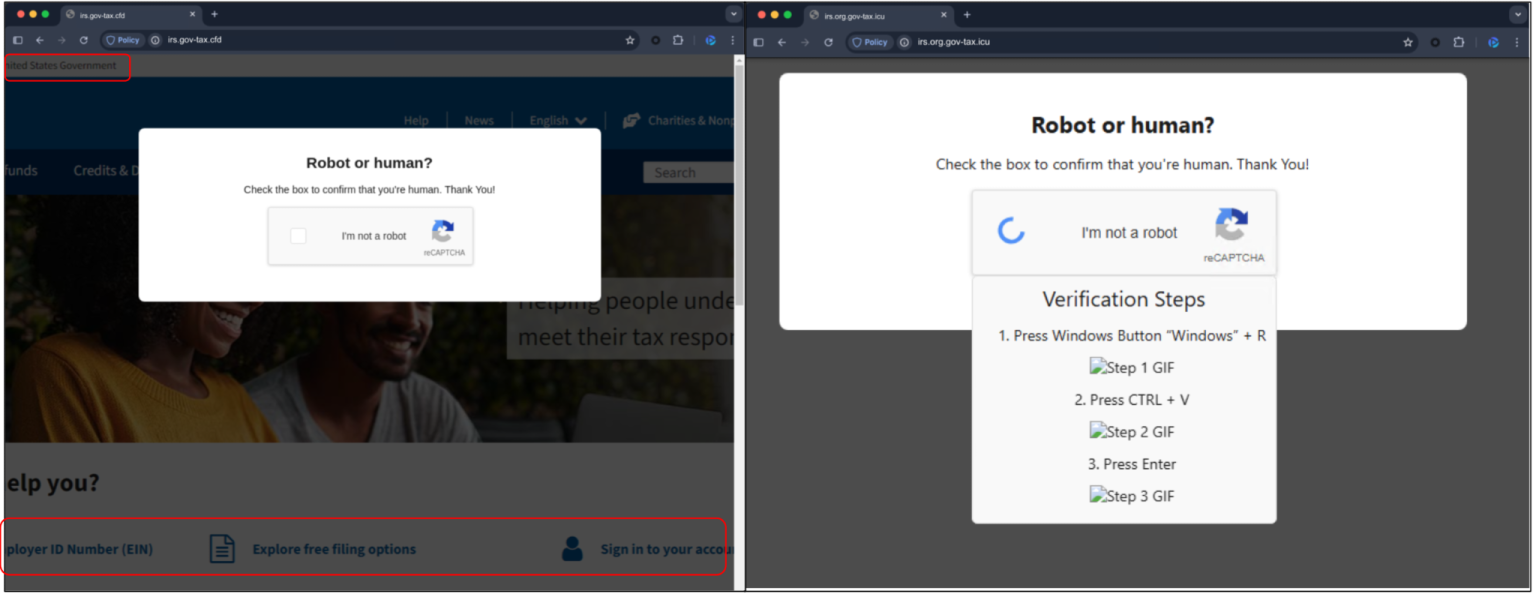
For instance, domains like “irs.gov-addpayment[.]info” are crafted to resemble official government websites during casual inspection.
The most commonly impersonated service is the U.S. Postal Service, with nearly 28,000 dedicated phishing domains, while toll services represent the largest category with approximately 90,000 dedicated FQDNs.
We aggregated the number of DNS responses per domain and geolocated the IP addresses in these responses.

Most registered domains demonstrate remarkably short lifespans, with approximately 29 percent remaining active for two days or less, and over 82 percent expiring within two weeks.
Phishing-as-a-Service Ecosystem
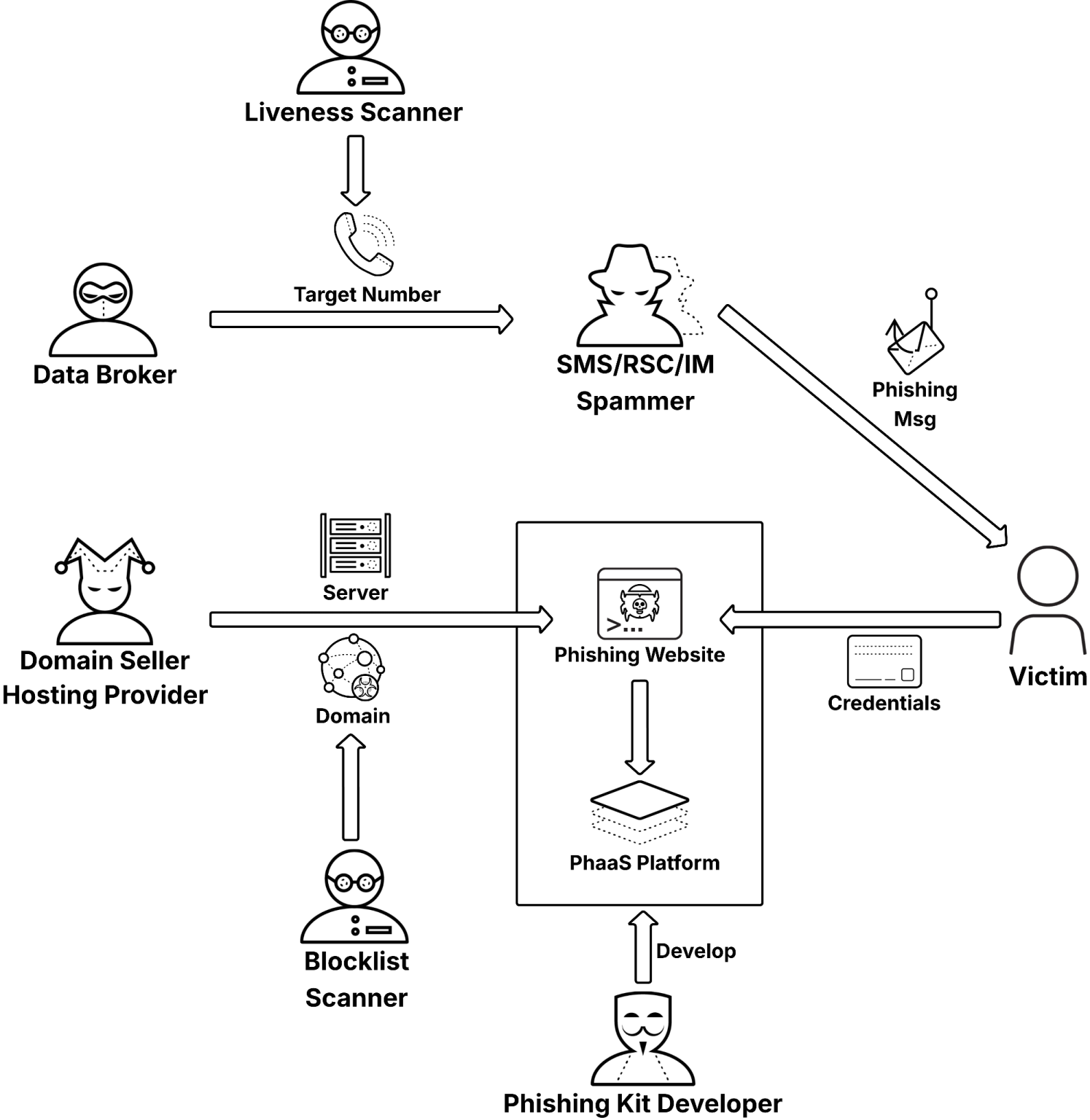
The operation functions as a sophisticated phishing-as-a-service ecosystem, with specialized threat actors managing different stages of the attack supply chain.
The page contains a fake CAPTCHA page that is designed to manipulate users into executing malicious scripts on their machine.

Upstream participants include data brokers selling target phone numbers, domain sellers registering disposable domains, and hosting providers supplying infrastructure.
Midstream operations involve phishing kit developers creating phishing websites and maintaining dashboards for harvesting stolen credentials.
Downstream participants handle SMS and RCS delivery at scale, while support specialists verify active phone numbers and monitor blocklist effectiveness. This compartmentalization enables efficient scaling and reduces individual operator exposure.
Research indicates the campaign continuously evolves its targeting strategies. Until May 2025, domain registrations favored “com-” prefixes, but recent months show significant increases in “gov-” domain registrations, suggesting tactical adaptation to better impersonate government services.
Messages originate from phone numbers beginning with Philippine country codes, though U.S. phone numbers are increasingly utilized, complicating attribution and victim awareness.
Security experts recommend exercising extreme caution with unsolicited messages from unknown senders. Users should independently verify any requests demanding urgent action through official service provider websites or applications, avoiding clicking links or calling numbers included in suspicious messages.
This campaign’s global scope, complex infrastructure, and realistic phishing pages demonstrate the substantial threat posed by well-resourced, organized phishing operations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
