In February 2023, JPCERT/CC confirmed malware attacks on routers in Japan, specifically targeting Linux routers with a new Golang RAT known as GobRAT.
The attacker exploits publicly accessible routers WEBUIs, leveraging potential vulnerabilities to infect them with the GobRAT ultimately.
After an internet-exposed router is compromised, a loader script is deployed to deliver GobRAT, which disguises itself as the Apache daemon process (apached) to avoid being detected.
How the Attack Chain Works
The attacker begins by targeting a publicly accessible router with an open WEBUI, exploits vulnerabilities through script execution, and ultimately spoils the GobRAT.
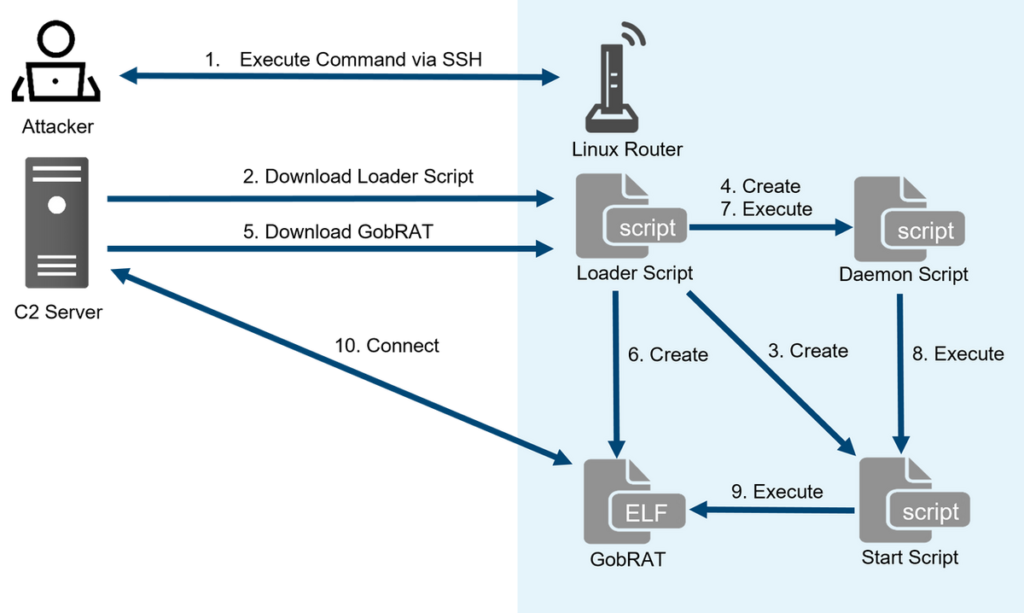
The Loader Script is a multifunctional loader, encompassing tasks like script generation, GobRAT downloading and containing a hard-coded SSH public key for the assumed backdoor.
Loader Script utilizes crontab to ensure the persistence of the file path for Start Script, while GobRAT lacks this capability, highlighting the functions of the Loader Script.
Here below, we have mentioned the functions of Loader Script:-
- Disable Firewall function
- Download GobRAT for the target machine’s architecture
- Create a Start Script and make it persistent
- Create and run Daemon Script.
- Register an SSH public key in /root/.ssh/authorized_keys
The Start Script code, responsible for executing GobRAT, distinguishes itself by recording the startup time in a file called restart[.]log, while also running GobRAT under the guise of a legitimate process named apached.
The Daemon Script monitors the status of the Start Script every 20 seconds. It initiates it if it is not running, indicating its potential role in handling unexpected terminations of the Start Script.
Here below, we have mentioned all the checks that the GobRAT performs:-
- IP address and MAC address of itself
- Uptime by uptime command
- Network communication status by /proc/net/dev
GobRAT utilizes TLS for data communication with its C2 server, employing a 4-byte data size indicator followed by gob serialized data, which is a Go-specific protocol used for receiving commands and transmitting command execution results.
Commands Executed by Malware
GobRAT, targeting routers, utilizes 22 commands from the C2 server, mainly focused on communication functions like frpc, socks5, and C2 reconfiguration.
Here below we have mentioned all the major commands:-
- Obtain machine Information
- Execute reverse shell
- Read/write files
- Configure new C2 and protocol
- Start socks5
- Execute file in /zone/frpc
- Attempt to login to sshd, Telnet, Redis, MySQL, and PostgreSQL services running on another machine
While apart from this, Lumen Black Lotus Labs recently discovered that HiatusRAT, a malware, has been exploiting business-grade routers to spy on victims in Latin America, Europe, and North America for the past three months.
Common Security Challenges Facing CISOs? – Download Free CISO’s Guide