Google dismantled what is believed to be one of the world’s largest residential proxy networks, taking legal action to seize domains controlling IPIDEA’s infrastructure and removing millions of consumer devices unknowingly enrolled as proxy exit nodes.
The takedown involved platform providers, law enforcement and security firms working to eliminate a service that enabled espionage, cybercrime and information operations at scale.
Residential proxy networks sell access to IP addresses owned by internet service providers and assigned to residential customers. By routing traffic through consumer devices worldwide, attackers mask malicious activity behind legitimate-looking IP addresses, creating significant detection challenges for network defenders.
IPIDEA became notorious for facilitating multiple botnets, with its software development kits playing key roles in device enrollment while proxy software enabled attacker control. This includes the BadBox2.0 botnet Google targeted with legal action last year, plus the more recent Aisuru and Kimwolf botnets.
Also read: Cloudflare Outage or Cyberattack? The Real Reason Behind the Massive Disruption
The scale of abuse proves staggering. During just one week in January this year, Google observed over 550 individual threat groups it tracks using IP addresses associated with IPIDEA exit nodes to obfuscate their activities. These groups originated from China, North Korea, Iran and Russia, conducting activities including access to victim software-as-a-service environments, on-premises infrastructure compromise and password spray attacks.
“While proxy providers may claim ignorance or close these security gaps when notified, enforcement and verification is challenging given intentionally murky ownership structures, reseller agreements, and diversity of applications,” Google’s analysis stated.


Google’s investigation revealed that many ostensibly independent residential proxy brands actually connect to the same actors controlling IPIDEA. The company identified 13 proxy and VPN brands as part of the IPIDEA network, including 360 Proxy, ABC Proxy, Cherry Proxy, Door VPN, IP 2 World, Luna Proxy, PIA S5 Proxy and others.
The same actors control multiple software development kit domains marketed to app developers as monetization tools. These SDKs support Android, Windows, iOS and WebOS platforms, with developers paid per download for embedding the code. Once incorporated into applications, the SDKs transform devices into proxy network exit nodes while providing whatever primary functionality the app advertised.
Google analyzed over 600 Android applications across multiple download sources containing code connecting to IPIDEA command-and-control domains. These apps appeared largely benign—utilities, games and content—but utilized monetization SDKs enabling proxy behavior without clear disclosure to users.
The technical infrastructure operates through a two-tier system. Upon startup, infected devices connect to Tier One domains and send diagnostic information. They receive back a list of Tier Two servers to contact for proxy tasks. The device then polls these Tier Two servers periodically, receiving instructions to proxy traffic to specific domains and establishing dedicated connections to route that traffic.
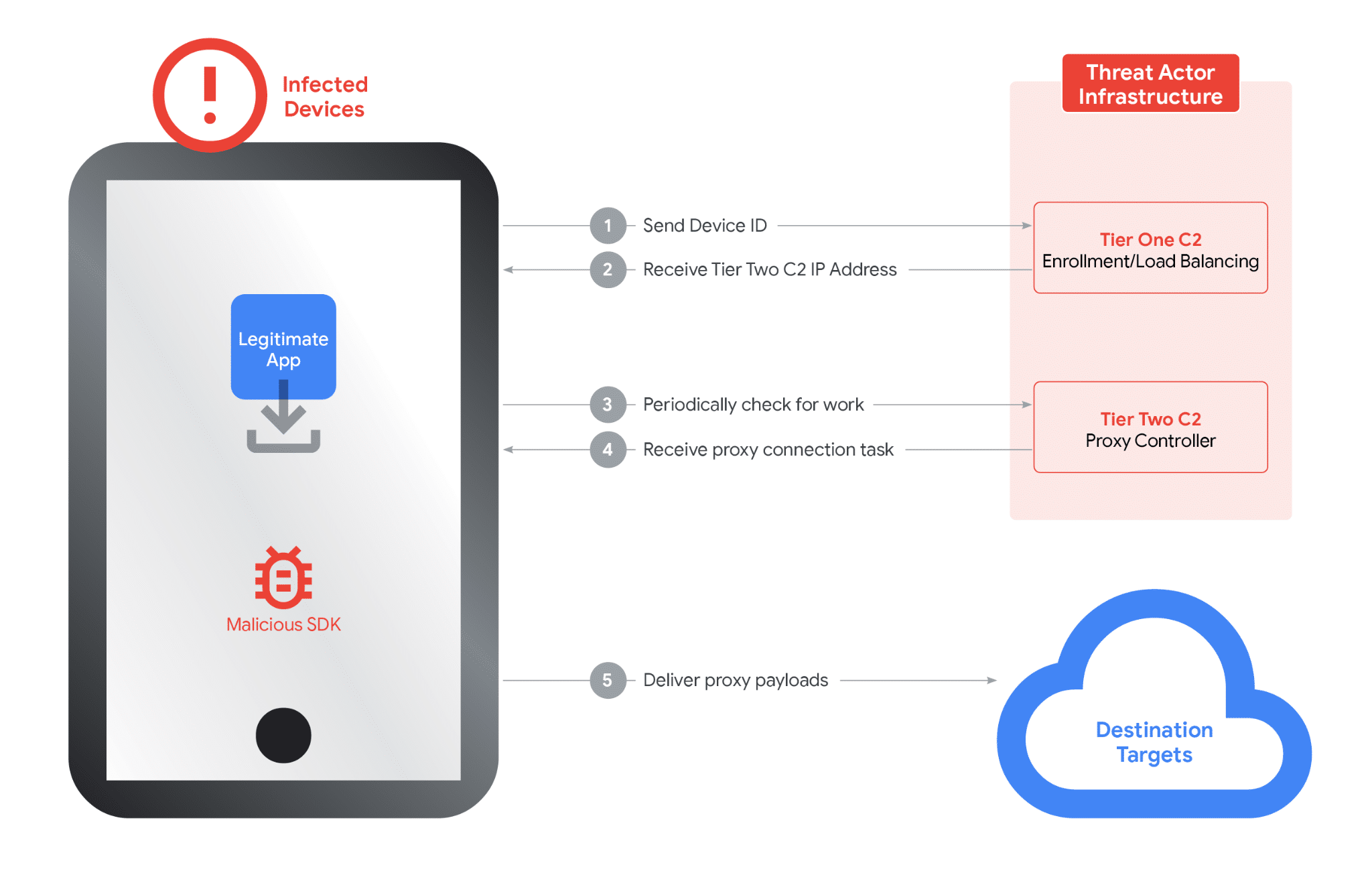

Google identified approximately 7,400 Tier Two servers as of the takedown. The number changes daily, consistent with demand-based scaling. These servers are hosted globally, including in the United States.
Analysis of Windows binaries revealed 3,075 unique file hashes where dynamic analysis recorded DNS requests to at least one Tier One domain. Some posed as legitimate software like OneDriveSync and Windows Update, though IPIDEA actors didn’t directly distribute these trojanized applications.
Residential proxies pose direct risks to consumers whose devices become exit nodes. Users knowingly or unknowingly provide their IP addresses and devices as launchpads for hacking and unauthorized activities, potentially causing providers to flag or block them. Proxy applications also introduce security vulnerabilities to home networks.
When a device becomes an exit node, network traffic the user doesn’t control passes through it. This means attackers can access other devices on the same private network, effectively exposing security vulnerabilities to the internet. Google’s analysis confirmed IPIDEA proxy software not only routed traffic through exit nodes but also sent traffic to devices to compromise them.
Google’s disruption involved three coordinated actions. First, the company took legal action to seize domains controlling devices and proxying traffic through them. Second, Google shared technical intelligence on discovered IPIDEA software development kits with platform providers, law enforcement and research firms to drive ecosystem-wide enforcement.
Third, Google ensured Play Protect, Android’s built-in security system, automatically warns users and removes applications incorporating IPIDEA SDKs while blocking future installation attempts. This protects users on certified Android devices with Google Play services.
Google believes the actions significantly degraded IPIDEA’s proxy network and business operations, reducing available devices by millions. Because proxy operators share device pools through reseller agreements, the disruption likely impacts affiliated entities downstream.
Also read: What Is a Proxy Server? A Complete Guide to Types, Uses, and Benefits
The residential proxy market has become what Google describes as a “gray market” thriving on deception—hijacking consumer bandwidth to provide cover for global espionage and cybercrime. Consumers should exercise extreme caution with applications offering payment for “unused bandwidth” or “internet sharing,” as these represent primary growth vectors for illicit proxy networks.
Google urges users to purchase connected devices only from reputable manufacturers and verify certification. The company’s Android TV website provides up-to-date partner lists, while users can check Play Protect certification status through device settings.
The company calls for proxy accountability and policy reform. While some providers may behave ethically and enroll devices only with clear consumer consent, any claims of “ethical sourcing” must be backed by transparent, auditable proof. App developers bear responsibility for vetting monetization SDKs they integrate.

