Over the weekend, Google’s threat intelligence team linked five more Chinese hacking groups to attacks exploiting the maximum-severity “React2Shell” remote code execution vulnerability.
Tracked as CVE-2025-55182, this actively exploited flaw affects the React open-source JavaScript library and allows unauthenticated attackers to execute arbitrary code in React and Next.js applications with a single HTTP request.
While multiple React packages (i.e., react-server-dom-parcel, react-server-dom-turbopack, and react-server-dom-webpack) are vulnerable in their default configurations, the vulnerability only affects React versions 19.0, 19.1.0, 19.1.1, and 19.2.0 released over the past year.
After the attacks began, Palo Alto Networks reported that dozens of organizations had been breached, including incidents linked to Chinese state-backed threat actors. The attackers are exploiting the flaw to execute commands and steal AWS configuration files, credentials, and other sensitive information.
The Amazon Web Services (AWS) security team also warned that the China-linked Earth Lamia and Jackpot Panda threat actors had begun exploiting React2Shell within hours of the vulnerability’s disclosure.
Five more Chinese hacking groups linked to attacks
On Saturday, the Google Threat Intelligence Group (GTIG) reported detecting at least five more Chinese cyber-espionage groups joining ongoing React2Shell attacks that started after the flaw was disclosed on December 3.
The list of state-linked threat groups exploiting the flaw now also includes UNC6600 (which deployed MINOCAT tunneling software), UNC6586 (the SNOWLIGHT downloader), UNC6588 (the COMPOOD backdoor payload), UNC6603 (an updated version of the HISONIC backdoor), and UNC6595 (ANGRYREBEL.LINUX Remote Access Trojan).
“Due to the use of React Server Components (RSC) in popular frameworks like Next.js, there are a significant number of exposed systems vulnerable to this issue,” GTIG researchers said.
“GTIG has also observed numerous discussions regarding CVE-2025-55182 in underground forums, including threads in which threat actors have shared links to scanning tools, proof-of-concept (PoC) code, and their experiences using these tools.”
While investigating these attacks, GTIG also spotted Iranian threat actors targeting the flaw and financially motivated attackers deploying XMRig cryptocurrency mining software on unpatched systems.
Shadowserver Internet watchdog group is currently tracking over 116,000 IP addresses vulnerable to React2Shell attacks, with over 80,000 in the United States.
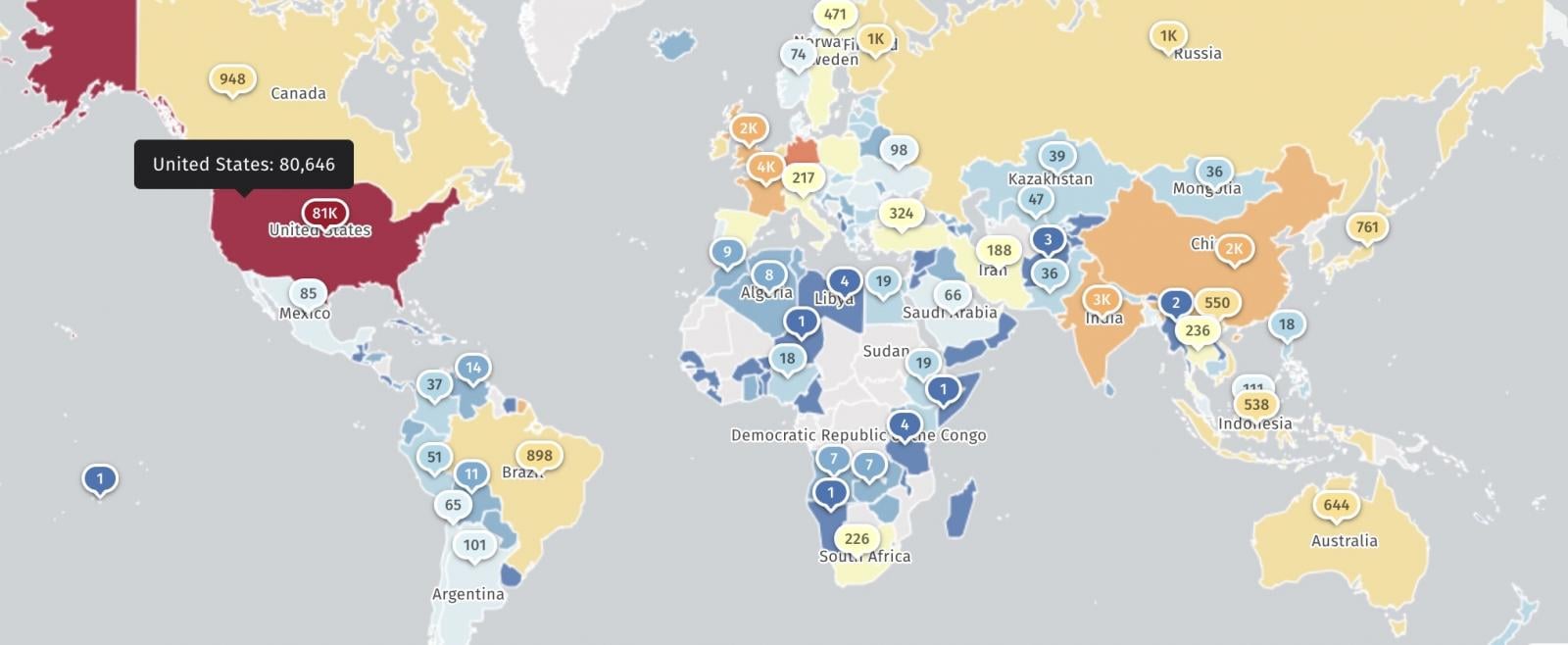
GreyNoise has also observed over 670 IP addresses attempting to exploit the React2Shell remote code execution flaw over the past 24 hours, primarily originating from the United States, India, France, Germany, the Netherlands, Singapore, Russia, Australia, the United Kingdom, and China.
On December 5, Cloudflare linked a global website outage to emergency mitigations for the React2Shell vulnerability.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.



