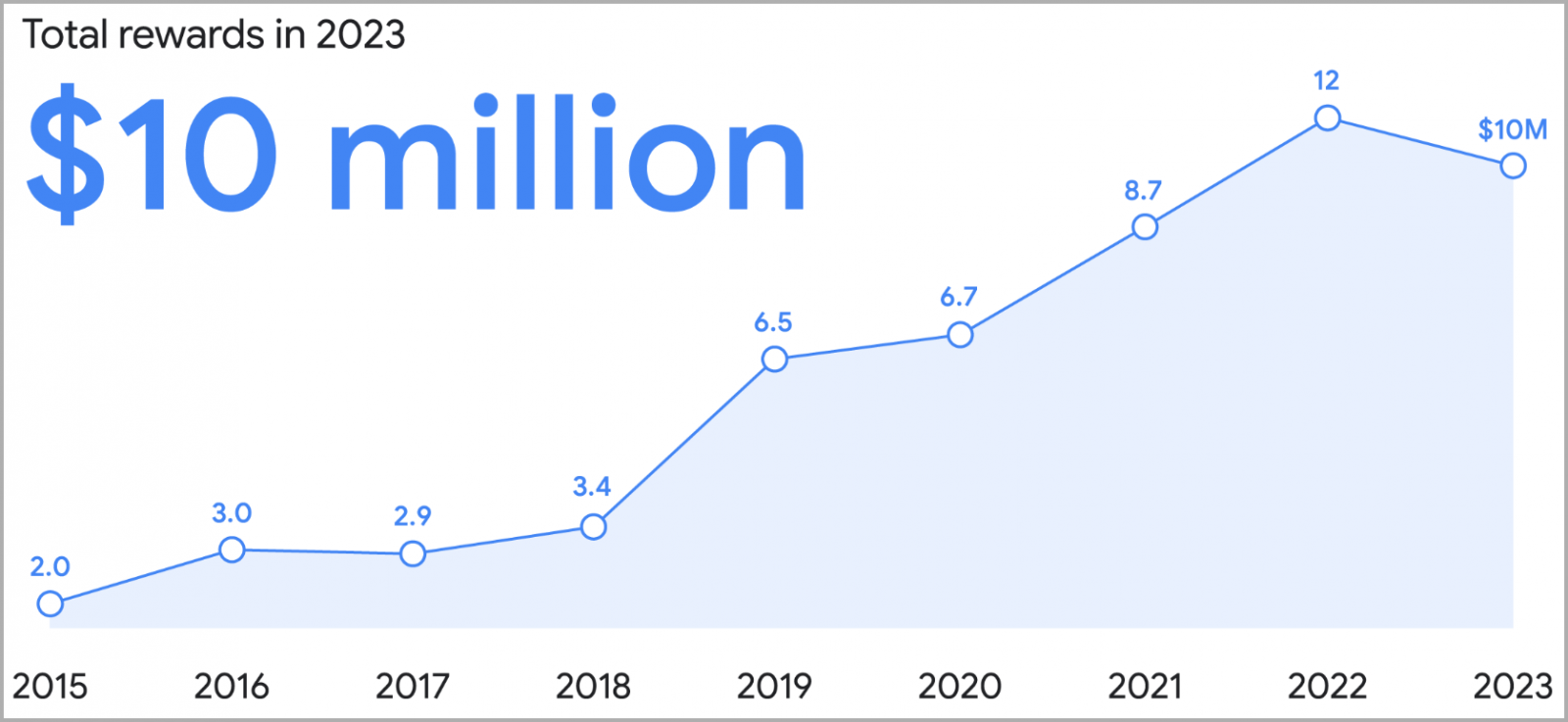
Google awarded $10 million to 632 researchers from 68 countries in 2023 for finding and responsibly reporting security flaws in the company’s products and services.
Though this is lower than the $12 million Google’s Vulnerability Reward Program paid to researchers in 2022, the amount is still significant, showcasing a high level of community participation in Google’s security efforts.
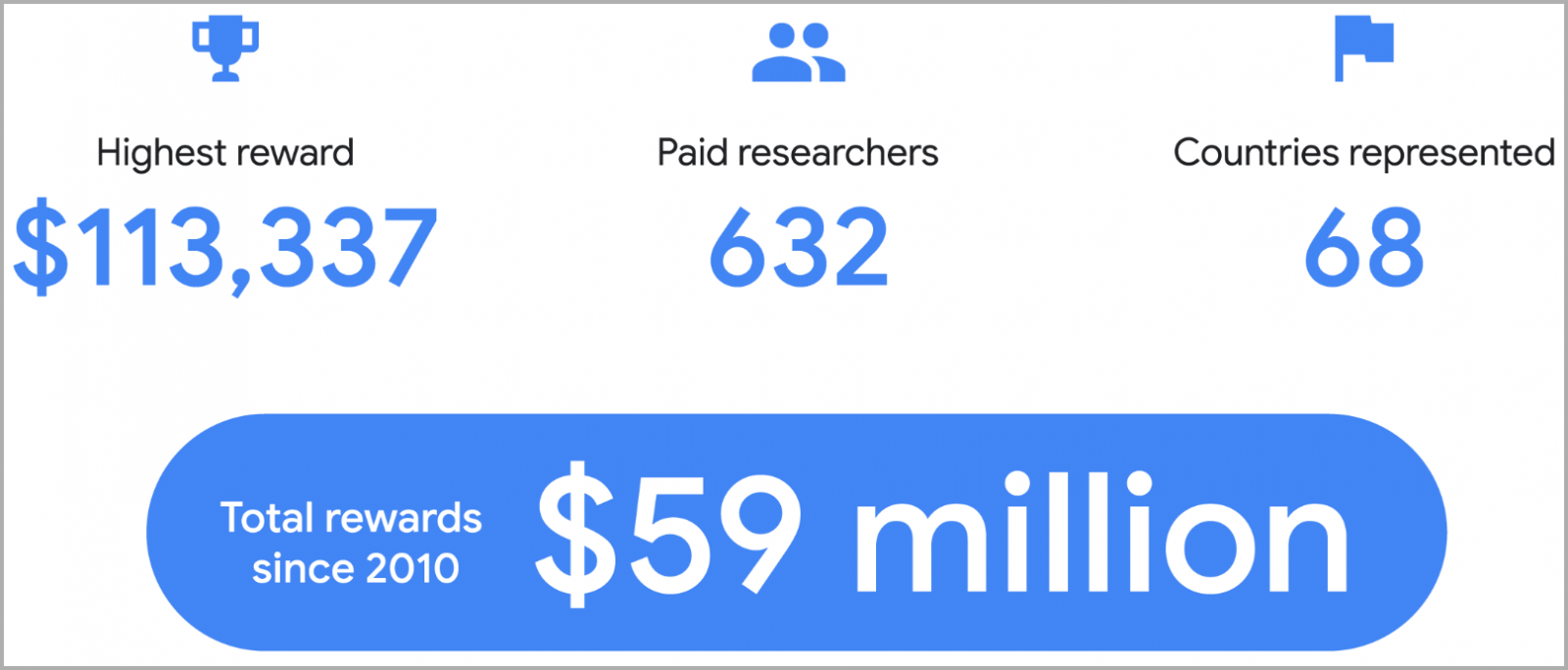
The highest reward for a vulnerability report in 2023 was $113,337, while the total tally since the program’s launch in 2010 has reached $59 million.
For Android, the world’s most popular and widely used mobile operating system, the program awarded over $3.4 million.
Google also increased the maximum reward amount for critical vulnerabilities concerning Android to $15,000, driving increased community reports.
During security conferences like ESCAL8 and hardwea.io, Google awarded $70,000 for 20 critical discoveries in Wear OS and Android Automotive OS and another $116,000 for 50 reports concerning issues in Nest, Fitbit, and Wearables.
Google’s other big software project, the Chrome browser, was the subject of 359 security bug reports that paid out a total of $2.1 million.
On June 1, 2023, the company announced it would triple bounty payments for sandbox escape chain exploits targeting Chrome until December 1, 2023.
The program also increased rewards for bugs in older (before M105) versions of V8, Chrome’s JavaScript engine, leading to significant discoveries and rewards like a $30,000 award for a long-existing (since M91) V8 JIT optimization bug.
Another point highlighted in Google’s post is the introduction of ‘MiraclePtr’ in Chrome M116, which protects against non-renderer Use-After-Free (UAF) vulnerabilities.
Due to these flaws being deemed ‘highly mitigated’ after the introduction of MiraclePtr, Google introduced a separate class of rewards for bypassing the protection mechanism itself.
Finally, the review also touches on the efforts in security generative AI products like Google Bard, with 35 researcher reports in a bugSWAT live-hacking event generating $87,000 in payouts.
Apart from the rewards themselves, the bug bounty program had the following key developments and enhancements during 2023:
- The introduction of the Bonus Awards program, offering extra rewards for specific targets.
- Expansion of the exploit reward program to include Chrome and Cloud, highlighted by the launch of v8CTF, focusing on Chrome’s V8 JavaScript engine.
- The inauguration of the Mobile VRP for first-party Android applications.
- Launch of the Bughunters blog to share insights and safety measures for the internet.
- The hosting of the ESCAL8 security conference in Tokyo, featuring live hacking events, workshops, and talks.
Those who wish to get involved in Google’s bug bounty program can learn more about it through its Bug Hunters community.
