Android and iOS apps on the Google Play Store and Apple App Store contain a malicious software development kit (SDK) designed to steal cryptocurrency wallet recovery phrases using optical character recognition (OCR) stealers.
The campaign is called “SparkCat” after the name (“Spark”) of one of the malicious SDK components in the infected apps, with developers likely not knowingly participating in the operation.
According to Kaspersky, on Google Play alone, where download numbers are publicly available, the infected apps were downloaded over 242,000 times.
“We found Android and iOS apps that had a malicious SDK/framework embedded to steal crypto wallet recovery phrases, some of which were available on Google Play and the App Store,” explains Kaspersky.
“The infected apps were downloaded more than 242,000 times from Google Play. This is the first known case of a stealer being found in the App Store.”
Spark SDK stealing your crypto
The malicious SDK on infected Android apps utilizes a malicious Java component called “Spark,” disguised as an analytics module. It uses an encrypted configuration file stored on GitLab, which provides commands and operational updates.
On the iOS platform, the framework has different names like “Gzip,” “googleappsdk,” or “stat.” Also, it utilizes a Rust-based networking module called “im_net_sys” to handle communication with the command and control (C2) servers.
The module uses Google ML Kit OCR to extract text from images on the device, trying to locate recovery phrases that can be used to load cryptocurrency wallets on attackers’ devices without knowing the password.
“It (the malicious component) loads different OCR models depending on the language of the system to distinguish Latin, Korean, Chinese and Japanese characters in pictures,” explains Kaspersky.
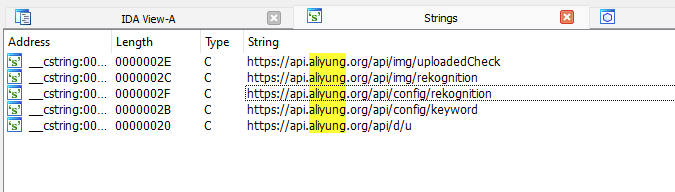
“Then, the SDK uploads information about the device to the command server along the path / api / e / d / u, and in response, receives an object that regulates the subsequent operation of the malware.”
Source: Kaspersky
The malware searches for images containing secrets by using specific keywords in different languages, which change per region (Europe, Asia, etc.).
Kaspersky says that while some apps show region-specific targeting, the possibility of them working outside the designated geographic areas cannot be excluded.
The infected apps
According to Kaspersky, there are eighteen infected Android and 10 iOS apps, with many still available in their respective app stores.
One of the apps reported as infected by Kaspersky is the Android ChatAi app, which was installed over 50,000 times. This app is no longer available on Google Play.

Source: Kaspersky
A full list of the impacted apps can be found at the end of Kaspersky’s report.
If you have any of these apps installed on your devices, you are recommended to uninstall them immediately and use a mobile antivirus tool to scan for any remnants. A factory reset should also be considered.
In general, storing cryptocurrency wallet recovery phrases in screenshots is a practice that should be avoided.
Instead, store them in physical offline media, encrypted removable storage devices, or in the vault of self-hosted, offline password managers.
BleepingComputer has contacted Apple and Google with a request for a comment on the presence of the listed apps on their respective app stores, and we will update this post with their responses.
