A financially motivated threat group dubbed Greedy Sponge has been systematically targeting Mexican financial institutions and organizations since 2021 with a heavily modified version of the AllaKore remote access trojan (RAT).
The campaign represents a sophisticated evolution of cybercriminal tactics, combining traditional social engineering with advanced technical capabilities designed specifically for financial fraud operations.
The threat actors deploy their malware through spear-phishing campaigns and drive-by downloads, utilizing trojanized Microsoft installer (MSI) files that masquerade as legitimate software updates.
These malicious packages contain a .NET downloader component that retrieves the customized AllaKore payload from command-and-control servers hosted on Hostwinds infrastructure in Dallas, Texas.
.webp)
The attackers have demonstrated particular cunning in their geographic targeting, implementing server-side geofencing mechanisms that restrict payload delivery exclusively to systems located within Mexico.
Arctic Wolf Labs researchers identified significant enhancements to the threat group’s operational capabilities, noting the integration of SystemBC as a secondary infection vector.
This multi-platform malware proxy tool enables the attackers to establish persistent backdoor access and deploy additional malicious payloads as needed.
The researchers observed that recent campaigns have moved away from client-side geographic filtering to server-side restrictions, making detection and analysis considerably more challenging for security teams.
Advanced Persistence and Evasion Mechanisms
The modified AllaKore variant employs sophisticated persistence techniques that demonstrate the group’s technical maturity.
.webp)
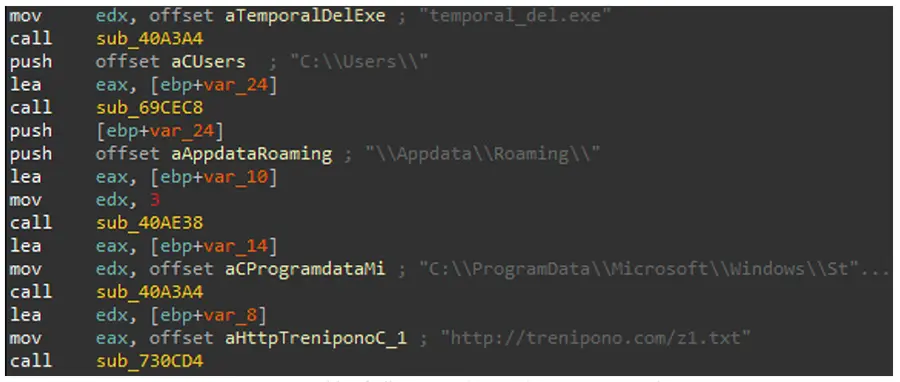
Upon successful infection, the malware establishes persistence by placing an updated version of itself in the system’s Startup folder, retrieved from the URI endpoint /z1.txt.
The persistence mechanism is coupled with a comprehensive cleanup operation using PowerShell scripts that eliminate traces of the initial infection vector from the %APPDATA% directory.
The malware’s evasion capabilities include a User Account Control (UAC) bypass technique utilizing Microsoft’s Connection Manager Profile Installer (CMSTP.exe).
This legitimate Windows binary is exploited to proxy execution of malicious code while appearing as a routine system update process labeled “Actualizando” (Spanish for “updating”).
The .NET downloader component uses a distinctive user-agent string Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2; .NET CLR 1.0.3705;) for command-and-control communications, employing base64 encoding to obfuscate network traffic patterns.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
