The scraped Chess.com data was leaked on Breach Forums on November 8th, 2023 by a threat actor operating under the alias ‘DrOne.’
A threat actor operating under the alias ‘DrOne’ has claimed responsibility for leaking the scraped database of Chess.com containing the personal data of more than 800,000 registered users.
Chess.com is a highly popular online platform for chess enthusiasts and a social networking website. As of 2023, the platform boasts more than 150 million registered users, indicating that the leaked records account for approximately only 0.533% of the total user base.
The database was disclosed on November 8th, 2023 on Breach Forums, a well-known platform for hackers and cybercrime activities. Interestingly, this forum recently saw another threat actor leaking a scraped database from LinkedIn just a couple of days prior, which contained information from 25 million users.
The Leaked Data
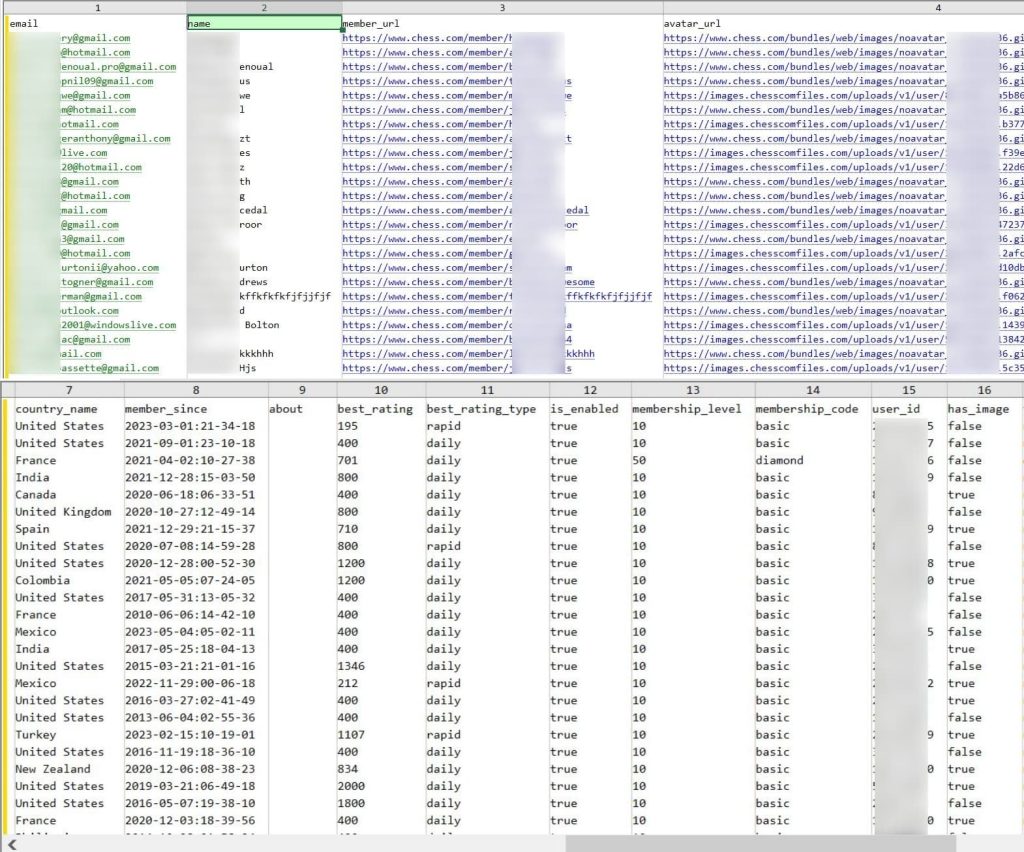
After a comprehensive scan of the Chess.com database by Hackread.com, our analysis confirms the exposure of personal data from 828,327 registered users. The leaked information includes:
- Full names
- Usernames
- Profile links
- Email addresses
- Users’ originating countries
- Avatar URLs (containing profile pictures)
- Universally Unique Identifier (UUID) and User IDs
- Date of registration (with the most recent sign-up in September 2023)
If combined, the leaked information can serve as a treasure trove for cybercriminals. This data could be utilized for identity theft, phishing scams, social engineering attacks, or even to cross-reference previously leaked login credentials in order to obtain passwords.
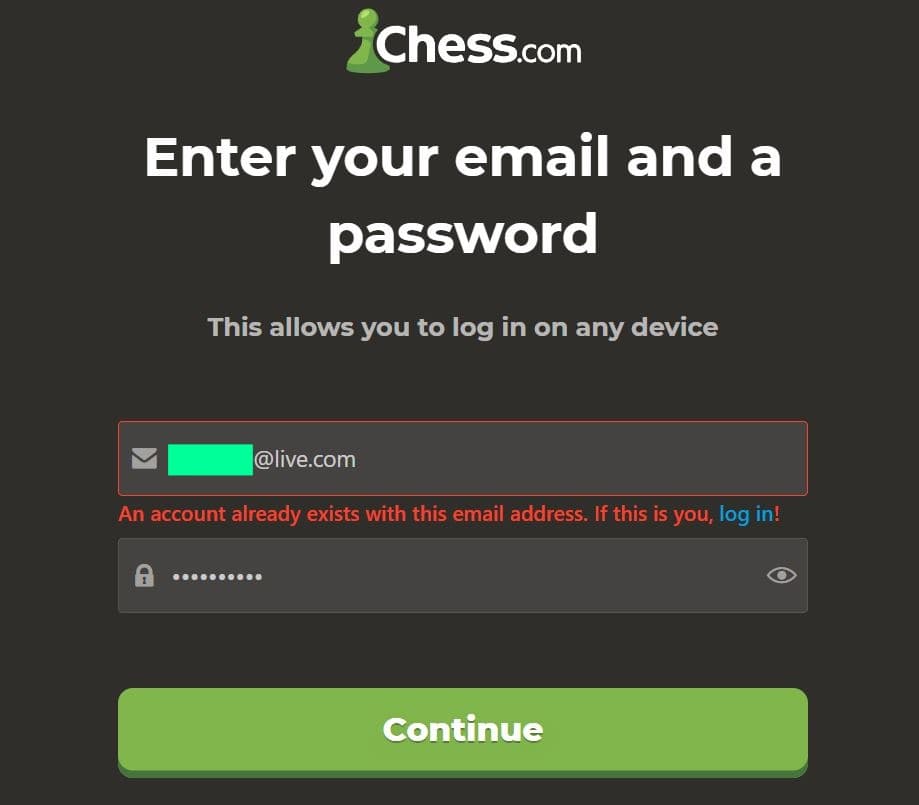
Fortunately, the leaked data does not include passwords. However, when Hackread.com attempted to sign up using the leaked email addresses, nearly every email address used prompted the message ‘An account already exists with this email address.’ This suggests that the leaked database contained valid and active email addresses associated with existing Chess.com accounts.
Web Scraping is Hard to Avoid/Block
Web scraping or data scraping, is an automated process utilized by software to extract data from websites, primarily for gathering specific information from web pages. The process is almost impossible to block since Chess.com is a large website.
Large websites use a variety of measures to prevent scraping, such as rate limiting and captcha challenges. However, scrapers are constantly developing new techniques to circumvent these measures and some scrapers may collect the data for research purposes, such as to study social networks or to develop machine learning models.
Chess.com and Cybersecurity
This is not the first time Chess.com has made headlines for cybersecurity-related issues. In February 2021, a well-known ethical hacker, Sam Curry, discovered and reported a critical vulnerability within the platform. This flaw allowed the researcher to potentially access any account on the site, including the administrator account.
This new breach poses a significant threat to Chess.com users, potentially facilitating various scams such as identity theft and phishing. For Chess.com users, it is strongly recommended to change your password not only on the platform but also across any other online accounts where the same password is used.
Cybercriminals might deploy phishing tactics, sending emails with links leading to malicious websites mimicking Chess.com or other legitimate platforms. It is crucial to refrain from clicking on any such links. However, you can safely check the real URL by hovering over the link before clicking it.
RELATED ARTICLES
- Hackers leak scraped data of 87,000 GETTR users
- Scraped data of 1.3 million Clubhouse users published online
- Twitter Scraping Breach: 209M Accounts Leaked on Hacker Forum
- API Misuse: Hacker Exposes 2.6M Duolingo Users’ Emails & Names
- Data scraping firm leaks 235m Instagram, TikTok, YouTube user data
