Hackers are likely starting to exploit CVE-2025-49113, a critical vulnerability in the widely used Roundcube open-source webmail application that allows remote execution.
The security issue has been present in Roundcube for over a decade and impacts versions of Roundcube webmail 1.1.0 through 1.6.10. It received a patch on June 1st.
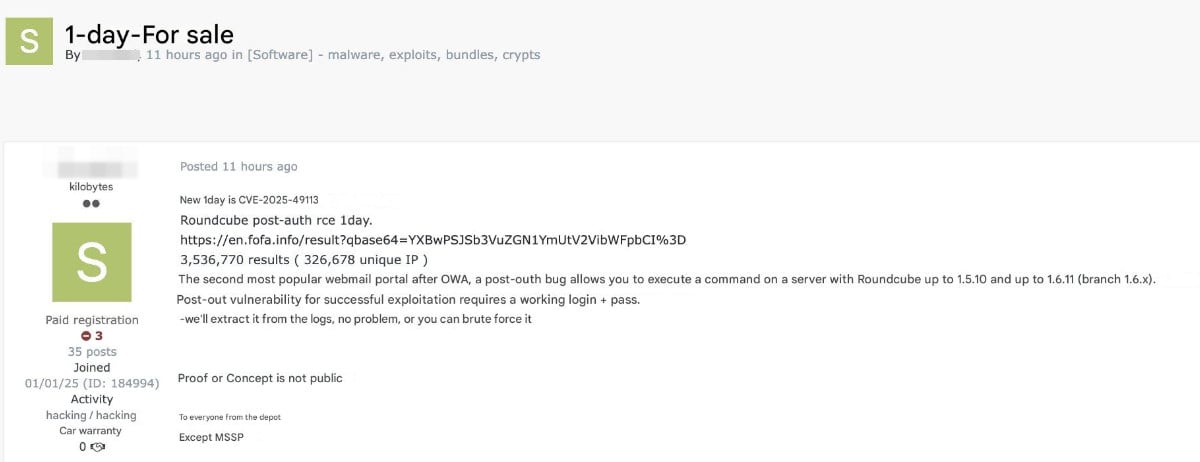
It took attackers just a couple of days to reverse engineer the fix, weaponize the vulnerability, and start selling a working exploit on at least one hacker forum.
Roundcube is one of the most popular webmail solutions as the product is included in offers from well-known hosting providers such as GoDaddy, Hostinger, Dreamhost, or OVH.
“Email armageddon”
CVE-2025-49113 is a post-authentication remote code execution (RCE) vulnerability that received a critical severity score of 9.9 out of 10 and is described as “email armageddon.”
It was discovered and reported by Kirill Firsov, the CEO of the cybersecurity company FearsOff, who decided to publish the technical details before the end of the responsible disclosure period because an exploit had become available.
“Given the active exploitation and evidence of the exploit being sold in underground forums, I believe it is in the best interest of defenders, blue teams, and the broader security community to publish a full technical breakdown but without complete PoC for now” – Kirill Firsov
At the root of the security problem is the lack of sanitization of the $_GET[‘_from’] parameter, which leads to PHP Object deserialization.
In the technical report, Firsov explains that when an exclamation mark initiates a session variable name, the session becomes corrupted and object injection becomes possible.
After Roundcube received a patch, attackers analyzed the modifications it introduced, developed an exploit, and advertised it on a hacker forum, noting that a working login is required.
However, the need for login credentials does not seem like a deterrent, since the threat actor offering the exploit says that they can extract it from the logs, or it can be brute forced.
Firsov says that the credential combination could also be obtained through cross-site request forgery (CSRF).
source: Kirill Firsov
According to Firsov, at least one vulnerability broker pays up to $50,000 for an RCE exploit in Roundcube.
The researcher published a video to demonstrate how the vulnerability can be exploited. It should be noted that the researcher uses the vulnerability identifier CVE-2025-48745 in the demonstration, which is currently rejected as a duplicate candidate for CVE-2025-49113.
Despite being a less-known application among consumers, Roundcube is very popular, mostly because it is highly customizable with more than 200 options, and it is freely available.
Apart from being offered by hosting providers and bundled in web hosting control panels (cPanel, Plesk), numerous organizations in the government, academic, and tech sectors use Roundcube.
Firsov also says that this webmail app has such a wide presence that a pentester is more likely to find a Roundcube instance than an SSL misconfiguration.
Considering the ubiquity of the application, the researcher says that “the attack surface isn’t big – it’s industrial.”
Indeed, a quick look on search engines for discovering internet-connected devices and services shows at least 1.2 million Roundcube hosts.
Manual patching is outdated. It’s slow, error-prone, and tough to scale.
Join Kandji + Tines on June 4 to see why old methods fall short. See real-world examples of how modern teams use automation to patch faster, cut risk, stay compliant, and skip the complex scripts.

