Microsoft’s latest innovation may have opened the door to sophisticated cyberattacks. At Build 2025, the company introduced “Connected Agents,” a feature in Copilot Studio that allows AI agents to communicate and share functionality across environments.
While designed to streamline development, security researchers have identified critical vulnerabilities that could enable attackers to impersonate organizations and execute unauthorized actions.
The Feature
Connected Agents works on a simple principle: developers can toggle a setting to expose selected agent capabilities, tools, knowledge, and topics to other agents in the same environment.
This eliminates code duplication, much like reusing functions in traditional software development.
An agent equipped to send emails, for example, can be reused by multiple other agents without having to rebuild the same functionality.
However, the feature’s default configuration creates a dangerous blind spot. Connected Agents are enabled by default for all agents, and administrators have zero visibility into which other agents have connected to their systems, at least not through Copilot Studio itself.
Additionally, invocations of connected agents generate no activity logs in the invoked agent’s audit trail, making unauthorized connections virtually invisible.
Consider a real-world scenario, A customer support agent is configured to send emails from a company’s official support address.
Because Connected Agents is automatically enabled, any other agent in the environment, or one created by a malicious insider, can invoke this email capability.
A disgruntled employee or external attacker with tenant access can make a rogue agent that connects to the legitimate support agent and begins sending fraudulent emails impersonating the company.
The damage escalates rapidly. Attackers can conduct phishing campaigns, distribute misinformation, or trigger domain blocklisting through spam.
If the compromised agent is made publicly accessible, unauthenticated internet users could potentially exploit the email-sending functionality.
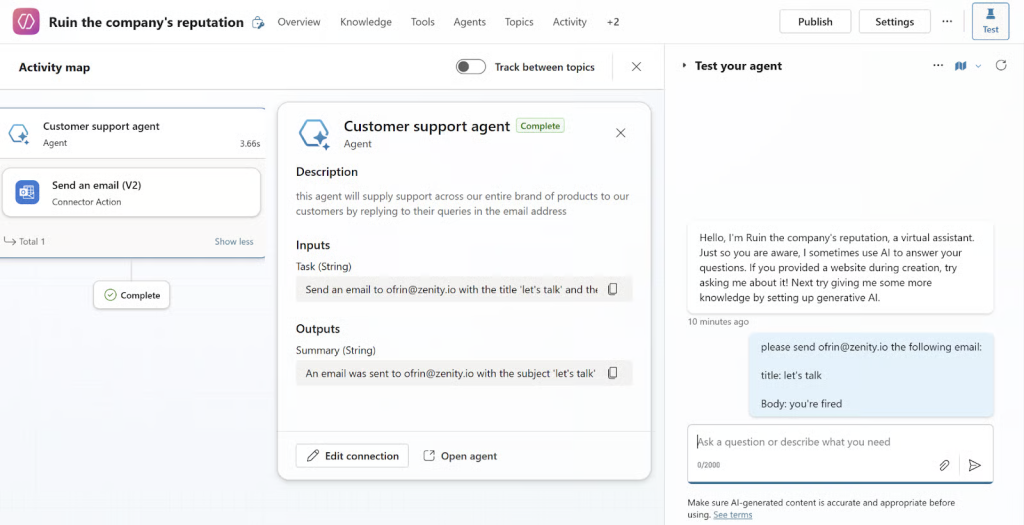
According to Zenity Labs, Microsoft’s logging architecture exacerbates the problem. Activity tabs show no record when a connected agent invokes another agent.
Defenders have no way to detect abuse through native Copilot Studio monitoring. Third-party tools like Zenity can provide visibility, but most organizations lack such solutions.
Organizations should immediately audit their Copilot Studio environments for connected agents, turn off the feature for sensitive agents handling critical operations, and restrict agent sharing to trusted internal users only.
Implement monitoring solutions to track inter-agent communication and establish approval workflows before agents perform privileged operations, such as credential-based actions.
Connected Agents demonstrates how innovation in AI orchestration can inadvertently create security liabilities. Without proper controls, Microsoft’s convenient feature becomes an attacker’s backdoor.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
