Hackers are utilizing the WordPress mu-plugins (“Must-Use Plugins”) directory to stealthily run malicious code on every page while evading detection.
The technique was first observed by security researchers at Sucuri in February 2025, but adoption rates are on the rise, with threat actors now utilizing the folder to run three distinct types of malicious code.
“The fact that we’ve seen so many infections inside mu-plugins suggests that attackers are actively targeting this directory as a persistent foothold,” explains Sucuri’s security analyst Puja Srivastava.
“Must-have” malware
Must-Use Plugins (mu-plugins) are a special type of WordPress plugin that automatically execute on every page load without needing to be activated in the admin dashboard.
They are PHP files stored in the ‘wp-content/mu-plugins/‘ directory that automatically execute when the page is loaded, and they are not listed in the regular “Plugins” admin page unless the “Must-Use” filter is checked.
Mu-plugins have legitimate use cases such as enforcing site-wide functionality for custom security rules, performance tweaks, and dynamically modifying variables or other code.
However, because MU-plugins run on every page load and don’t appear in the standard plugin list, they can be used to stealthily perform a wide range of malicious activity, such as stealing credentials, injecting malicious code, or altering HTML output.
Sucuri has discovered three payloads that attackers are planting in the mu-plugins directory, which appears to be part of financially motivated operations.
These are summarized as follows:
- redirect.php: Redirects visitors (excluding bots and logged-in admins) to a malicious website (updatesnow[.]net) that displays a fake browser update prompt to trick them into downloading malware.
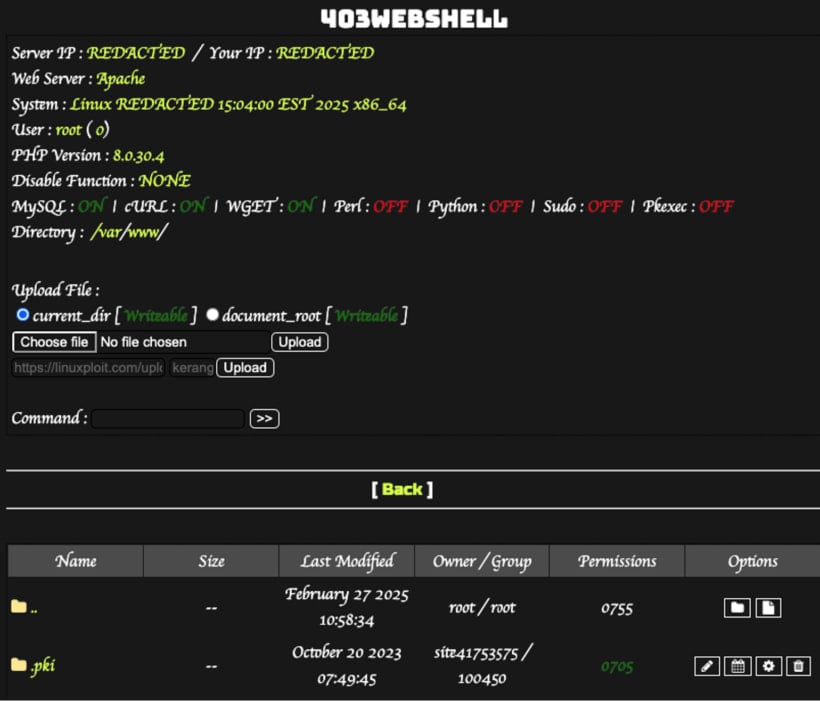
- index.php: Webshell that acts as a backdoor, fetching and executing PHP code from a GitHub repository.
- custom-js-loader.php: Loads JavaScript that replaces all images on the site with explicit content and hijacks all outbound links, opening shady popups instead.
Source: Sucuri
The webshell case is particularly dangerous as it allows the attackers to remotely execute commands on the server, steal data, and launch downstream attacks on members/visitors.
The other two payloads can also be damaging as they hurt a site’s reputation and SEO scores due to shady redirections and attempt to install malware on visitor’s computers.
Sucuri has not determined the exact infection pathway but hypothesizes that attackers exploit known vulnerabilities on plugins and themes or weak admin account credentials.
It is recommended that WordPress site admins apply security updates on their plugins and themes, disable or uninstall those that aren’t needed, and protect privileged accounts with strong credentials and multi-factor authentication.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
