Security researchers are observing a significant increase in internet-wide scans targeting the critical PAN-OS GlobalProtect vulnerability (CVE-2024-3400).
Exploit attempts have surged as attackers seek to leverage an arbitrary file creation flaw to achieve OS command injection and ultimately full root code execution on vulnerable firewalls.
Exploitation of Critical PAN-OS SSL VPN Flaw (CVE-2024-3400)
Since late September 2025, honeypots deployed globally have logged thousands of TCP connections probing PAN-OS SSL VPN portals.
SANS Technology Institute observed that one prominent source IP, 141.98.82.26, has repeatedly issued malicious POST requests to the /ssl-vpn/hipreport.esp endpoint, exploiting the lack of session ID validation. The attacker supplies a crafted Cookie header:
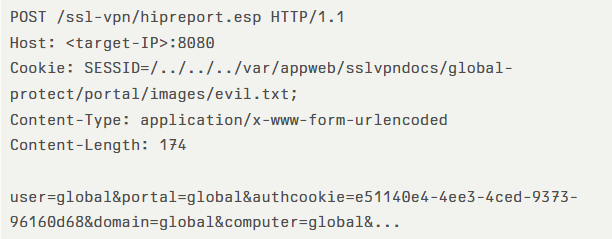
If the upload succeeds, a follow-up GET request for /global-protect/portal/images/evil.txt will return HTTP/403, confirming file presence.
Attackers then pivot file placement to directories, allowing command execution. These automated scans reflect the high CVSS 10.0 severity and network-accessible, unauthenticated attack vector of CVE-2024-3400.
| Risk Factors | Details |
| Affected Products | PAN-OS 10.2 versions before 10.2.9-h1, 11.0 versions before 11.0.4-h1, 11.1 versions before 11.1.2-h3 (with GlobalProtect gateway or portal enabled) |
| Impact | Arbitrary file creation leading to OS command injection and root code execution |
| Exploit Prerequisites | None (network-accessible, unauthenticated) |
| CVSS 3.1 Score | 10. 0 (Critical) |
Mitigations
Palo Alto Networks has released fixed PAN-OS versions—10.2.9-h1, 11.0.4-h1, 11.1.2-h3—and new hotfixes for affected branches.
An immediate upgrade is strongly advised to thwart ongoing exploitation. Administrators can also deploy Threat Prevention signatures 95187, 95189, and 95191 to block the initial arbitrary file creation interaction at the GlobalProtect interface.
For detection, operators should grep GPSvc logs for anomalous session ID strings:

Legitimate GUID patterns appear as hex-digit groups; any file-system path or shell snippet between sessions ( and ) indicates exploitation attempts.
A timeline of updates shows that enhanced factory reset (EFR) procedures and CLI commands for evidence collection were published between April and May 2024, underscoring the ongoing remediation efforts.
Cloud NGFW and Prisma Access customers are not affected; only on-premises PAN-OS 10.2–11.1 devices with GlobalProtect gateway or portal enabled are at risk.
Organizations should verify configuration via the firewall GUI under Network > GlobalProtect > Gateways/Portals and audit for unauthorized files in /var/appweb/sslvpndocs.
As threat actors continue to weaponize CVE-2024-3400, vigilant patch management, proactive log inspection, and robust Threat Prevention enforcement remain critical to defend against unauthorized root-level access.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
