Apache Axis is a web service engine that provides the capability to add web service interfaces to web applications.
It can function as a standalone application server and supports SOAP 1.1, SOAP 1.2, and the REST style of web services.

Recently, the researchers at Binary Defense identified that hackers have been actively attacking the Apache AXIS server to deploy malicious web shells.
Apache AXIS Server
In August of 2024, a China-linked threat actor breached three unmanaged AIX servers which were accessed through the internet with the basic passwords used in the administration of the Apache Axis servers.
Meet the CISOs, Join the Virtual Panel to Learn compliance – Join Free
The attacker then proceeded to upload an AxisInvoker web shell, gained SSH access, and used a Fast Reverse Proxy (FRP) for persistent communication with the targeted network.
From March to August, reconnaissance was conducted by them with the help of LDAP, SMB shares, and local config files.
The threat actors then switched to Windows OS, where it attempted to insert Cobalt Strike beacons and web shells made with JavaScript.
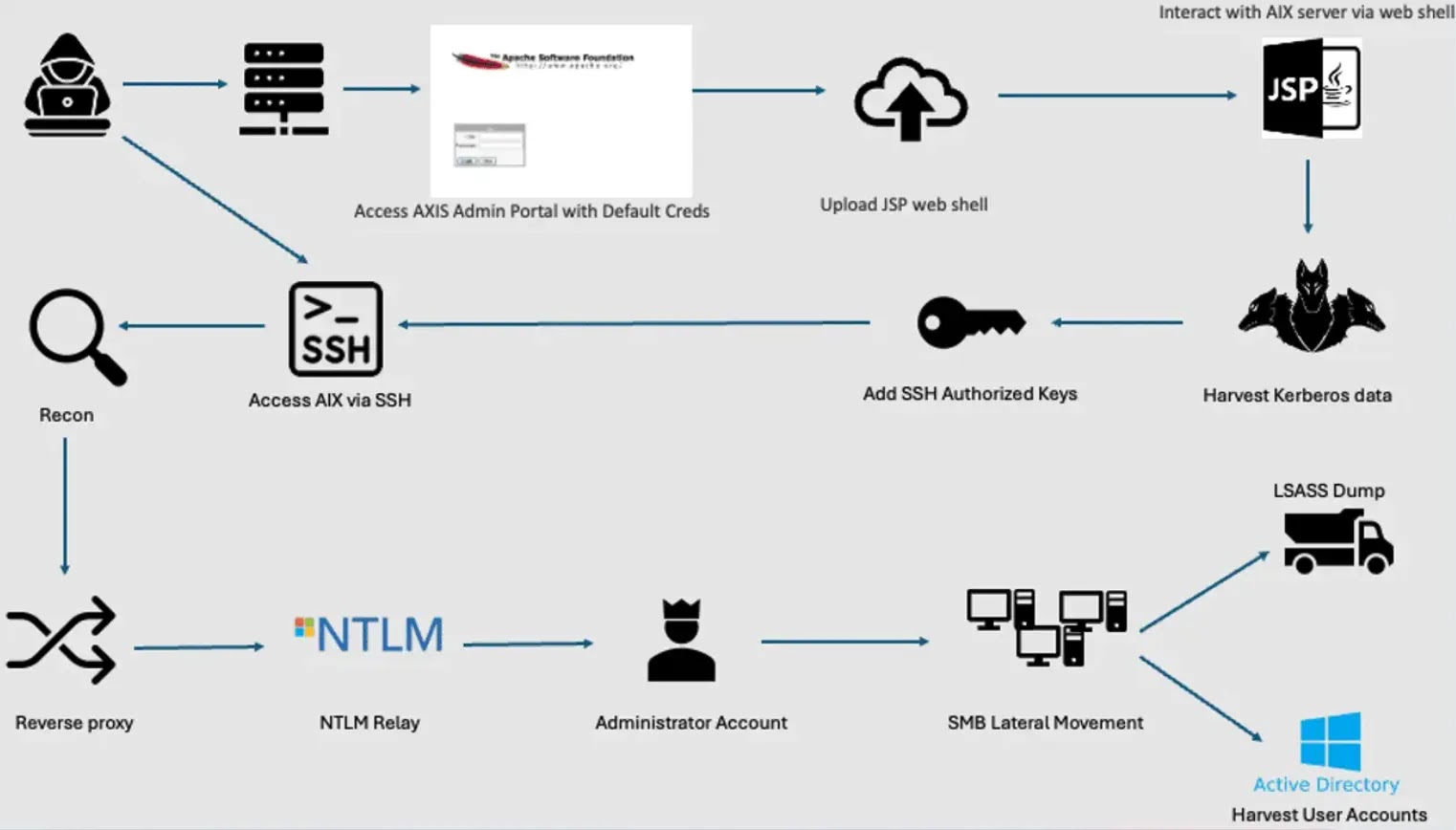
They carried out NTLM relay attacks to conduct Active Directory reconnaissance and impersonation of accounts.
The invasion was limited when someone tried to dump the LSASS process memory which is a well-known technique for harvesting credentials on a Windows server.
Such an event illustrates the dangers of shadow IT when the IT solutions are implemented without the security team’s control.
It highlights the importance of advanced threat detection across the entire network even including the outdated systems to prevent such a complex attack that employs insignificant and low-profile vectors.
Binary Defense report states that the unmanaged AIX (Advanced Interactive eXecutive) servers have proved vulnerable to sophisticated attacks.
Threat actors who may be of Chinese origin were able to use these systems employing the AXISInvoker web shell and the Fast Reverse Proxy (FRP) tool to gain initial access.
They crossed over to a Windows environment and tried to go lateral but were prevented by security mechanisms and controls in place.
The attackers used such Linux commands as ‘wget’ and ‘curl’, which are incompatible with AIX solutions, and were blocked from creating a Command and Control (C2) channel through cobalt Strike.
This incident illustrates the need for comprehensive security monitoring in every networked device, including legacy and seemingly low-priority systems.
It warns about the threats of shadow IT and explains the necessity of regular monitoring and audits, management of credentials, and elements of security integration.
Organizations need to make sure no system lacks visibility and protection to prevent this scenario from happening again and to be able to strengthen the security defenses even better than before.
Are You From SOC/DFIR Teams? - Try Advanced Malware and Phishing Analysis With ANY.RUN - 14-day free trial




