Since last summer, hotel owners and employees have grappled with a surge in malicious e-mails disguised as ordinary correspondence from previous or potential guests.
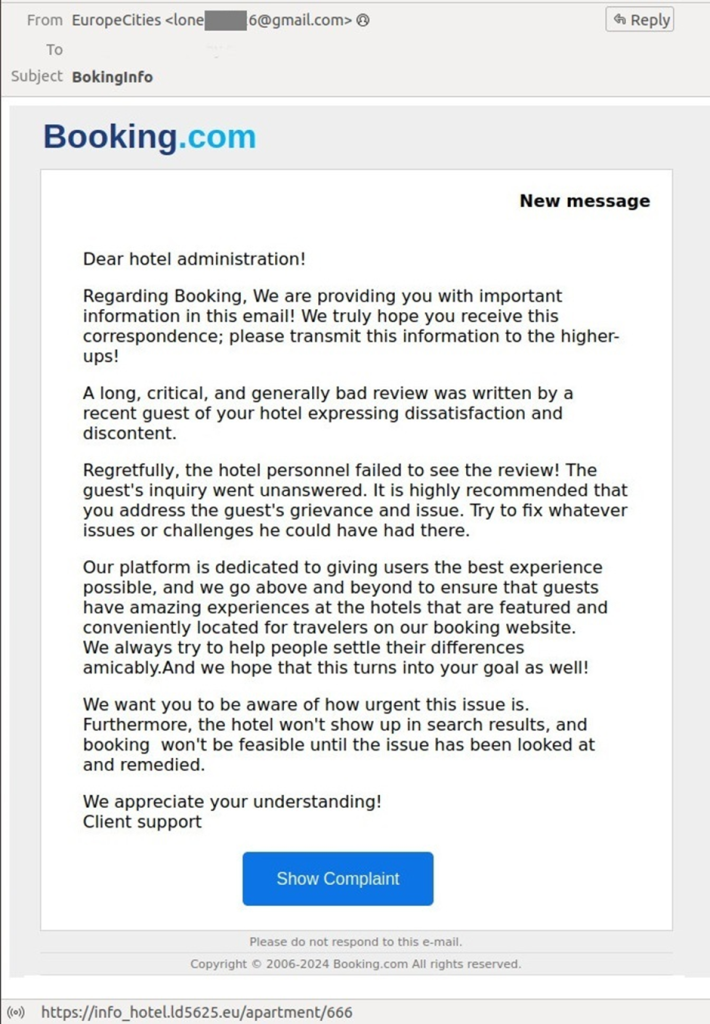
These e-mails, often appearing as typical messages sent to the hotel’s public e-mail address or as urgent requests from Booking.com, aim to steal employees’ login credentials or infect hotel systems with malware.
=The attackers’ tactics have evolved, making it increasingly challenging for hotel staff to identify and thwart these threats.
According to the reports from Kaspersky, when targeting hotels, cybercriminals exploit the industry’s inherent customer service focus.
Hotel employees, eager to resolve conflicts and fulfill requests to maintain their establishment’s reputation, often fall prey to these attacks.
The attackers craft e-mails that mimic genuine customer inquiries or complaints, prompting employees to follow links or open attachments that contain malware.
This method termed a “customer focus attack,” leverages the hotel’s commitment to customer satisfaction to breach its defenses.
E-mail Content: Complaints and Inquiries
The malicious e-mails generally follow two themes: complaints or inquiries.
Scan Your Business Email Inbox to Find Advanced Email Threats - Try AI-Powered Free Threat Scan
In complaint-based e-mails, attackers pose as dissatisfied guests, citing unethical staff behavior, double-charged bank cards, or poor accommodation conditions.
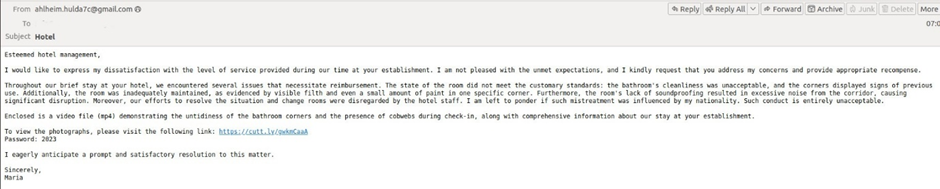
They often include supposed evidence like videos, photos, or bank statements to lend credibility to their claims.
In inquiry-based e-mails, attackers pose as potential guests seeking information about hotel services and pricing.
These inquiries cover various topics, from room amenities to sustainable energy sources, making them appear legitimate.
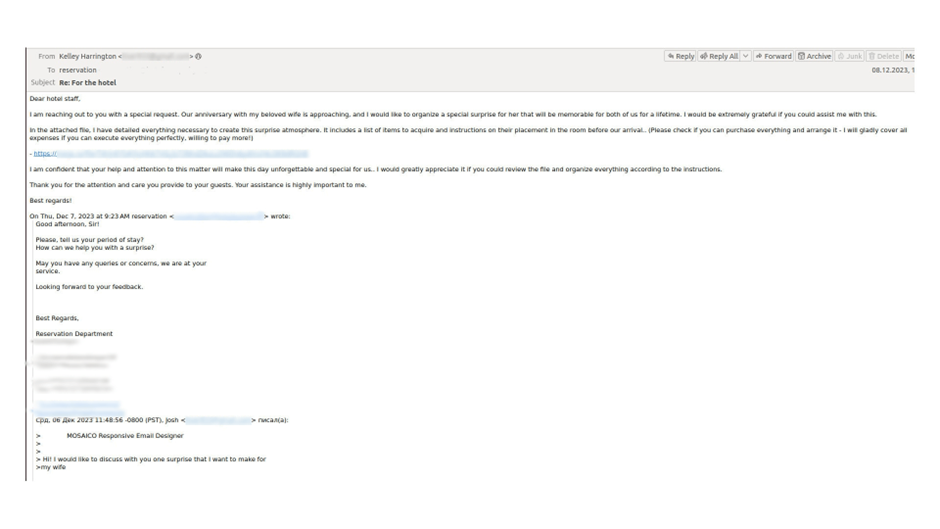
In some cases, attackers employ a more sophisticated approach, engaging in multi-stage correspondence with hotel staff.
Initially, they send innocuous messages about accommodation conditions, gradually building trust.
For example, an attacker might pose as a potential customer planning a surprise for their spouse.
After a few exchanges, they send an e-mail with a link to a malicious file, claiming it contains detailed instructions for the surprise.
This method lulls the victim into a false sense of security before delivering the payload.
End Goals: Credential Theft and Malware Infection
The primary objective of these cybercriminals is to obtain login credentials, which they can then use in other scams or sell on the dark web.
Compromised hotel accounts on Booking.com can be exploited to scam clients out of payment information.
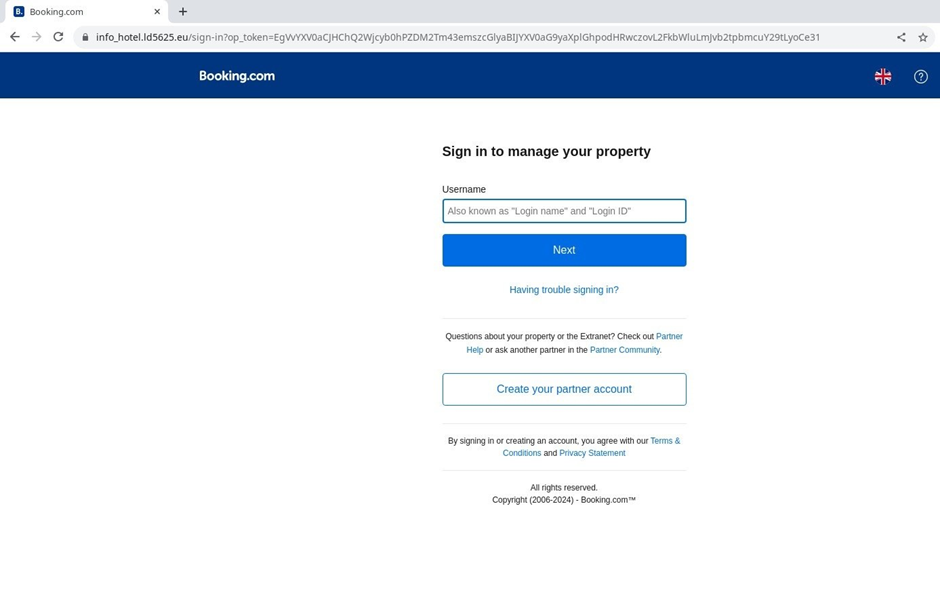
Attackers use various methods to achieve their goals, including phishing links that mimic Booking.com login or corporate credential forms.
They also employ malware, such as the XWorm backdoor and the RedLine stealer, to infect victims’ devices and steal passwords.
How to Defend Against These Attacks
To protect against these sophisticated attacks, hotels should implement several key measures:
- Security Awareness Training: Regular training sessions can equip employees to recognize and resist social engineering techniques. For instance, employees should be trained to scrutinize the sender’s e-mail address and be wary of free e-mail services used by attackers.
- E-mail Gateway Protection: Implementing protection at the e-mail gateway level can prevent phishing, malicious links, and dangerous attachments from reaching employees’ inboxes.
- Robust Security Solutions: Installing comprehensive security solutions with anti-phishing technology on all work devices can provide an additional layer of defense.
- Stay Informed: Keeping up-to-date with the latest e-mail threats through reliable sources can help hotels stay ahead of cybercriminals’ evolving tactics.
By adopting these measures, hotels can significantly reduce the risk of falling victim to these malicious e-mail campaigns and safeguard their operations and reputation.
Free Webinar! 3 Security Trends to Maximize MSP Growth -> Register For Free
