Grafana, the popular open-source analytics and visualization platform, has once again become the target of a large‐scale, coordinated exploitation effort.
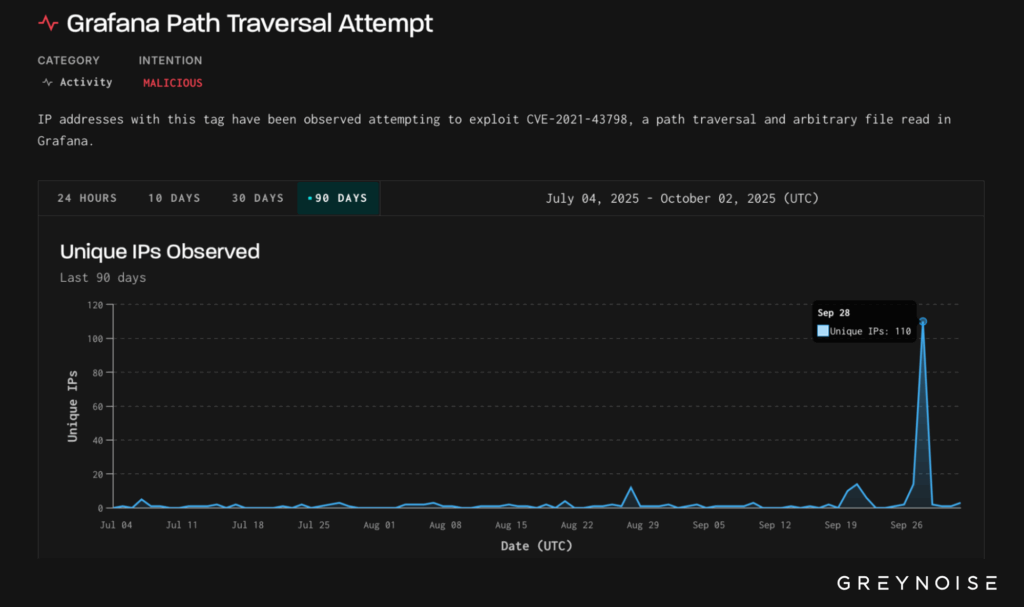
On 28 September, security researchers at GreyNoise detected a sudden spike in attempts to exploit CVE-2021-43798, a path traversal flaw that permits arbitrary file reads on unpatched instances.
Over the course of a single day, 110 unique malicious IPs probed the Global Observation Grid (GOG), all classified as adversarial, in what appears to be a concerted campaign to harvest sensitive configuration and credential files.
Grafana Exploitation Attempts
The previous months’ activity had been limited, but on September 28, attackers generated an upsurge of requests. A total of 110 unique IP addresses attempted exploitation. Destinations included only the United States, Slovakia, and Taiwan, adhering to a strict 3:1:1 distribution.
Bangladesh accounted for 107 of the source IPs, targeting U.S. endpoints 105 times, with the remaining two sources in China and one in Germany. Most IPs were first observed on the same day they launched their probes, suggesting disposable infrastructure.
Payloads followed a classic traversal pattern, for example:
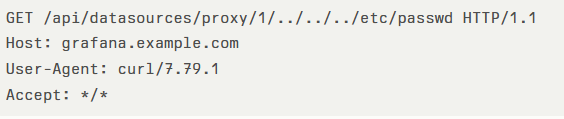
Responses returning system files or Grafana configuration data would reveal credentials or sensitive settings, enabling further compromise of monitored environments.
Traffic analysis uncovered two notable patterns: a uniform geographic targeting ratio and convergence of tooling fingerprints.
Bangladesh-based scanners hit U.S. hosts 100 times, Slovakia once, and Taiwan once; similar 3:1:1 ratios were observed from China and Germany.
The top TCP and HTTP fingerprints distinct sets of TLS JA3 hashes and User-Agent strings mapped similarly across destinations, indicating that attack kits were shared or orchestrated centrally rather than by different actors.
Two China-hosted IPs, 60.186.152.35 and 122.231.163.197, both under CHINANET-BACKBONE, were active exclusively on 28 September and focused solely on Grafana path traversal probes, GreyNoise said.
Exploitation of older, high–impact flaws remains prevalent. Path traversal bugs in Grafana have featured in SSRF waves and account takeover toolkits, and attackers frequently integrate them into multi-stage exploit chains.
The resurgence of CVE-2021-43798 demonstrates that even patched or deprecated vulnerabilities demand ongoing vigilance.
Mitigations
Ensure all Grafana deployments are updated to the latest secure release, mitigating CVE-2021-43798. Inspect web server logs for unauthorized traversal requests and audit any returned file contents for unauthorized access.
Block the 110 malicious IPs identified on 28 September and consider implementing dynamic IP blocklists with JA3/JA4 signature support.
By maintaining rigorous patch management and proactive log analysis, organizations can defend against the resurgence of legacy vulnerabilities and disrupt coordinated exploitation efforts.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.




