Hackers Bombard Open Source Repositories with Over 144,000 Malicious Packages
NuGet, PyPi, and npm ecosystems are the target of a new campaign that has resulted in over 144,000 packages being published by unknown threat actors.
“The packages were part of a new attack vector, with attackers spamming the open source ecosystem with packages containing links to phishing campaigns,” researchers from Checkmarx and Illustria said in a report published Wednesday.
Of the 144,294 phishing-related packages that were detected, 136,258 were published on NuGet, 7,824 on PyPi, and 212 on npm. The offending libraries have since been unlisted or taken down.

Further analysis has revealed that the whole process was automated and that the packages were pushed over a short span of time, with a majority of the usernames following the convention “
The fake packages themselves claimed to provide hacks, cheats, and free resources in an attempt to trick users into downloading them. The URLs to the rogue phishing pages were embedded in the package description.
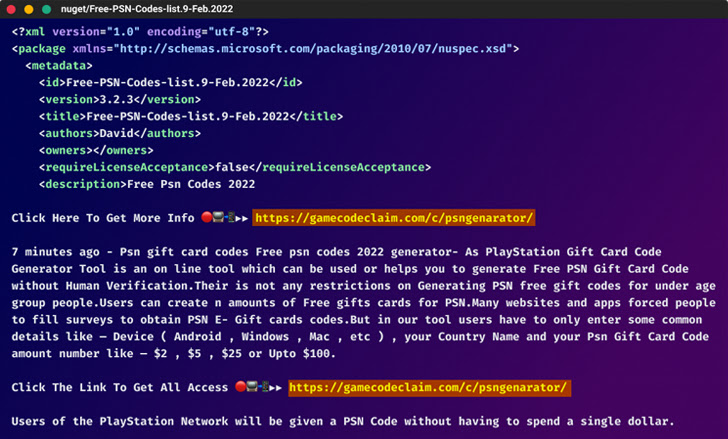
In all, the massive campaign encompassed more than 65,000 unique URLs on 90 domains.
“The threat actors behind this campaign likely wanted to improve the search engine optimization (SEO) of their phishing sites by linking them to legitimate websites like NuGet,” the researchers said. “This highlights the need to be cautious when downloading packages and only to use trusted sources.”
These deceptive and well-designed pages advertised Discord Nitro codes, game hacks, “free money” for Cash App accounts, gift cards, and increased followers on social media platforms like YouTube, TikTok, and Instagram.
The sites, as is typically the case, don’t offer the promised rewards, instead prompting users to enter their email addresses and complete surveys, before redirecting them to legitimate e-commerce sites via an affiliate link to generate illicit referral revenues.
The poisoning of NuGet, PyPi, and npm with fabricated packages once again illustrates the evolving methods threat actors use to attack the software supply chain.
“Automating the process also allowed the attackers to create a large number of user accounts, making it difficult to trace the source of the attack,” the researchers said. “This shows the sophistication and determination of these attackers, who were willing to invest significant resources in order to carry out this campaign.”