A critical vulnerability in Windows Boot Manager, known as bitpixie, enables attackers to bypass BitLocker drive encryption and escalate local privileges on Windows systems.
The vulnerability affects boot managers from 2005 to 2022 and can still be exploited on updated systems through downgrade attacks, posing significant risks to enterprise security.
Key Takeaways
1. Bitpixie lets attackers bypass BitLocker and escalate privileges.
2. Admin access is possible if a BitLocker PIN is known.
3. Patch KB5025885 is required to mitigate.
The BitPixie vulnerability stems from a flaw in the PXE (Preboot Execution Environment) soft reboot feature of the Windows Boot Manager, where the BitLocker Volume Master Key (VMK) is not properly erased from memory during the boot process.
This vulnerability is linked to CVE-2023-21563, which affects the boot manager’s handling of network boot operations.
Exploit bitpixie Windows Boot Manager Vulnerability
SySS Tech details that the exploitation process involves a sophisticated two-stage attack that targets the boot configuration and memory extraction mechanisms.
Attackers first craft a malicious Boot Configuration Data (BCD) file that specifies a recovery boot process loading from their controlled TFTP server.
This modified BCD file redirects the normal boot sequence to trigger a PXE soft reboot, which loads an attacker-controlled Linux environment while preserving the VMK in system memory.
The attack leverages the Trusted Platform Module (TPM) and Platform Configuration Registers (PCRs) used in the Windows Measured Boot process.
During normal operation, BitLocker relies on PCR registers 7 and 11 to validate boot integrity before unsealing the VMK from the TPM.
However, the bitpixie vulnerability allows attackers to circumvent this protection by exploiting the memory persistence during PXE soft reboot operations.
To extract the VMK from memory, attackers scan for the specific byte pattern -FVE-FS- (hex: 2d 46 56 45 2d 46 53 2d) which marks the beginning of the BitLocker metadata area.
The VMK itself is identified by the byte signature 03 20 01 00 followed by the 32-byte encryption key. Once extracted, this key can be used to unlock the entire BitLocker-encrypted partition, granting administrative access to the system.
Even systems protected with BitLocker Pre-Boot Authentication (PBA) and PIN requirements remain vulnerable to privilege escalation attacks.
Research demonstrates that malicious insiders with knowledge of the BitLocker PIN can exploit bitpixie to gain local administrative privileges on their assigned systems.
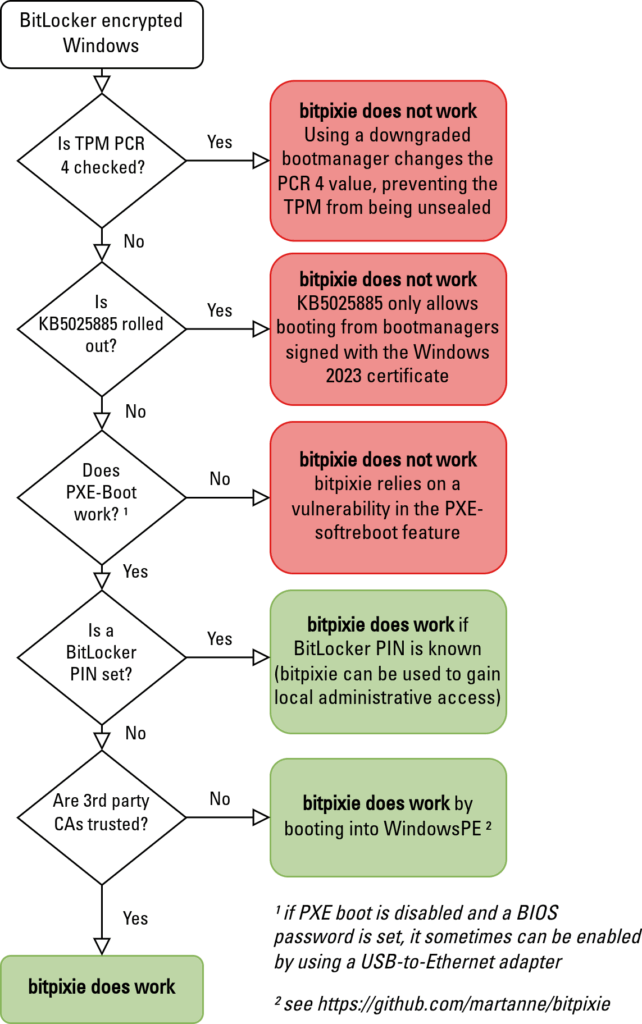
The attack succeeds because the PIN validation occurs before the vulnerable memory handling, allowing the VMK to be extracted even from PIN-protected systems.
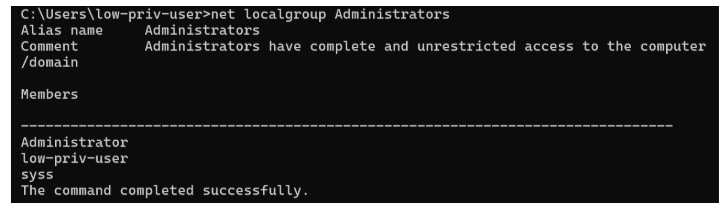
Attackers can then modify Windows registry files, such as the Security Account Manager (SAM) database, to add low-privilege user accounts to the Administrators group.
This technique enables lateral movement and persistent access within corporate environments.
The vulnerability affects multiple VMK protection types, with different byte signatures observed for various configurations:
- Standard TPM protection: 03 20 01 00
- TPM with PIN protection: 03 20 11 00 or 03 20 05 00
- Recovery password protection: 03 20 08 00
Mitigations
Microsoft has released KB5025885 as the primary mitigation for bitpixie and related boot manager vulnerabilities.
This update replaces the vulnerable Microsoft Windows Production PCA 2011 certificate with the new Windows UEFI CA 2023 certificate, preventing downgrade attacks to vulnerable boot managers.
The patch adds new certificate authorities to the UEFI Secure Boot database and revokes the 2011 certificate by adding it to the Database of eXcluded signatures (DBX).
Organizations should implement comprehensive defense strategies, including mandatory BitLocker PBA with strong PINs, updated PCR validation configurations, and network segmentation to prevent PXE boot attacks.
The Microsoft certificate update becomes mandatory in 2026 when the current certificates expire, making early deployment critical for identifying compatibility issues before the forced transition.
Security teams should monitor for unauthorized PXE boot attempts, implement physical security controls for workstations, and ensure BitLocker recovery keys are securely managed through enterprise key management systems.
The vulnerability demonstrates the importance of hardware-based security controls and the ongoing evolution of boot-level attack techniques targeting modern encryption implementations.
Free live webinar on new malware tactics from our analysts! Learn advanced detection techniques -> Register for Free
