On the first day of Pwn2Own Ireland 2025, security researchers exploited 34 unique zero-days and collected $522,500 in cash awards.
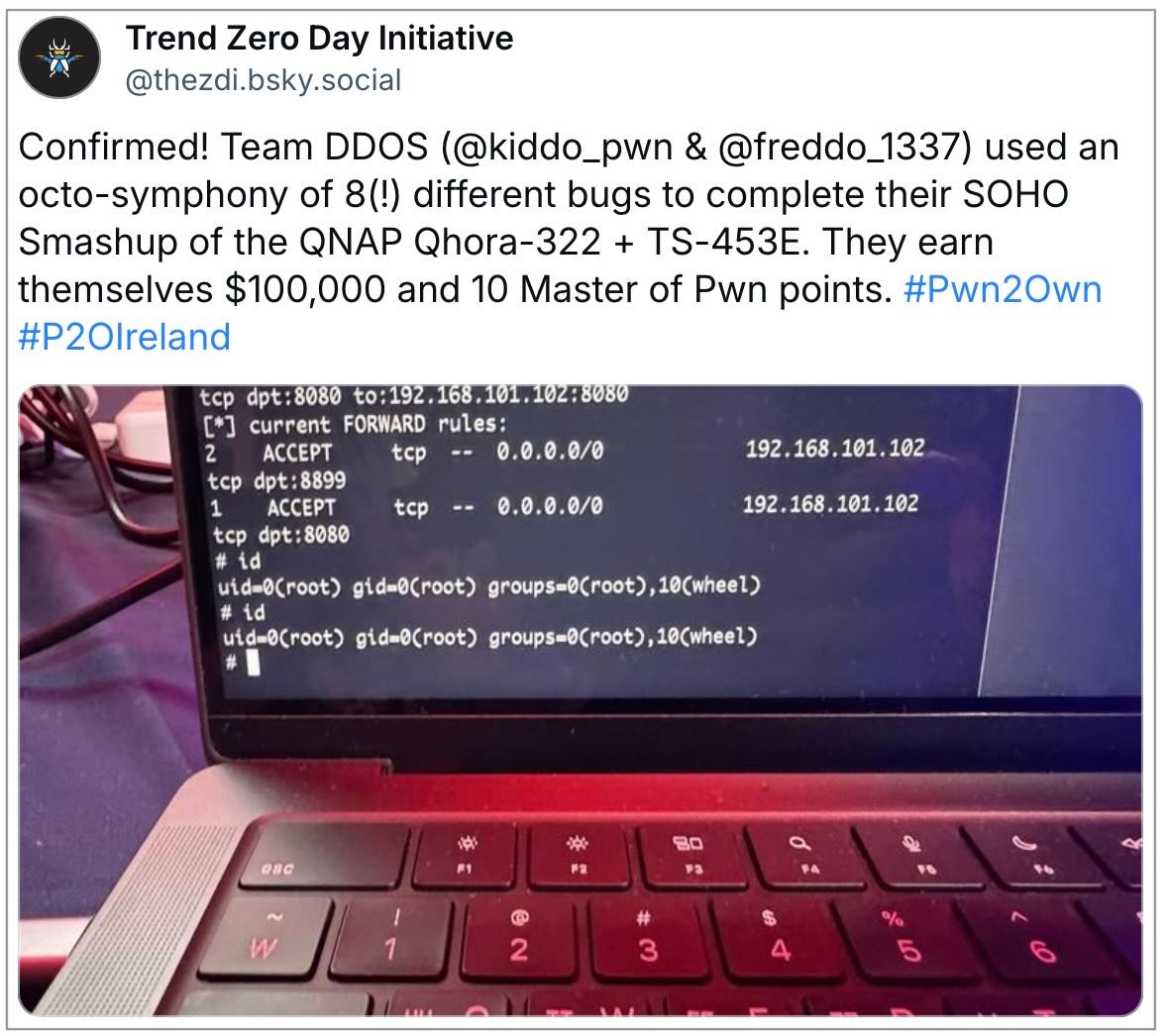
The highlight of the day was Bongeun Koo and Evangelos Daravigkas of Team DDOS chaining eight zero-day flaws to hack the QNAP Qhora-322 Ethernet wireless router via the WAN interface and gain access to a QNAP TS-453E NAS device. For this successful attempt, they won $100,000 and are now in second place on the Master of Pwn leaderboard with 8 points.
Synacktiv Team, Sina Kheirkhah of the Summoning Team, the DEVCORE Team, and Stephen Fewer of Rapid7 have also earned $40,000 each after gaining root on the Synology BeeStation Plus, the Synology DiskStation DS925+, the QNAP TS-453E, and the Home Assistant Green, respectively.
STARLabs, Team PetoWorks, Team ANHTUD, and Ierae researchers hacked the Canon imageCLASS MF654Cdw multifunction laser printer four times, while STARLabs also hacked the Sonos Era 300 smart speaker to earn $50,000, and Team ANHTUD exploited the Phillips Hue Bridge to collect $40,000 in cash.
Sina Kheirkhah and McCaulay Hudson of the Summoning Team have used an exploit chain combining two zero-days to gain root on a Synology ActiveProtect Appliance DP320 and win another $50,000.
Summoning Team won a total of $102,500 during the first day of the competition and is at the top of the Master of Pwn leaderboard with 11.5 points.
The Zero Day Initiative (ZDI) operates the event to identify security vulnerabilities in targeted devices before threat actors can exploit them, coordinating responsible disclosure with the affected vendors.
After the zero-day flaws are exploited during Pwn2Own events, vendors are given 90 days to release security updates before Trend Micro’s Zero Day Initiative publicly discloses them.
The Pwn2Own Ireland 2025 hacking competition features eight categories targeting flagship smartphones (Apple iPhone 16, Samsung Galaxy S25, and Google Pixel 9), messaging apps, smart home devices, printers, home networking equipment, network storage systems, surveillance equipment, and wearable technology (including Meta’s Ray-Ban Smart Glasses and Quest 3/3S headsets).
This year, the ZDI also expanded the attack vectors for the mobile category to include USB port exploitation for mobile handsets, which requires competitors to hack into locked phones through physical connections. However, traditional wireless protocols such as Bluetooth, Wi-Fi, and near-field communication (NFC) remain valid attack vectors.
On the second day, security researchers will again target devices in the network-attached storage, printers, smart home, and surveillance systems categories, as well as the Samsung Galaxy S25 in the mobile phones category.
As announced in August, this is also the first time ZDI will offer a $1 million reward to security researchers who demo a zero-click WhatsApp exploit that allows code execution without user interaction.
Meta, alongside QNAP and Synology, is co-sponsoring the Pwn2Own Ireland 2025 hacking contest, which takes place from October 21 to October 24 in Cork, Ireland.
During last year’s Pwn2Own Ireland event, security researchers earned $1,078,750 for more than 70 zero-day vulnerabilities, with Viettel Cyber Security collecting $205,000 for QNAP, Sonos, and Lexmark bugs.
In January 2026, the ZDI will return to the Automotive World technology show in Tokyo for its third Pwn2Own Automotive contest, with Tesla returning as a sponsor.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
