The ransomware actor ‘ShadowSyndicate’ was observed scanning for servers vulnerable to CVE-2024-23334, a directory traversal vulnerability in the aiohttp Python library.
Aiohttp is an open-source library built on top of Python’s asynchronous I/O framework, Asyncio, to handle large amounts of concurrent HTTP requests without traditional thread-based networking.
It is used by tech firms, web developers, backend engineers, and data scientists looking to build high-performance web applications and services that aggregate data from multiple external APIs.
On January 28, 2024, aiohttp released version 3.9.2, addressing CVE-2024-23334, a high-severity path traversal flaw impacting all versions of aiohttp from 3.9.1 and older that allows unauthenticated remote attackers to access files on vulnerable servers.
The flaw is due to inadequate validation when ‘follow_symlinks’ is set to ‘True’ for static routes, allowing unauthorized access to files outside the server’s static root directory.
On February 27, 2024, a researcher released a proof of concept (PoC) exploit for CVE-2024-23334 on GitHub, while a detailed video showcasing step-by-step exploitation instructions was published on YouTube at the start of March.
Cyble’s threat analysts report that their scanners have caught exploitation attempts targeting CVE-2024-23334 starting on February 29 and continuing at an increased rate into March.
The scanning attempts originate from five IP addresses, one of which was tagged in a September 2023 report by Group-IB, who linked it to the ShadowSyndicate ransomware actor.
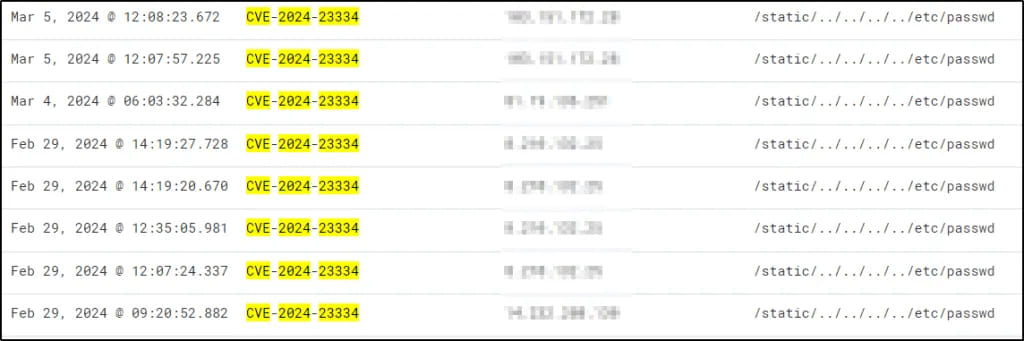
ShadowSyndicate is an opportunistic, financially-motivated threat actor, active since July 2022, who was linked with various degrees of confidence to ransomware strains such as Quantum, Nokoyawa, BlackCat/ALPHV, Clop, Royal, Cactus, and Play.
Group-IB believes the threat actor is an affiliate working with multiple ransomware operations.
Cyble’s finding, though not definitive, indicates that the threat actors might be carrying out scans targeting servers using a vulnerable version of the aiohttp library. Whether or not these scans turn into breaches remains unknown at this time.
Regarding the attack surface, Cyble’s internet scanner ODIN shows there are roughly 44,170 internet-exposed aiohttp instances around the world. Most (15.8%) are located in the United States, followed by Germany (8%), Spain (5.7%), the UK, Italy, France, Russia, and China.
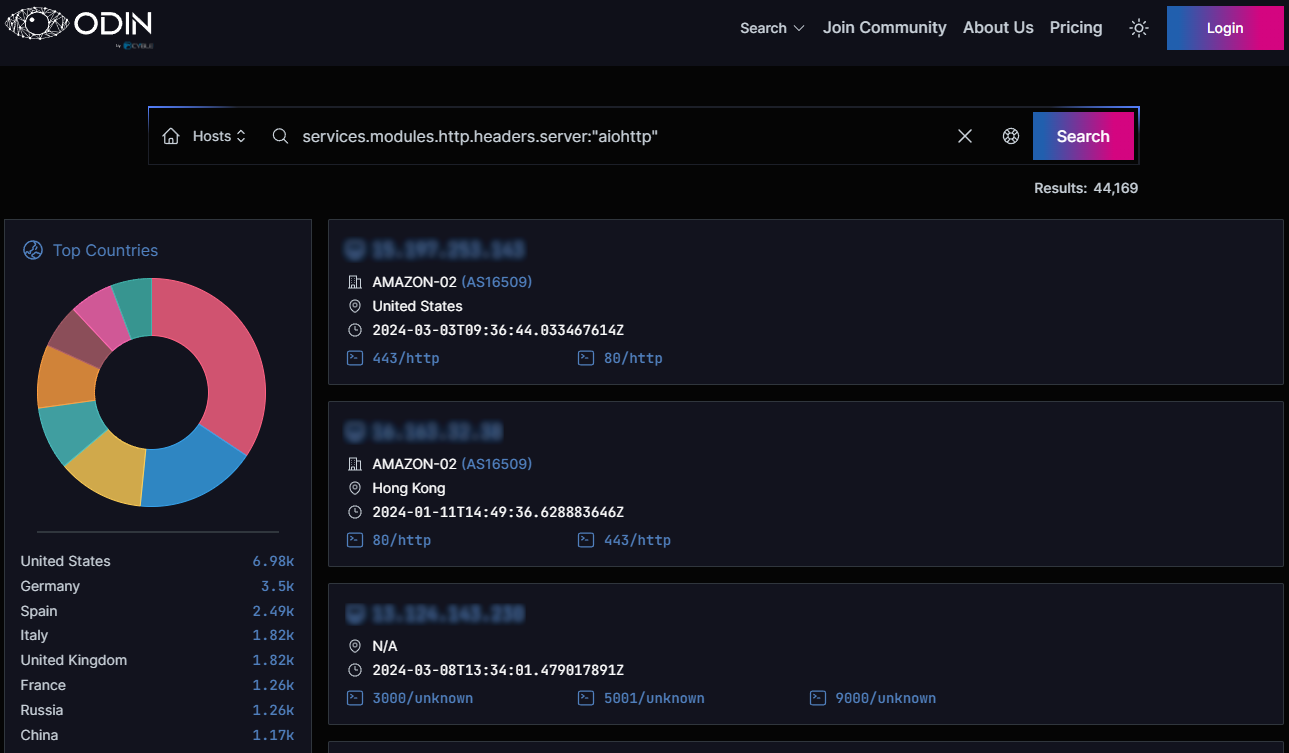
The version of the internet-exposed instances run cannot be discerned, making it hard to determine the number of vulnerable aiohttp servers.
Unfortunately, open-source libraries are often used in outdated versions for extended periods due to various practical issues that complicate locating and patching them.
This makes them more valuable to threat actors, who leverage them in attacks even after years have passed since a security update was made available.




