LAC’s Cyber Emergency Center has identified a sophisticated cyberespionage campaign targeting Japanese shipping and transportation companies.
The operation, orchestrated by a China-based threat actor in April 2025, leveraged critical vulnerabilities in Ivanti Connect Secure (ICS) to deploy “MetaRAT,” a newly identified variant of the notorious PlugX malware family.
This campaign highlights the persistent evolution of Chinese state-linked threat actors, with forensic evidence pointing toward groups such as Space Pirates or Calypso, known for targeting Asian infrastructure.
The Attack Chain
The intruders gained access by exploiting two high-severity vulnerabilities in Ivanti Connect Secure: CVE-2024-21893 (server-side request forgery) and CVE-2024-21887 (command injection).
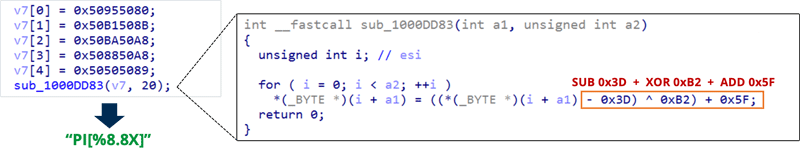
MetaRAT strings are obfuscated using either the TEA cipher or SUB+XOR+ADD (Subtraction Exclusive Or Addition), the former obfuscating 21 strings and the latter obfuscating 24 strings.
Forensic analysis of compromised systems revealed a surge in critical error logs (code “ERR31093”) and the creation of suspicious files consistent with previous Mandiant-identified attacks.
Once inside the network, the attackers pivoted laterally using compromised Active Directory credentials. To maintain persistence and exfiltrate data, they deployed two distinct malware strains: MetaRAT and Talisman.
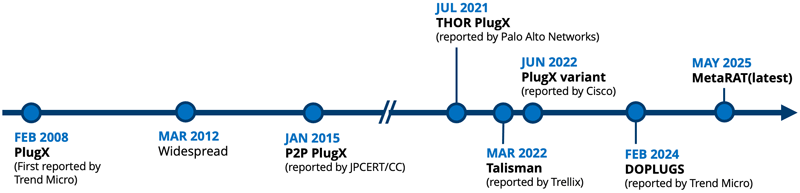
While PlugX has been a staple of Chinese cyberespionage since 2008, MetaRAT represents a significant evolution.
Though LAC researchers trace its origins back to 2022, the 2025 campaign utilized a refined version designed to evade detection.
MetaRAT operates via DLL side-loading, where a legitimate application inadvertently loads a malicious DLL (mytilus3.dll).

This loader decrypts a shellcode payload (materoll), which then injects the malware into memory. Key features distinguishing MetaRAT from standard PlugX variants include:
- Custom Encryption: It uses AES-256-ECB encryption and Gzip compression for its configuration and communication data.
- Unique C2 Protocols: The malware supports multiple communication protocols (TCP, UDP, HTTP, HTTPS, ICMP) and utilizes unique “cookie” headers in HTTP traffic to blend in with legitimate traffic.
- Expanded Capabilities: MetaRAT includes advanced plugins for keylogging and port mapping, allowing attackers to tunnel deeper into the victim’s network.
The Talisman Connection
Alongside MetaRAT, the attackers deployed Talisman, another PlugX variant previously linked to groups like RedFoxtrot and Mustang Panda.
The simultaneous use of both malware strains, along with shared code structures and debug paths found in their loaders, strongly suggests a unified operation.
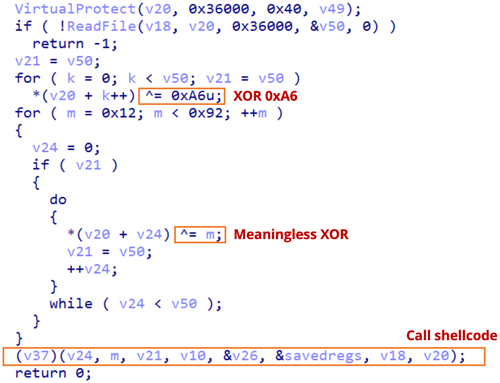
The operation of this loader is very simple. First, it reads the encrypted file “materoll” and decrypts it using XOR with 0xA6.
Forensic analysis revealed that the Talisman samples in this campaign used modified “Magic Values” in their headers, a likely attempt to bypass security scanners.
This campaign underscores the critical need for organizations to patch edge devices like Ivanti Connect Secure immediately.
The attackers’ ability to modify well-known tools like PlugX allows them to bypass standard antivirus signatures.
Security teams are advised to monitor for specific indicators of compromise (IOCs), including:
- Registry Keys: Auto-start keys named “matesile.”
- Files: Suspicious files such as mytilus3.dll, materoll, and keylog files named VniFile.hlp.
- Network Traffic: HTTP requests containing “Cookie-Yaga” or “Cookie-Nguy” headers.
LAC’s findings were presented at the Virus Bulletin Conference 2025 and the Threat Analyst Summit 2025, warning that while the tools evolve, the strategic targeting of critical infrastructure remains a constant threat.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
