Hackers are trying to exploit CVE-2024-52875, a critical CRLF injection vulnerability that leads to 1-click remote code execution (RCE) attacks in GFI KerioControl firewall product.
KerioControl is a network security solution designed for small and medium-sized businesses that combines firewall, VPN, bandwidth management, reporting and monitoring, traffic filtering, AV protection, and intrusion prevention.
On December 16, 2024, security researcher Egidio Romano (EgiX) published a detailed writeup on CVE-2024-52875, demonstrating how a seemingly low-severity HTTP response splitting problem could escalate to 1-click RCE.
The vulnerability, which impacts KerioControl versions 9.2.5 through 9.4.5, is due to improper sanitization of line feed (LF) characters in the ‘dest’ parameter, allowing HTTP header and response manipulation via injected payloads.
Malicious JavaScript injected into responses is executed on the victim’s browser, leading to the extraction of cookies or CSRF tokens.
An attacker could use the CSRF token of an authenticated admin user to upload a malicious .IMG file containing a root-level shell script, leveraging the Kerio upgrade functionality, which opens a reverse shell for the attacker.
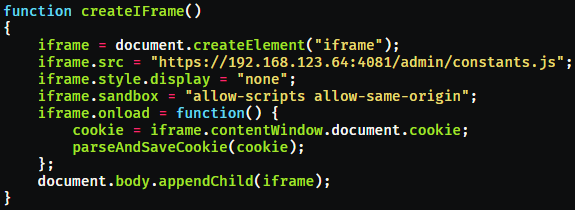
Source: karmainsecurity.com
Active exploitation
Yesterday, threat scanning platform Greynoise detected exploitation attempts targeting CVE-2024-52875 from four distinct IP addresses, possibly using the PoC exploit code presented by Romano.
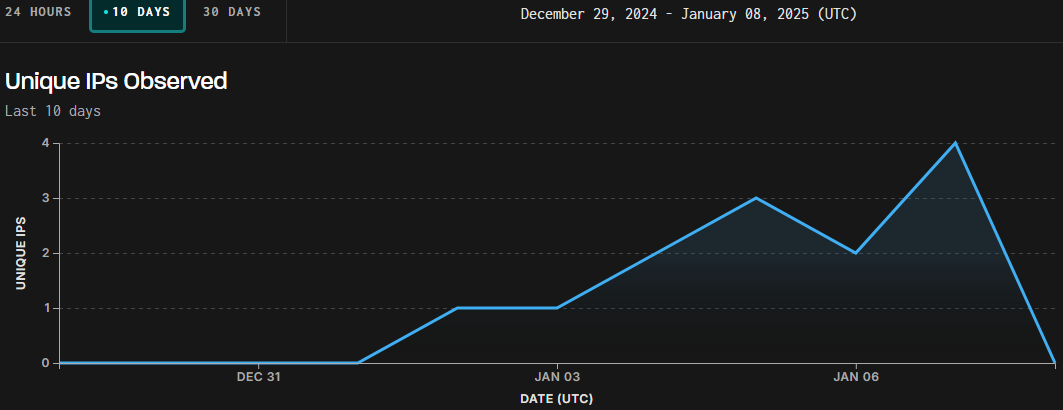
Source: Greynoise
The activity is marked as “malicious” by the threat monitoring platform, indicating that the exploitation attempts are attributed to threat actors rather than researchers probing systems.
Also yesterday, Censys reported 23,862 internet-exposed GFI KerioControl instances, although it is unclear how many of them are vulnerable to CVE-2024-52875 is unknown.
Source: Censys
GFI Software on December 19, 2024, released version 9.4.5 Patch 1 for the KerioControl product, which addresses the vulnerability . Users are recommended to apply the fix as soon as possible.
If patching is not possible at the moment, admins should limit access to KerioControl’s web management interface to trusted IP addresses and disable public access to the ‘/admin’ and ‘/noauth’ pages via firewall rules.
Monitoring for exploitation attempts targeting the ‘dest’ parameters and configuring shorter session expiration times are also effective mitigations.
