In recent years, adversaries have abandoned traditional malware in favor of “living-off-the-land” operations against cloud and SaaS environments.
Rather than deploying custom ransomware binaries, many threat actors now exploit misconfigured database services—leveraging only built-in commands to steal, destroy, or encrypt data.
Victims often discover their data missing or inaccessible, replaced only by ransom notes stored within the database itself. This malware-less approach has grown from isolated incidents into highly automated campaigns that prey on exposed databases worldwide.
Classic ransomware typically requires delivering a malicious payload to encrypt files on disk. By contrast, database ransomware uses normal queries—such as DROP, DELETE, or EXPORT—to render data unavailable and then holds backups hostage.
Attackers scan the Internet for open ports (MySQL on 3306, PostgreSQL on 5432, MongoDB on 27017, and others), test weak or default credentials, and upon authentication, exfiltrate data to attacker-controlled hosts.
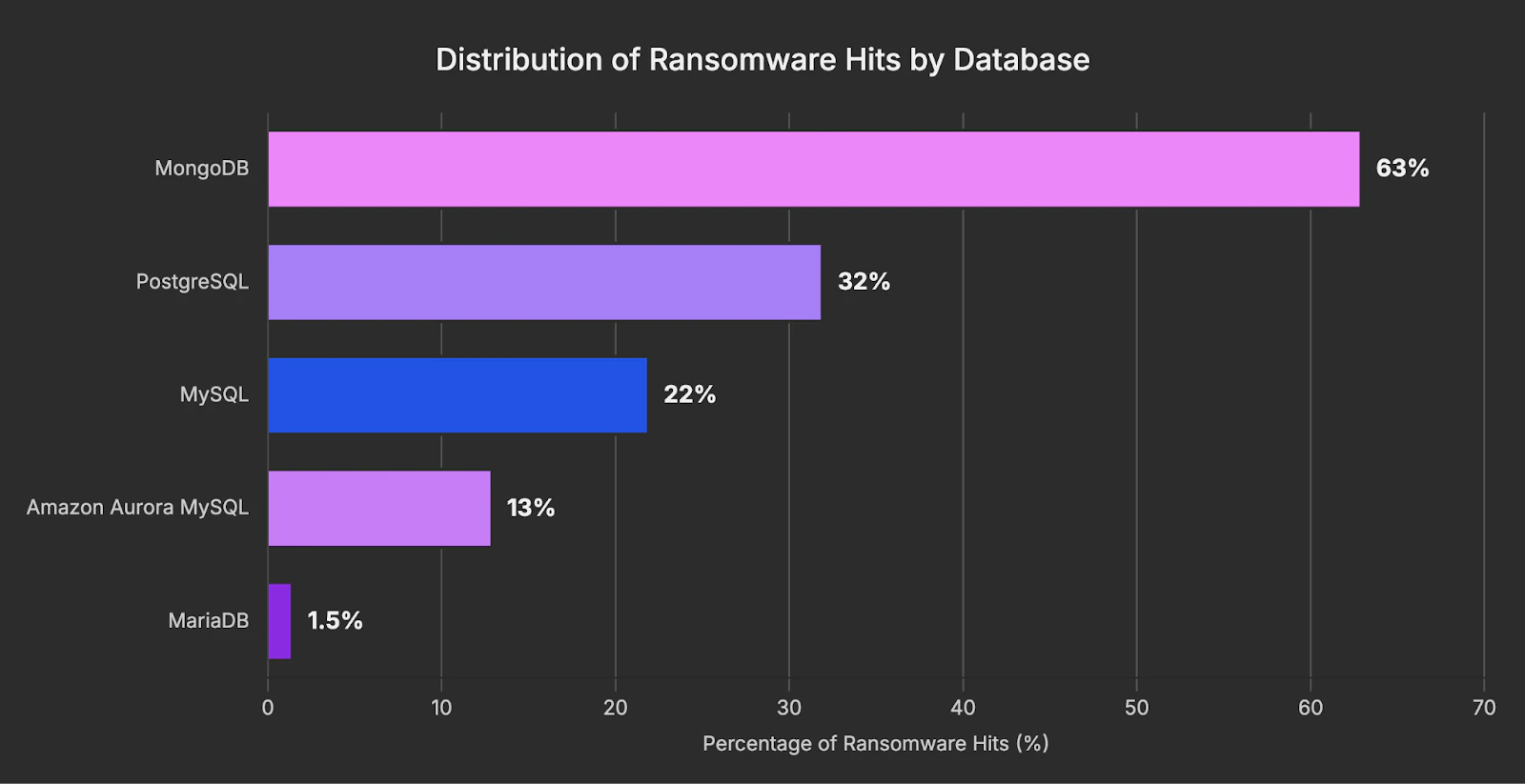
They then wipe the database and create a table or collection named README_TO_RECOVER or RECOVER_YOUR_DATA containing a ransom demand. Because no foreign binary is ever installed, endpoint security tools often fail to detect any malicious activity.
Threat researchers first documented large-scale database hijacking as early as February 2017, when thousands of unprotected instances were compromised in bulk.
Today, specialized bots continuously scour new hosts, compromising fresh targets within minutes of exposure. The combination of automation and the ease of exploiting simple misconfigurations has made malware-less database extortion a persistent threat.
Double Extortion and Escalation
Recent campaigns have adopted double extortion tactics, threatening to publish stolen data if ransoms go unpaid—even if actual exfiltration is unverified.
By mirroring broader ransomware strategies without ever deploying a payload, these actors amplify pressure on victims to comply.
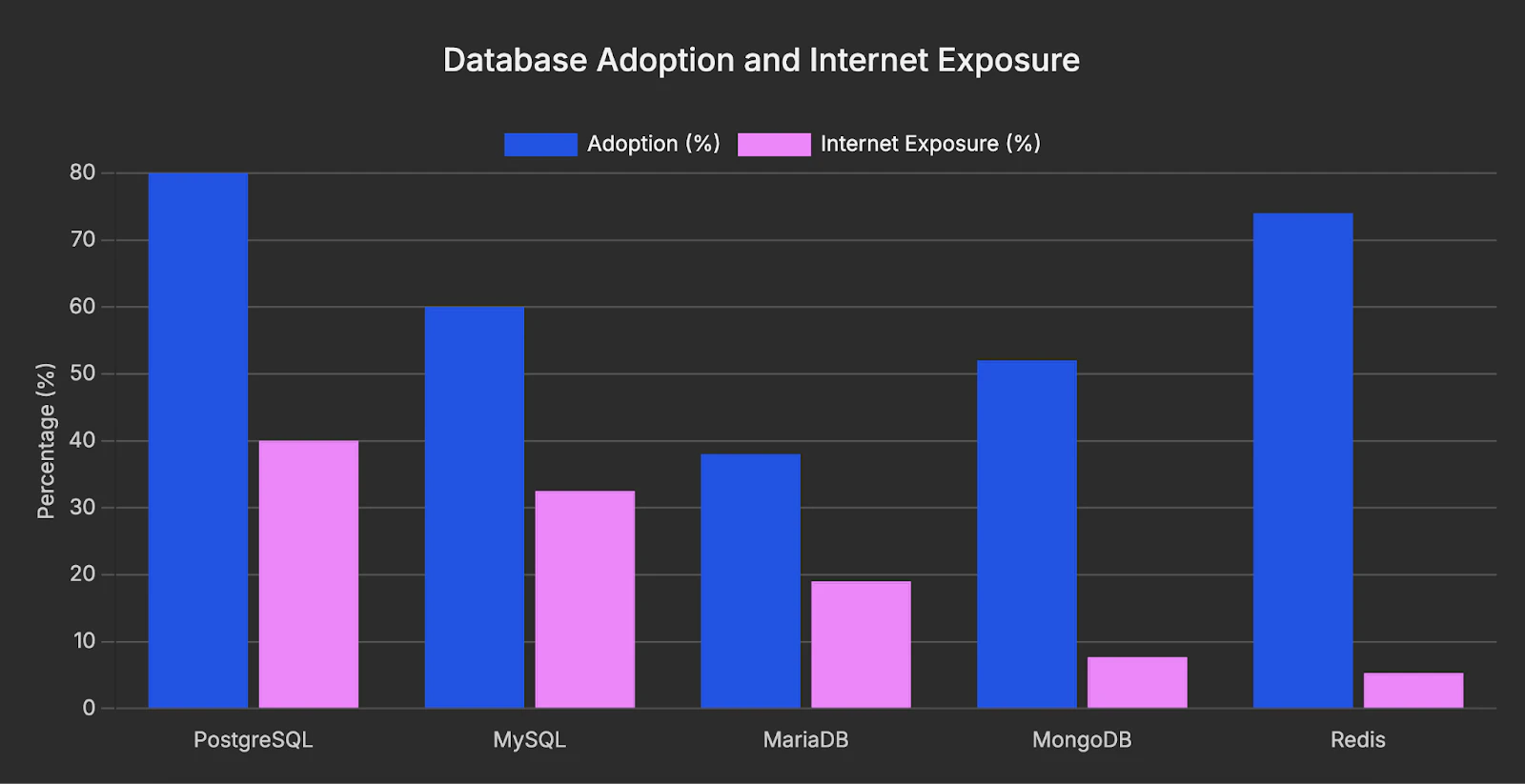
An outlier in the dataset is Redis, which has relatively low exposure (5.3% of environments) despite its widespread popularity (74% of environments).

Beyond data extortion, successful database takeover can enable privilege escalation to achieve remote code execution (RCE).
Once attackers gain administrative SQL rights, they may deploy stored procedures or leverage server features to run shell commands, pivot to other hosts, and establish persistent footholds.
Thus, a ransom note lodged in a database often signals a deeper compromise, with potential for lateral movement and long-term data theft.
Preventative measures start with network segmentation. Database servers should reside on private networks, shielded by firewalls and security groups that only allow application-server traffic. Direct Internet exposure of database ports must be eliminated.
In one high-profile MySQL attack, adversaries posted victims’ database dumps on dark-web auction sites to coerce payment. Ransom notes warn that nonpayment will result in public data leaks or sales to the highest bidder.
The Wiz Dynamic Scanner continuously evaluates security posture, while IOC detection rules alert on suspicious ransom-note artifacts. By combining prevention with vigilant detection, organizations can thwart malware-less extortion campaigns and protect critical data assets.


When remote administration is necessary, access should route through a hardened jump server protected by multi-factor authentication rather than opening DB ports publicly.
Authentication controls are equally critical. Disable passwordless login, enforce strong, unique credentials, and require MFA for administrative accounts.
Regularly audit configurations to ensure default usernames and weak passwords are eradicated. To mitigate potential data loss, implement robust backup strategies: schedule frequent backups, validate recoverability, and store archives in separate, access-controlled locations.
Detecting database ransomware involves continuous monitoring for Indicators of Compromise (IOCs). Automated scans should flag newly created tables or collections named to suggest ransom notes.
Anomalous bulk DELETE or DROP operations, especially outside normal maintenance windows, warrant immediate investigation. Proactive attack surface mapping can reveal unintended exposures before adversaries strike.
Wiz customers benefit from agentless scanning that identifies public database instances and misconfigurations in real time.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
