Researchers have uncovered a sophisticated malware campaign where threat actors weaponize trojanized installers for popular productivity applications to deploy ValleyRat, a persistent remote access tool.
The operation demonstrates advanced evasion techniques, including kernel-level driver abuse, endpoint security tampering, and multi-stage obfuscation designed to evade detection and establish long-term system compromise.
The campaign has been attributed to Silver Fox, a China-aligned advanced persistent threat (APT) group active since at least 2022.
The threat actors repurpose legitimate installer files for Telegram, WinSCP, Google Chrome, and Microsoft Teams applications that users regularly download and trust.
Upon execution, victims observe a standard installation interface while malware silently stages payloads, deploys kernel drivers, turns off security defenses, and launches a ValleyRat beacon that grants adversaries persistent remote access.
The Infection Chain
The attack unfolds through a meticulously coordinated sequence. Initial compromise occurs when victims execute a trojanized Telegram installer (tg.exe) distributed via spear-phishing and malvertising campaigns.
The binary, masquerading as Telegram Desktop version 6.0.2, displays a legitimate user interface while immediately executing malicious post-exploitation activities.
Upon launch, the installer creates the staging directory C:ProgramDataWindowsData and deploys a renamed 7-Zip binary alongside a password-protected archive disguised as main.xml.
Critically, the installer then uses PowerShell to add a Microsoft Defender exclusion for the entire C: drive a dangerous configuration change that disables antivirus protection system-wide.
The archive is subsequently extracted using the command-line password htLcENyRFYwXsHFnUnqK, yielding a second-stage orchestrator binary named men.exe.
The men.exe component orchestrates subsequent infection stages. It enumerates running processes to identify security software, including Microsoft Defender and Chinese security products such as ZhuDongFangYu and 360tray indicating geographic targeting.
The orchestrator then deploys additional password-protected archives containing drivers, privilege escalation tools, persistence mechanisms, and the ValleyRat payload to %PUBLIC%DocumentsWindowsData.
Defense Evasion and Persistence
The campaign employs multiple overlapping evasion techniques. A UAC bypass utility leverages the ICMLuaUtil elevated COM interface to escalate privileges.
Two kernel-mode drivers rwdriver.sys and the vulnerable but signed NSecKrnl64.sys operate at ring 0 to weaken endpoint protection.
The custom driver circumvents user-mode EDR hooks, interferes with logging mechanisms by overloading event forwarding pipelines, and repeatedly terminates security solution processes.
A legitimately signed executable (NtHandleCallback.exe) performs DLL sideloading to execute the malicious log.dll beacon.
Persistence is maintained through a scheduled task named WindowsPowerShell.WbemScripting.SWbemLocator deliberately mimicking legitimate Windows components.
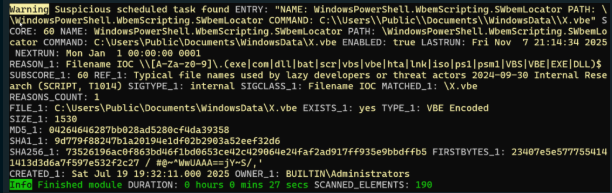
The task executes an encoded VBScript (X.vbe) at logon, which triggers both the vulnerable driver loader and the ValleyRat beacon.
Access control lists are modified to prevent even administrators from removing the staging directory, complicating remediation efforts.
Detection and Response
Despite its sophistication, the campaign presents multiple reliable detection opportunities. File system monitoring of C:ProgramDataWindowsData and %PUBLIC%DocumentsWindowsData identifies anomalous staging activities.
THOR detects these drivers via YARA signatures (for example, EXT_Winnti_Rootkit in related tooling), driver location checks and generic service analysis.

Microsoft Defender Operational event ID 5007 captures suspicious exclusion modifications. Process creation logs reveal password-protected archive extraction commands and UAC bypass CLSID invocations.
Service creation events expose kernel driver registration from user-writable directories.
Organizations should implement strict application control policies, restrict local administrator rights, monitor process execution from public user directories, and deploy comprehensive endpoint detection and response (EDR) solutions capable of detecting kernel-mode driver abuse and DLL sideloading techniques.
DNS logging and process-level C2 detection provide additional visibility into command-and-control communications used by the ValleyRat beacon.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
