Visual Studio is a powerful IDE from Microsoft that is primarily used for developing applications in various programming languages like “C#,” “C++,” and “Visual Basic.”
It offers a rich set of features like “debugging tools,” “a code editor with IntelliSense,” and “support for version control systems.”

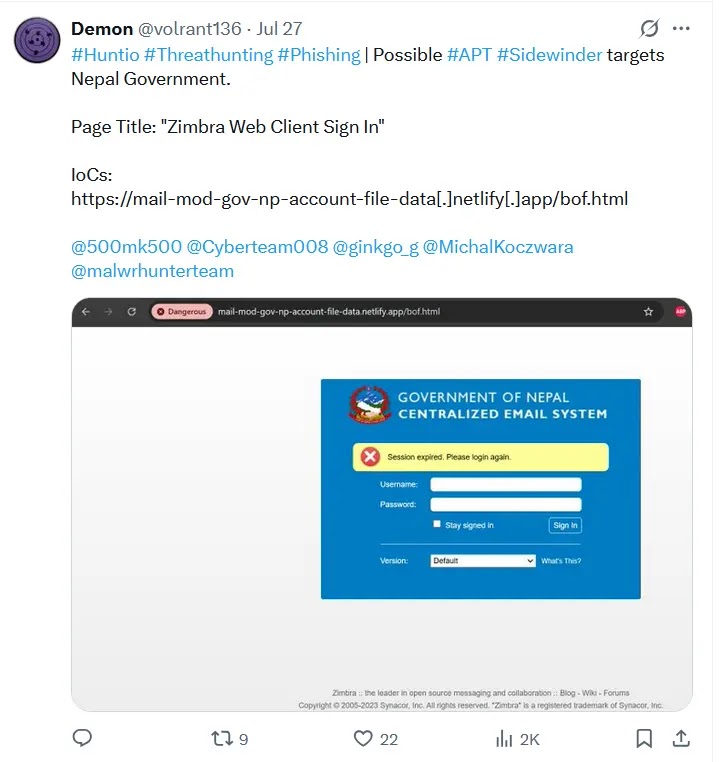
Milos (aka Ynwarcs) recently discovered an RCE vulnerability which is tracked as “CVE-2024-30052,” that enables hackers to exploit the “Visual Studio” via dump files.
Hackers Exploit Visual Studio Via Dump Files
Visual Studio developers routinely analyze dump files (“memory snapshots” of crashed programs) during ‘debugging sessions.’ But this common practice carries “security risks,” particularly when handling files from “untrusted sources.”
These dump files contain detailed program states and crash information, and they often originate from automated crash reporting systems like “Google’s Crashpad in Chrome,” and via “user-submitted support tickets.”
Analyse Any Suspicious Links Using ANY.RUN’s New Safe Browsing Tool: Try for Free
The vulnerability (“CVE-2024-30052,” patched in “Visual Studio 2022 17.8.11”) specifically involves “PDB files,” which store “debugging information” and can be embedded within “executables.”
When debugging managed dump files with “full heap memory,” the Visual Studio automatically processes embedded ‘PDBs’ containing source files especially those related to the “crash stack trace.”
The security concern arises from Visual Studio’s behavior when encountering non-printable characters in these files.
As it defaults to opening them using the operating system’s associated programs for specific file extensions (like “.hta,” “.chm,” and “.py”) that help in executing “malicious code.”
This vulnerability is concerning as it exploits legitimate features like the “Portable PDB format,” “embedded debugging symbols,” and “Visual Studio’s debug directory entries,” which makes it a sophisticated attack vector that evades traditional “memory corruption safeguards.”
.webp)
The process utilized “-debug:portable” compilation flags and involved modifying the PDB’s “document table hash” to evade the validation checks of Visual Studio.
The exploit worked by embedding the modified PDB into an executable which creates a “full-memory dump” (‘DumpType 2’), and triggering Visual Studio’s “Debug With Managed” functionality.
When debugging dump files, Visual Studio would attempt to open embedded sources through “external editors,” this Arbitrary Code Execution (ACE) through various file extensions associated with executables like “hh.exe” (for CHM), “mshta.exe” (for HTA), and “python.exe” (for PY files).
The vulnerability was especially effective since these file types could contain “non-printable characters” while maintaining their malicious functionality.
Besides this, the “CHM files could execute Visual Basic code,” “HTA files could run embedded scripts,” and “Python files could execute arbitrary commands through carefully crafted scripts with NUL characters.”
This security flaw was initially reported to Microsoft on August 14, 2023, and was initially categorized as “moderate impact” or “defense in depth,” but was later re-evaluated as “important.”
This led to its eventual patch release in “Visual Studio 17.8.11” on June 11, 2024, which implemented new security checks in the “CVsUIShellOpenDocument::OpenStandardEditor” function to prevent unauthorized file execution during debugging sessions.
Free Webinar on How to Protect Small Businesses Against Advanced Cyberthreats -> Free Registration