VASTFLUX, a large-scale well-organized, and sophisticated ad fraud operation were recently taken down by cybersecurity researchers at HUMAN Security Inc.
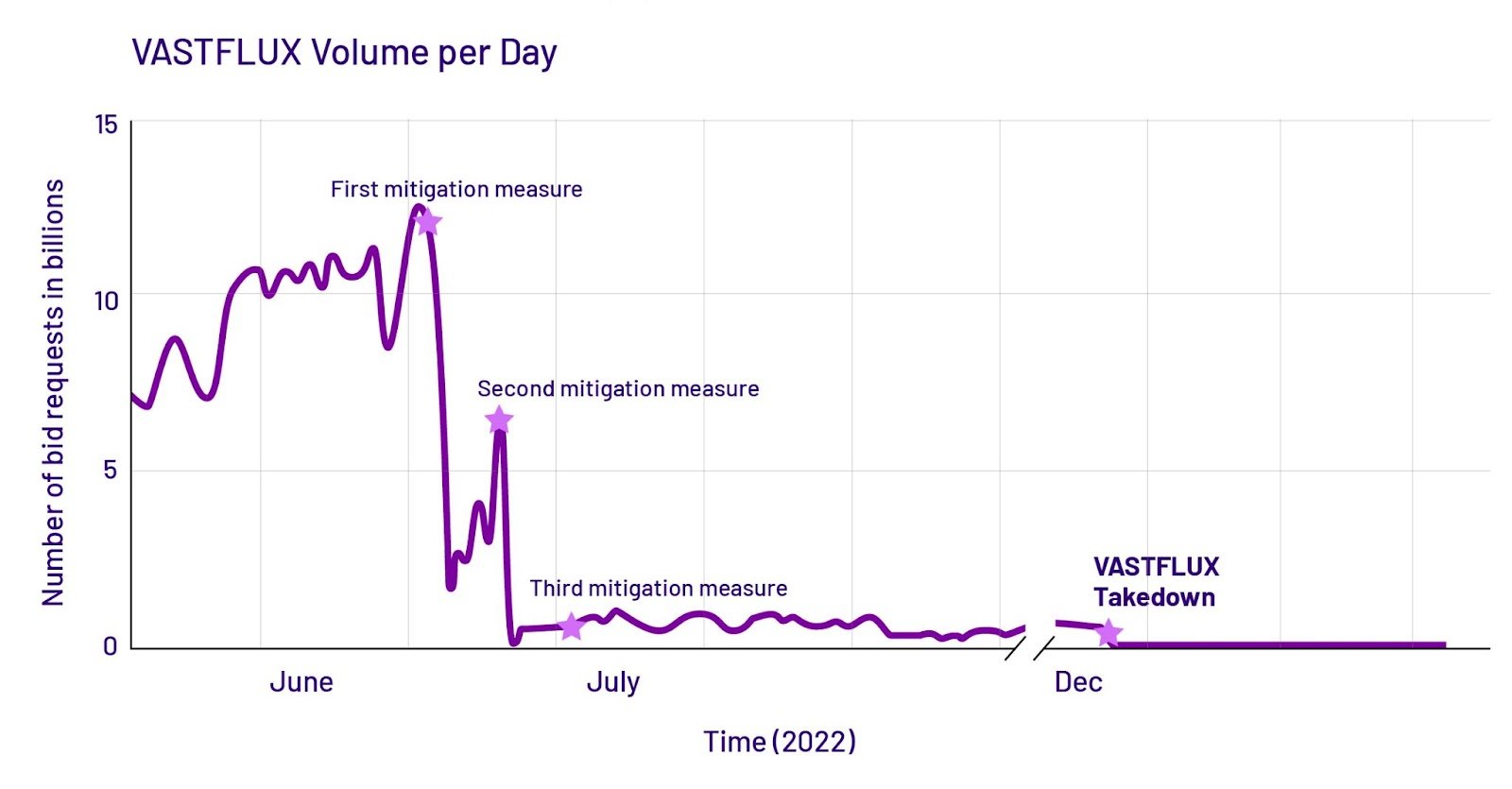
On a daily basis, 12 billion ads are requested by VASTFLUX, which was spoofing 1,700 apps on 11 million devices, targeting 120 publishers. Several key elements of collective protection are highlighted by VASTFLUX’s sophistication.
VASTFLUX is a malvertising operation in which the attackers manipulated ad creatives by injecting JavaScript and stacking multiple video players on top of each other, getting paid for all the ads even though none of them were visible to the user.
In order to avoid ad verification tags, VASTFLUX deployed a code that prevented the scheme from being detected.

Discovery of VASTFLUX Campaign
In terms of its function, VASTFLUX combines two terms. During this operation, the VAST template was exploited to deliver digital video ads. ‘Flux’ refers to the concept of Fast Flux, a technique used by cybercriminals as a way to evade detection and evade detection systems.
The operation was discovered by the Satori team from HUMAN while investigating the spoofing attack against an iOS application.
This study found that cybercriminals were exploiting the limited signal that made itself available to verification partners in a targeted environment which was exploited to build a highly sophisticated scheme. It is important to note that this includes in-app advertising primarily on iOS.
Eventually, the ad fraud progressed into spoofing bids on one platform to appear on another, resulting in the appearance of ads on both platforms. This made it impossible for cross-platform attacks to be deterred from taking place.
In an effort to get more insight into the fraud’s traffic volumes and the verification tags used to make sure the ads were genuine, Human partnered with its partners in the HUMAN Collective to gain further information.
VASTFLUX Operation
As a result of the attack, malicious JavaScript code was injected into digital advertisements. Fraudsters took advantage of this exploit by stacking up thousands of video ads on top of one another so they could register views for ads that were not seen by the user.
However, primarily it involves four steps, and here below we have mentioned them:-
- Step One: JavaScript Injection
- Step Two: C2 Instructions
- Step Three: A Playlist of Ads
- Step Four: Fraud Tracking Evasion
By implementing a private takedown effort, Human Security was able to bring an end to this operation. But, it is still being actively monitored by the company, as this will ensure further security.
Recommendations
Here below we have mentioned all the recommendations provided by the experts that users can apply to stay alert and mitigate:-
- In a short period of time, the battery life of the device deteriorates considerably.
- In the middle of the night, the device’s screen turns on unexpectedly.
- The performance of the device suddenly decreases.
- Depending on the day of the week, the amount of data being used jumps dramatically.
- Frequent and unexpected crash occurs.
It is true that VASTFLUX is down at this time, but it does not mean that the story is over. As the investigation continues, security analysts will be on the lookout for more clues as to who the perpetrators are as well as any future adaptations.
Network Security Checklist – Download Free E-Book
