Hackers are increasingly targeting verified accounts on X (formerly Twitter) belonging to government and business profiles and marked with ‘gold’ and ‘grey’ checkmarks to promote cryptocurrency scams.
A recent high-profile case is the X account of cyber threat intelligence company Mandiant, a Google subsidiary, which was hijacked yesterday to distribute a fake airdrop that emptied cryptocurrency wallets.
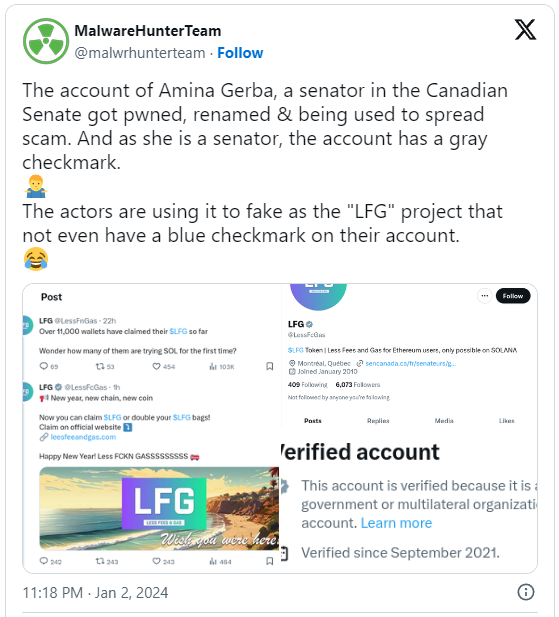
MalwareHunterTeam has been tracking this type of activity on X lately and reported several notable examples of compromised “gold” and “grey” accounts.
Only in the past couple of days, MHT has posted about the accounts of Canadian senator Amina Gerba, nonprofit consortium ‘The Green Grid,’ and Brazilian politician Ubiratan Sanderson falling in the hands of hackers.
A gold checkmark attached to an account on X indicates an official organization/company, while the grey badge marks profiles representing a government organization or an official.
Both types of accounts need to meet specific eligibility requirements. By contrast, the blue checks are given to any user paying for an X Premium subscription.
Due to the strict eligibility criteria, gold and grey “identity signals” inspire trust, and the content they distribute is typically considered more reliable.
While the promoted idea behind X’s verification and paid subscription system is to increase “by several orders of magnitude” the cost and difficulty for impersonation and scams, gold and grey badge accounts have become targets for hackers and a commodity for cybercriminals.
A recent report from CloudSEK, a digital risk monitoring platform, highlights the emergence of a new black market where hackers sell compromised gold and grey X accounts for prices between $1,200 and $2,000.
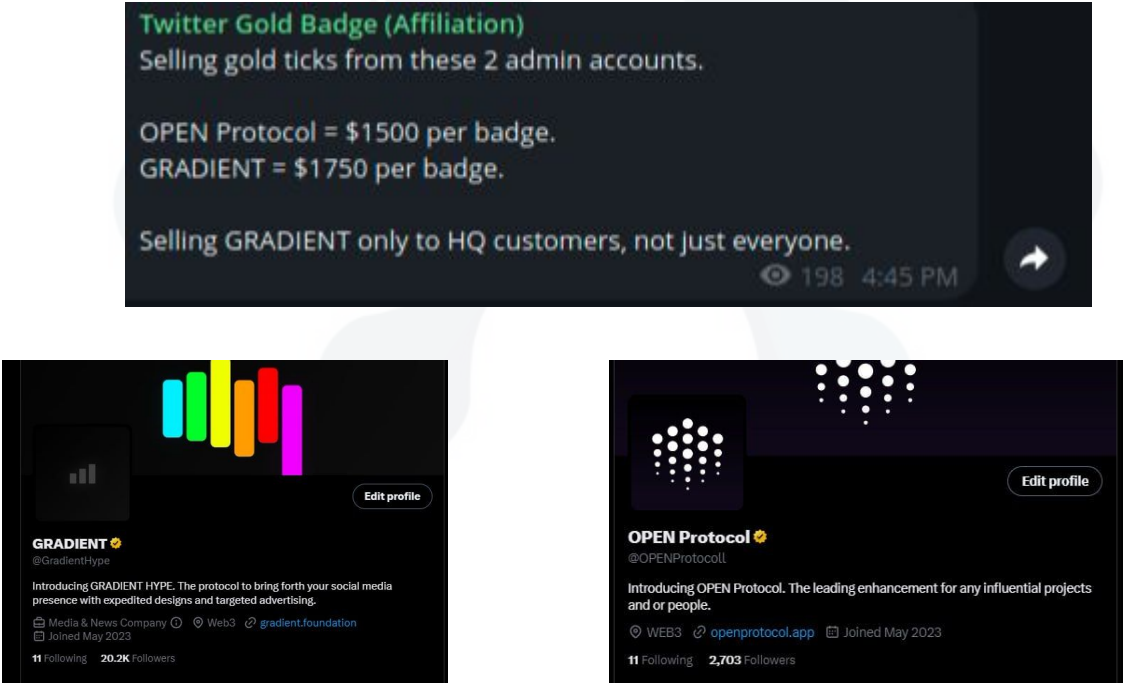
Some sellers also provide the option to add scam accounts as affiliates to the verified gold accounts for $500, lending them credibility without having to go through the more rigorous verification process from the social media platform.
Claims from threat actors on dark web markets and on Telegram suggest that the cybercriminals also work with compromised dormant corporate accounts that can be converted into “gold” profiles by the buyer.
In other cases, the hackers who compromise these accounts lock out their legitimate owners, subscribe to gold for 30 days, and pass the accounts to the new owners.
CloudSEK says it observed six sales of such accounts in a month. One of them, dormant since 2016 and with 28,000 followers, was advertised for $2,500.
Researchers recommend companies to close dormant accounts if they’ve been inactive for a larger period. Reviewing the security settings and activate the two-factor authentication option.
It is also worth checking what apps are connected to the account as well as the log of active sessions on other devices.