Cybercriminals are increasingly exploiting YouTube, a platform beloved by millions, to produce sophisticated malware attacks.
These threat actors, leveraging the impression of free software and video game enhancements, target unsuspecting users, particularly the younger demographic, to steal sensitive personal information.
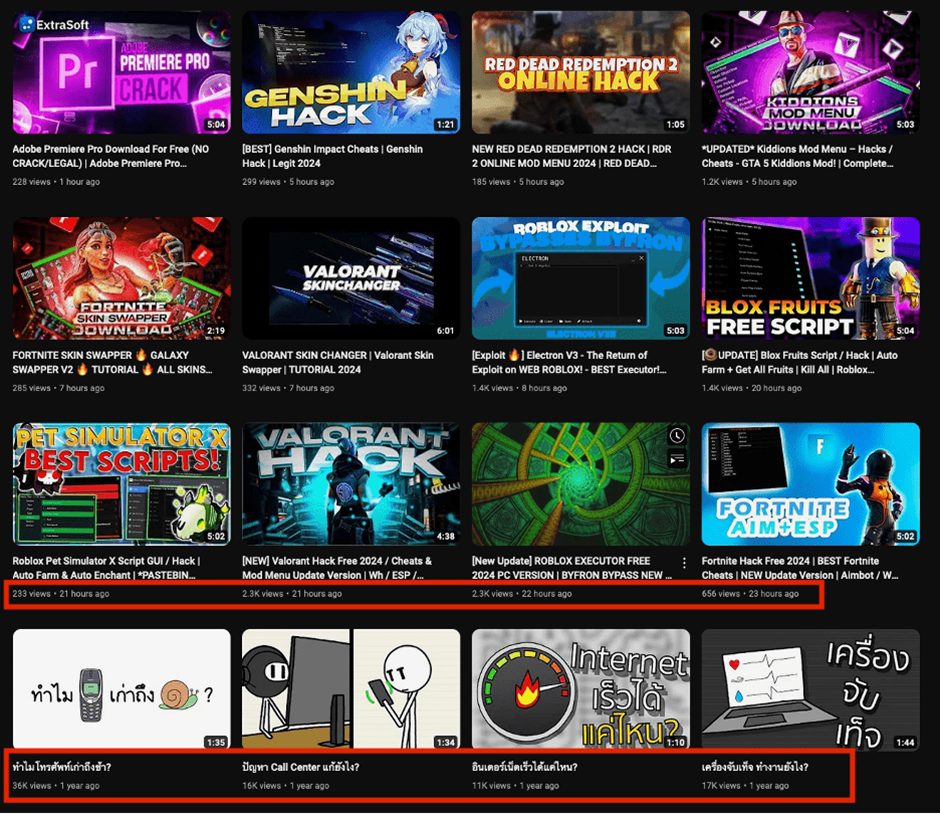
At the heart of this cyber threat are seemingly innocuous YouTube videos offering pirated software and video game cracks.
These videos, often presented as helpful guides for downloading free software or upgrading games, contain links in their descriptions that lead directly to malware.
Proofpoint Emerging Threats, a leading cybersecurity firm, has identified several instances where popular games aimed at children were used as bait, exploiting their inability to determine malicious content.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
Compromised Accounts: A Cloaked Threat
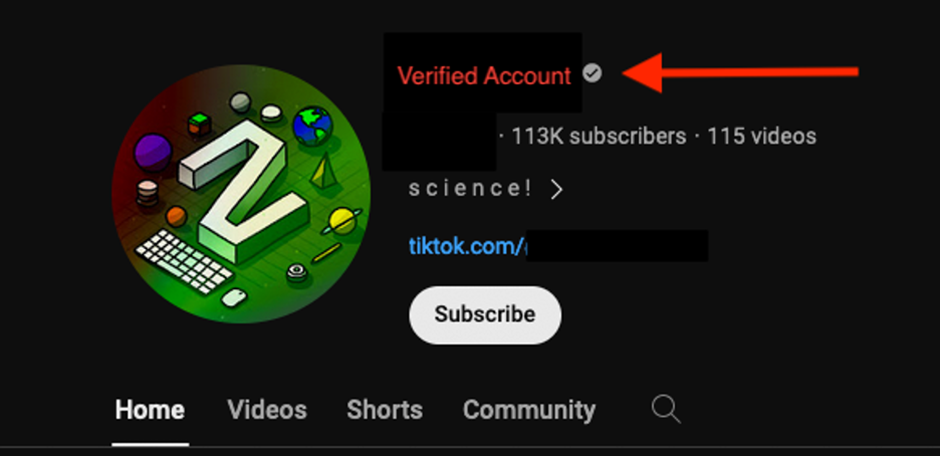
Many YouTube accounts distributing these malicious videos appear to have been compromised or acquired from legitimate users.
Proofpoint’s investigation revealed accounts with significant subscriber counts and verified status being used to spread malware.
These accounts exhibited unusual activity patterns, such as long gaps between video uploads and a sudden shift in the language and content of the videos, signaling potential compromise.
The Mechanics of Malware Distribution
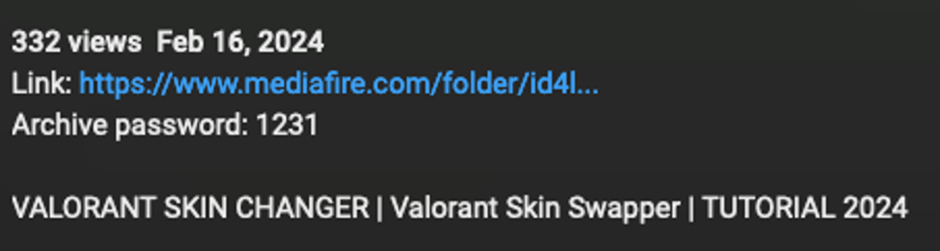
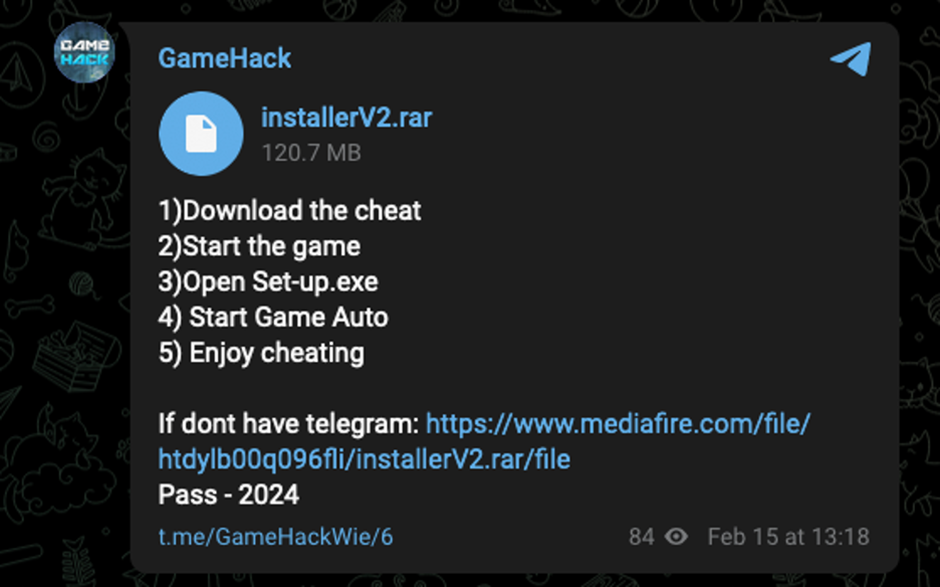
Videos often include links to password-protected files on platforms like MediaFire. These files contain executables that, once run, unleash malware onto the victim’s device.
One such malware identified is Vidar Stealer, which is known for extracting sensitive data like credit card information and cryptocurrency wallets.
Adding to the complexity, some videos impersonate well-known figures in the software piracy community, such as Empress.
These videos promise legitimate cracked content, further luring users into the trap. Distributing these links on social media platforms like Telegram adds another layer of authenticity to the scam.
Evading Detection
The malware files are designed to evade antivirus detection by incorporating large amounts of padding, making them too large for many scanning tools.
Additionally, the malware’s use of social media and community forums for command and control (C2) instructions allows it to blend in with regular network traffic, making detection challenging.
Discord: A New Frontier for Malware Distribution
A novel approach observed by Proofpoint involves the use of Discord servers to distribute malware.
These servers host files associated with different video games, complete with instructions on disabling antivirus software to facilitate the download, further endangering users.
This surge in cybercriminal activity on YouTube underscores the need for heightened awareness and caution among users.
While YouTube has been proactive in removing reported accounts, the sophistication and variety of these attacks pose a significant challenge.
Users are advised to remain skeptical of offers that seem too good to be true and to exercise caution when downloading files from the Internet.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
