A novel social engineering technique dubbed “ClickFix” has surged by an alarming 517% between the second half of 2024 and the first half of 2025, as reported by ESET telemetry data.
This manipulative attack vector, now the second most prevalent after phishing, exploits user trust in familiar online verification processes like reCAPTCHA challenges.
ClickFix deceives victims into copying and pasting malicious scripts under the guise of resolving fake errors or completing verification checks, ultimately leading to severe system compromises.
A New Social Engineering Threat Emerges
With detections under the HTML/FakeCaptcha label accounting for nearly 8% of all blocked attacks, the true scale of this threat may be even larger due to its multi-stage nature involving various payloads and obfuscation techniques.
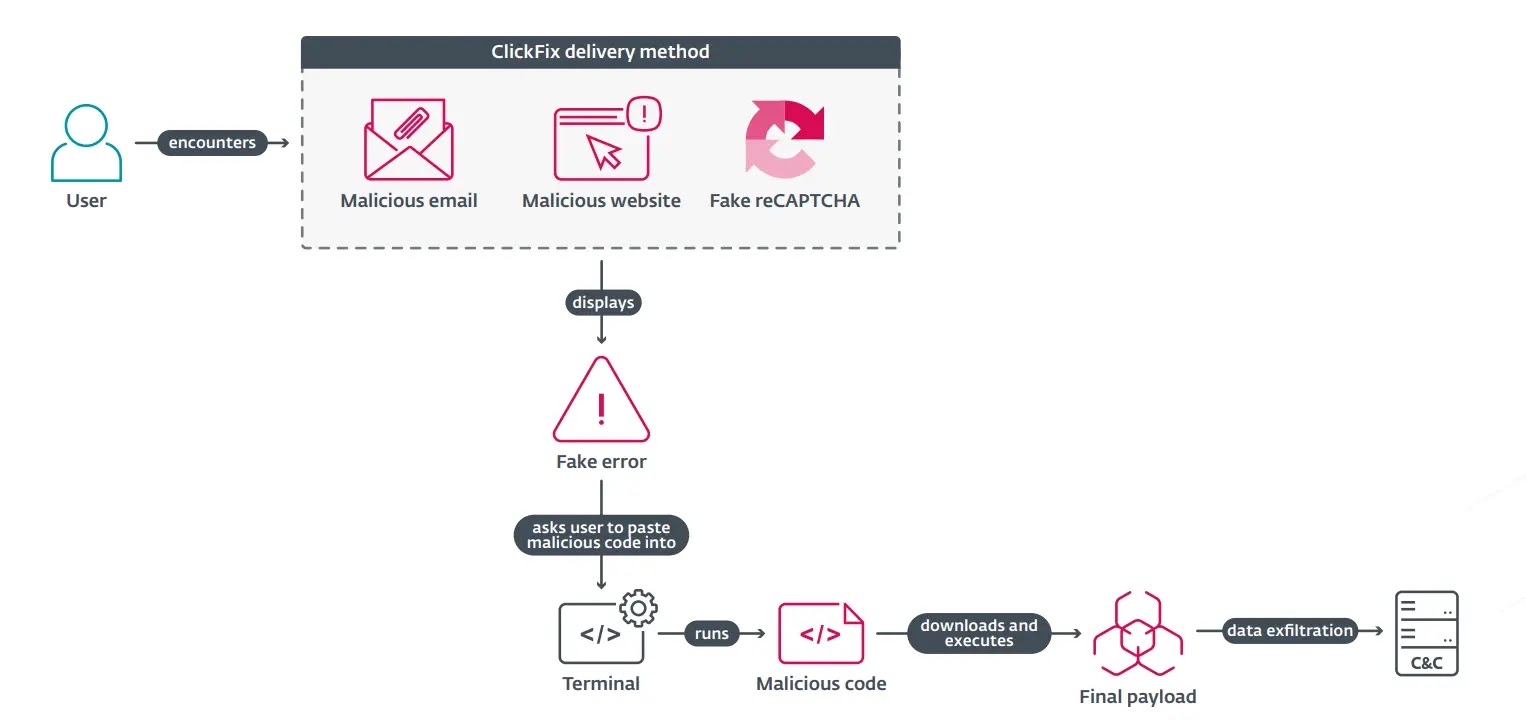
ClickFix operates by presenting users with counterfeit prompts mimicking legitimate services such as Microsoft Word, OneDrive, Booking.com, or Google Meet, often delivered via phishing emails or compromised websites.
These prompts trick users into clicking a “Fix it” button, which copies a malicious PowerShell command to their clipboard.
Victims are then instructed to execute this command in a terminal, unwittingly initiating a chain of downloads that deploy a range of threats, including infostealers like Lumma Stealer and VidarStealer, remote access trojans such as VenomRAT, ransomware like Interlock (formerly Rhysida), and even cryptominers.
From Fake Errors to Devastating Payloads
First documented in March 2024 by Proofpoint in campaigns involving threat actors like ClearFake and TA571, ClickFix has rapidly evolved, with nation-state-aligned groups such as North Korea’s Kimsuky and Russia’s Callisto adopting it for initial access across Windows, macOS, and Linux platforms.
Japan, Peru, and Poland report the highest detection rates, with Japan alone accounting for 23% of incidents, highlighting the global reach of this insidious tactic.

The sophistication of ClickFix lies in its simplicity and psychological manipulation, preying on users’ conditioned responses to routine online challenges.
As ESET Senior Detection Engineer Dušan Lacika notes, the technique’s effectiveness stems from its believable premise and the likelihood that victims overlook the malicious nature of the commands they execute.
Beyond individual users, corporate environments face heightened risks, where endpoint detection and response (EDR) tools can play a critical role in flagging anomalous PowerShell usage.
However, the proliferation of ClickFix builders on the dark web, enabling even less-skilled attackers to craft weaponized landing pages, signals a worrying democratization of this threat.
Additionally, the technique’s adaptability is evident in its use by ransomware operators like Interlock, who impersonate IT tools to deploy payloads covertly while distracting victims with legitimate-looking foreground activities.
As this threat continues to grow, there is speculation that tech giants like Microsoft and Apple, alongside the open-source community, may introduce security warnings akin to those for macros or internet-downloaded files to alert users to potential script execution risks.
For now, vigilance remains paramount users must scrutinize any unsolicited “one-click” fixes, and organizations should bolster defenses against this rapidly escalating cyber menace.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
