A sophisticated new variant of the Masslogger credential stealer has emerged, utilizing VBScript encoded (.VBE) files to deploy a multi-stage fileless malware campaign that operates entirely from the Windows Registry.
This advanced threat represents a significant evolution in information-stealing malware, demonstrating how cybercriminals are adapting their techniques to bypass traditional security measures and maintain persistence on infected systems.
The malware campaign begins with the distribution of .VBE files, likely through spam email campaigns or drive-by downloads, which serve as the initial infection vector.
.png
)
Once executed, these encoded VBScript files reveal multiple layers of obfuscation and sophisticated modular routines designed to establish a comprehensive credential harvesting operation.
The attack targets sensitive information stored in popular web browsers including Chrome, Firefox, and Edge, as well as email clients, making it particularly dangerous for both individual users and organizations.
Seqrite researchers identified this fileless variant during a recent investigation, noting its sophisticated registry-based storage mechanism and multi-stage deployment process.
.webp)
The malware’s ability to operate without writing executable files to disk represents a significant challenge for traditional antivirus solutions that rely heavily on file-based detection methods.
The malware’s impact extends beyond simple credential theft, incorporating keylogging capabilities, clipboard monitoring, screen capture functionality, and system reconnaissance features.
Additionally, the threat actors have implemented geo-targeting functionality specifically for French users, attempting to download additional payloads from remote servers when French language settings are detected on the target system.
Registry-Based Infection and Persistence Mechanism
The malware’s most distinctive characteristic lies in its sophisticated use of the Windows Registry as both a storage and execution platform.
Upon initial execution, the VBScript systematically creates multiple registry entries under the path HKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUl, where it stores obfuscated PowerShell commands, .NET assemblies, and configuration data necessary for the multi-stage infection process.
The malware employs a clever segmentation strategy, splitting the final Masslogger payload into 25,000-character chunks and distributing them across multiple registry values under HKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUldonnseg.
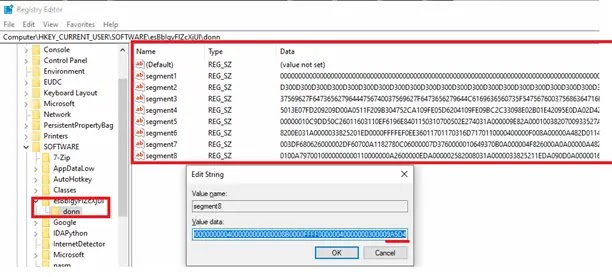.webp)
This approach effectively bypasses size limitations while maintaining the fileless nature of the attack. The malware systematically writes these segmented payloads to registry locations.
To ensure persistence, the malware establishes a Windows scheduled task that executes every minute, continuously monitoring registry values to determine when to deploy the credential stealing payload.
The task scheduler script incorporates sophisticated user input simulation techniques, using the .SendKeys method to execute PowerShell commands that appear as legitimate user activity, further complicating detection efforts by security monitoring systems.
Power up early threat detection, escalation, and mitigation with ANY.RUN’s Threat Intelligence Lookup. Get 50 trial searches.
