Hackers abuse CHM files because they can embed malicious scripts or code within them. Windows systems often trust and execute these files without many security checks.
When the CHM file is opened, it enables threat actors to deliver malware, execute arbitrary commands, and gain unauthorized access to the victim’s computer.
Cybersecurity researchers at Securonix recently identified that hackers have been actively exploiting CHM files to attack users with password-protected Zip files.
Hackers Leveraging CHM Files
The PHANTOM#SPIKE campaign which was tracked by Securonix found to be using military-themed phishing documents to deploy a simple RAT.
Free Webinar on API vulnerability scanning for OWASP API Top 10 vulnerabilities -> Book Your Spot
For the payload delivery, the threat actors utilize password-protected ZIP archives and CHM files.
The campaign is likely politically motivated, and this campaign primarily targets Pakistan-associated victims, with some payloads involving Western countries.
This approach exploits trusted file formats to bypass defenses, highlighting a concerning trend in cyber attacks.
The phishing campaign employs an archive file structure with a deceptive look to deliver a harmful CHM file and hidden EXE.
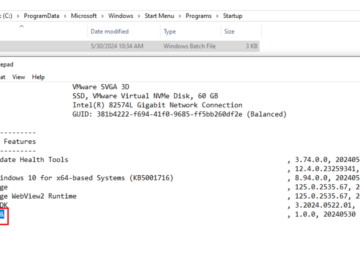
This particular CHM file that masquerades as military forum meeting minutes contains embedded pictures alongside javascript, which, upon user interaction, will cause the hidden EXE to be executed.
.webp)
This approach has previously been seen in Ukraine-targeted campaigns in which the CHM format was exploited for clandestine script execution within its HTML pages.
A malicious CHM file uses a deceptive HTML structure and embedded images to appear legitimate.
It contains an OBJECT tag with a specific classid and PARAM tags that create a shortcut to execute a hidden executable, “RuntimeIndexer.exe”, when the user clicks anywhere on the document.
This small, CSharp-written payload functions as a backdoor, connecting to a C2 server for remote command execution on the infected system.
Here below we have mentioned all of the code’s key components and functionalities:-
- Network communication and data transmission
- Command execution
- Asynchronous and hidden execution
- Post exploitation
This attack stands out for its simplicity and modularity, as it’s been found that instead of complex multi-stage sequences, it uses simple payloads.
This approach minimizes the attack surface, unlike more complicated campaigns such as STEEP#MAVERICK or STARK#VORTEX.
Recommendations
Here below we have mentioned all the recommendations:-
- Avoid downloading unsolicited files from external sources.
- Verify file extensions before executing.
- Monitor common malware staging directories, especially for script activity.
- Deploy robust endpoint logging capabilities, including Sysmon and PowerShell logging.
- Be cautious of encrypted traffic over port 443, which may hide malicious activity.
Free Webinar! 3 Security Trends to Maximize MSP Growth -> Register For Free