Security researchers at K7 Labs have uncovered a sophisticated phishing campaign targeting Brazilian users that exploits WhatsApp Web to distribute malware and steal sensitive financial information.
The attack leverages open-source WhatsApp automation scripts combined with banking trojans, spreading silently through victims’ contacts while harvesting logs, credentials, and personal data.
The campaign, identified as part of the Water-Saci malware variants, begins innocuously with a phishing email containing a ZIP archive with a malicious VBS script.
The initial payload uses charcode and XOR encoding to evade signature-based antivirus detection, masking its actual functionality from security solutions.
Once executed, the script downloads and installs Python, ChromeDriver, and the Selenium webdriver legitimate tools weaponized to automate WhatsApp Web.
The malware’s most insidious feature is its ability to hijack WhatsApp sessions without requiring QR-code authentication.
The Python script (whats.py) enumerates browser profiles from Chrome, Firefox, and Edge, extracting session artifacts including cookies, local storage, and IndexedDB files.
By leveraging these stolen session tokens, the malware launches a browser with the victim’s authenticated WhatsApp Web session already active, completely bypassing login verification.
Once authenticated, the malware injects malicious JavaScript into WhatsApp Web to access internal APIs.

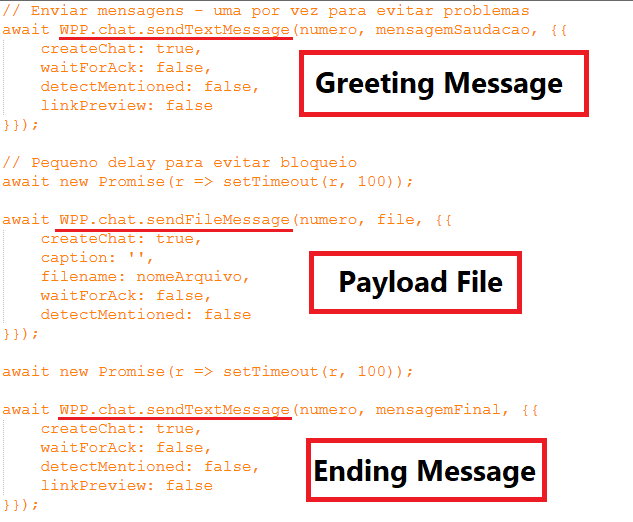
Using functions like WPP.contact.list() and WPP.chat.sendFileMessage(), it methodically harvests the victim’s contact list, filters out groups and businesses, and sends greeting messages followed by the malicious payload.
The script drops a .bat script which downloads and installs Python.zip, ChromeDriver.exe and PIP to download the webdriver from Selenium and executed a Python script whats.py.

The attachment is transferred entirely in memory as a Base64-encoded string, never touching the disk a technique designed to evade antivirus detection.
This trust-based distribution mechanism is particularly effective because recipients see messages coming from known contacts, dramatically increasing the likelihood they’ll execute the attachment.
Banking Trojan and System Reconnaissance
Parallel to WhatsApp propagation, an MSI installer deploys an AutoIt script that monitors active windows for Brazilian banking applications, cryptocurrency exchanges, and financial platforms.
When a targeted institution is detected, the script decrypts and decompresses a payload stored in encrypted .tda and .dmp files, loading the banking trojan entirely into memory using reflective injection techniques.
For each validated contact, it sends a greeting message then the payload file and then the final message: (1) sendTextMessage(number, greeting), (2) sendFileMessage(number, inMemoryFile), (3) sendTextMessage(number, closing).
Before executing the trojan, the malware conducts extensive system reconnaissance, querying WMI to identify installed antivirus products, including Windows Defender, McAfee, ESET, Kaspersky, and others.
It collects computer name, OS information, external and local IP addresses, installed security applications, and critically, browser history from Chrome to identify visited Brazilian banking sites.
The banking trojan specifically targets 20+ Brazilian financial institutions and cryptocurrency exchanges, including Banco do Brasil, Bradesco, Itaú, Santander, Binance, and Coinbase.
Recommendations
System information and harvested contacts are exfiltrated to attacker-controlled PHP servers via JSON-formatted HTTP POST requests, enabling real-time campaign tracking and configuration updates.
This multi-stage attack demonstrates how cybercriminals combine social engineering with sophisticated automation and memory-resident malware to bypass traditional defenses.
The attack’s reliance on trusted contact distribution makes it particularly dangerous.
Organizations and individuals should implement security solutions that detect anomalous WhatsApp behavior, monitor for unauthorized session access, and block suspicious file execution from communication platforms.
Employees should verify unexpected file attachments directly with contacts through alternative communication channels before opening any files, regardless of apparent sender legitimacy.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
