The role of info stealers (aka stealers) in the cybercrime world has been growing, according to researchers at the SecureWorks Counter Threat Unit (CTU).
While threat actors make use of them to steal the following data from the networks and computer systems that are compromised or breached:-
- Login credentials
- Financial details
- Personal data
- System information
Infostealers are commonly deployed onto computers and devices through various means, including:-
By using these above-mentioned TTPs, the threat actors install the info stealer onto the target’s system and gain unauthorized access to sensitive information.

Infostealers, once installed, demonstrate remarkable efficiency by executing and exiting swiftly. Within a short runtime of seconds to minutes, these malicious programs complete the collection and transmission of stolen data.
Infostealers on Underground Forums
The availability of infostealers extends to a subscription-based model, with prices varying from $50 to more than $1,000 USD per month.
These subscriptions grant users access to a C2 server operated by the developer, enabling the execution and control of the stealer.
The infostealer service typically offers various support functions, enabling users to conveniently access, download, and share the stolen data through multiple channels.
Additionally, self-hosted stealer command and control (C2) servers are offered separately as a one-time purchase, providing users with more control over their operations.
Within underground forums, threat actors convene in a collaborative environment to engage in discussions regarding ongoing projects, request enhancements for their tools, and offer evaluations of malware.
These forums serve as a shared space for cybercriminals to exchange knowledge, share expertise, and seek improvements to their malicious activities.
These forums highlight the organized and interconnected nature of the cybercrime community, fostering innovation and cooperation in their illicit endeavors.
Underground forums comprise subforums and sections encompassing diverse topics alongside administrative domains for management, including specialized marketplaces with strict regulations for selling illicit items like infostealers.
Underground forums, marketplaces, and various online platforms cater to threat actors seeking stealer logs, providing them with a means to acquire valuable resources and data like:-
- Credentials
- Financial information
- Personal data
- Banking details
- Cryptocurrency wallets
- Other sensitive data
Marketplaces offering such resources are commonly accessible exclusively through Tor or the I2P (Invisible Internet Project) anonymity services, as this ensures the privacy and anonymity of participants.
These platforms enforce stringent rules and regulations, dictating the permissible types of information that can be exchanged within their confines.
Mediums and Market places
Here below we have mentioned all the common marketplaces that the threat actors most seek:-
- Russian Market
- Genesis Market
- 2easy
- Telegram
- RaidForums
Infostealer variants
Here below, we have mentioned all the identified infostealer variants:-
- RedLine
- Raccoon
- Vidar
- Taurus
- Rhadamanthys
- State-sponsored stealers
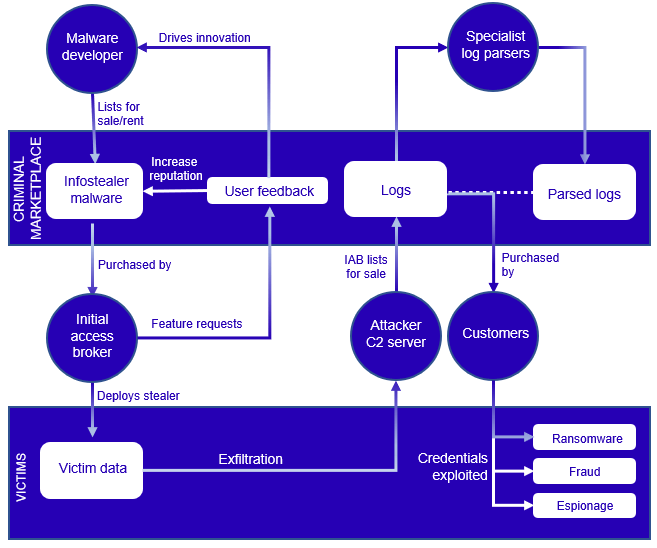
The ecosystem of the Infostealer
Similar to the broader cybercriminal ecosystem, the effective creation and implementation of infostealers depend on a diverse set of skilled individuals fulfilling various roles and responsibilities.

The development and deployment of these malicious programs necessitate expertise across different areas.
Key participants in the cybercrime ecosystem involved in the development and distribution of infostealers are:-
- Developers
- Initial access brokers (IABs)
- Customers.
The emergence of MaaS (Malware-as-a-Service) operations has significantly reduced the technical barriers for individuals who are seeking entry into the cybercrime landscape.
During Secureworks’ incident response engagements in 2022, stolen credentials played a prominent role, emphasizing the severity of the issue.
Infostealer malware presents a substantial and tangible threat to individuals and organizations alike, underscoring the need for robust cybersecurity measures.
As time progresses, this particular malware variant continues to evolve and display heightened levels of sophistication, posing challenges for victims in terms of detection and removal.
Mitigating this threat requires individuals and organizations to adopt a proactive approach to securing their systems. To stay ahead of emerging threats, it is crucial to implement robust security measures and steps like:-
- Make sure to use strong passwords.
- Regularly update software.
- Regularly update the system.
- Make sure to enable auto-updates.
- Make sure to epmply multi-factor authentication.
- Make sure to stay informed about cybersecurity best practices.
Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus
