A widespread ransomware campaign targeting misconfigured MongoDB databases continues to compromise thousands of servers worldwide, with attackers exploiting internet-exposed instances that lack basic authentication controls.
Recent research reveals that opportunistic threat actors are leveraging automated scripts to wipe databases and demand Bitcoin ransoms, turning configuration negligence into a scalable extortion operation.
Attack Resurfaces After Years of Silence
Between 2017 and 2021, MongoDB ransomware campaigns affected thousands of organizations globally.
While public reporting declined in subsequent years, recent investigations demonstrate the threat never disappeared.
In late 2025, security researchers deployed honeypot infrastructure exposing MongoDB instances without authentication across multiple geolocations.
Within days, all honeypot servers received ransom notes demanding approximately $500 USD in Bitcoin, confirming the attack pattern remains active and automated.
The resurgence was further highlighted by penetration testing that revealed two compromised MongoDB instances at a small-to-medium-sized business, both containing ransom notes.
This discovery prompted a deeper investigation into the current threat landscape, uncovering evidence that insecure deployment practices persist across tutorials, container images, and infrastructure templates.
The MongoDB ransomware attack exploits a simple yet critical vulnerability: internet-exposed databases deployed without authentication.
Automated scanning tools identify MongoDB services listening on port 27017 that accept connections from any IP address. Once discovered, attackers execute a straightforward four-step process.
First, threat actors locate vulnerable MongoDB instances through mass internet scanning. Second, they export or copy database contents to their own systems.
Third, all collections and databases on the victim server are completely wiped. Finally, attackers insert a new collection containing a ransom note demanding payment in Bitcoin within 48 hours, threatening permanent data loss if the victim fails to comply.
Security experts strongly advise against paying ransoms, as victims who complied frequently reported receiving nothing in return.
In many cases, attackers never actually retained copies of the stolen data, making recovery impossible regardless of payment.
Massive Exposure Revealed Through Internet Scanning
Analysis using Shodan, an internet-connected device search engine, identified over 200,000 publicly discoverable MongoDB servers.
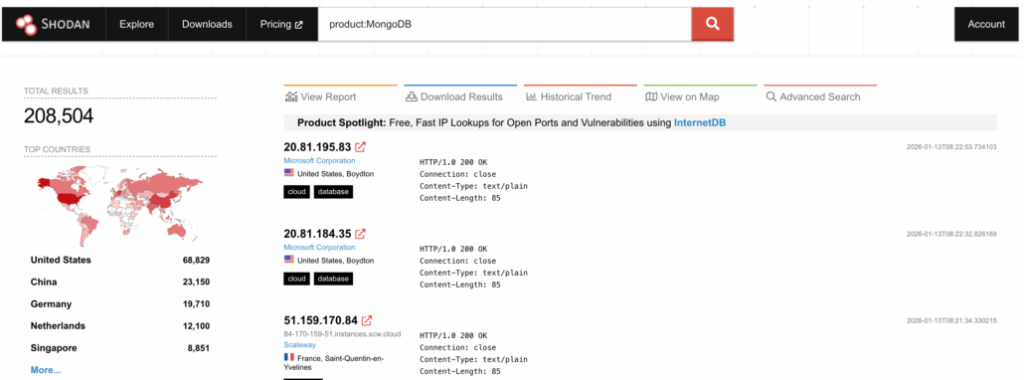
Of these, more than 100,000 instances disclosed operational information, while 3,100 servers were fully exposed without access restrictions or authentication requirements.
| Metric | Count | Percentage |
|---|---|---|
| Total MongoDB servers discovered | 200,000+ | – |
| Servers with operational information | 100,000+ | – |
| Fully exposed instances (no authentication) | 3,100 | 100% |
| Compromised instances (wiped with ransom) | 1,416 | 45.6% |
| Servers with at least one vulnerability | 95,000 | 46.3% |
Among the 3,100 fully exposed servers, 1,416 instances (45.6%) had already been compromised, with databases wiped and replaced by ransom notes. Nearly all incidents demanded approximately $500 USD in Bitcoin.
Significantly, only five distinct Bitcoin wallets were observed across all attacks, with a single wallet address (bc1qe2l4ffmsqfdu43d7n76hp2ksmhclt5g9krx3du) present in over 98% of cases, strongly suggesting a single dominant threat actor.
The discrepancy between exposed servers and compromised instances raises questions about the remaining 1,684 systems.
Some may represent test environments or systems that have been taken offline. In contrast, others could have paid the ransom, leaving no visible evidence of compromise.
Even if only a portion is paid, the campaign’s revenue could range from zero to approximately $842,000 USD.
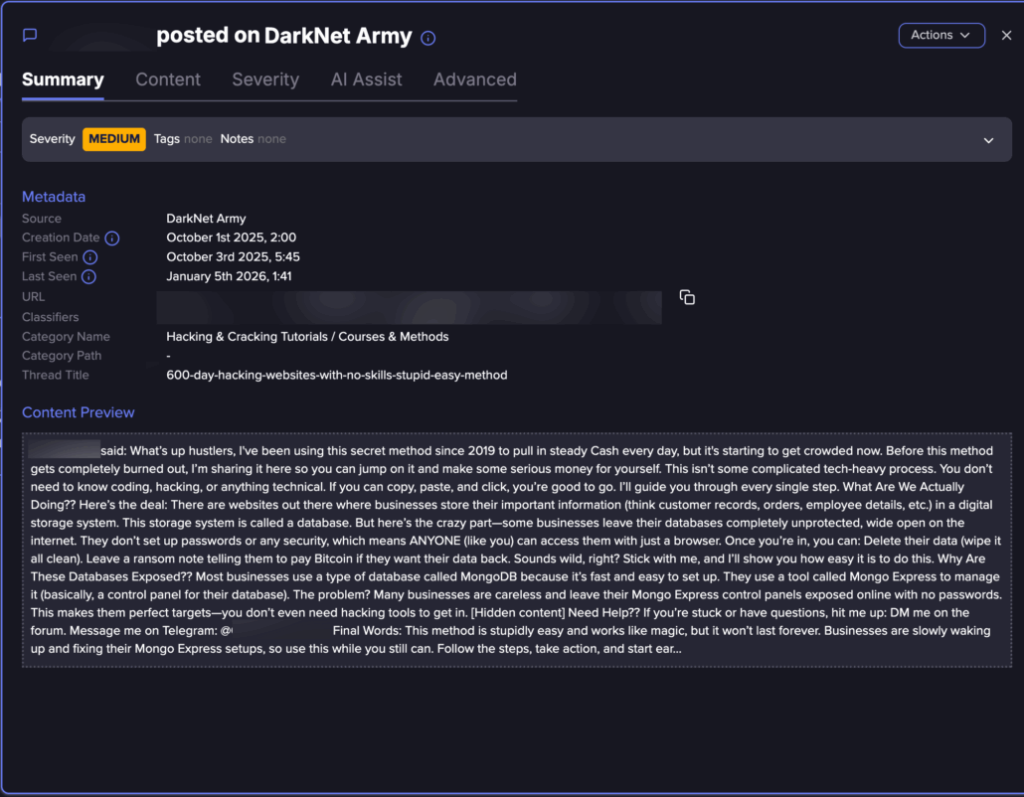
Threat intelligence gathering revealed active MongoDB ransom tutorials circulating on dark web forums and Tor websites.
One tutorial discovered in 2025 explicitly marketed the attack method as requiring no technical expertise, claiming attackers could “pull in steady cash every day” by targeting exposed databases.
The tutorial provided step-by-step instructions describing how businesses often leave MongoDB and its management interface, Mongo Express, exposed online without passwords.
The guide emphasized that the method required only basic computer skills “if you can copy, paste, and click, you’re good to go” lowering the barrier to entry for aspiring cybercriminals.
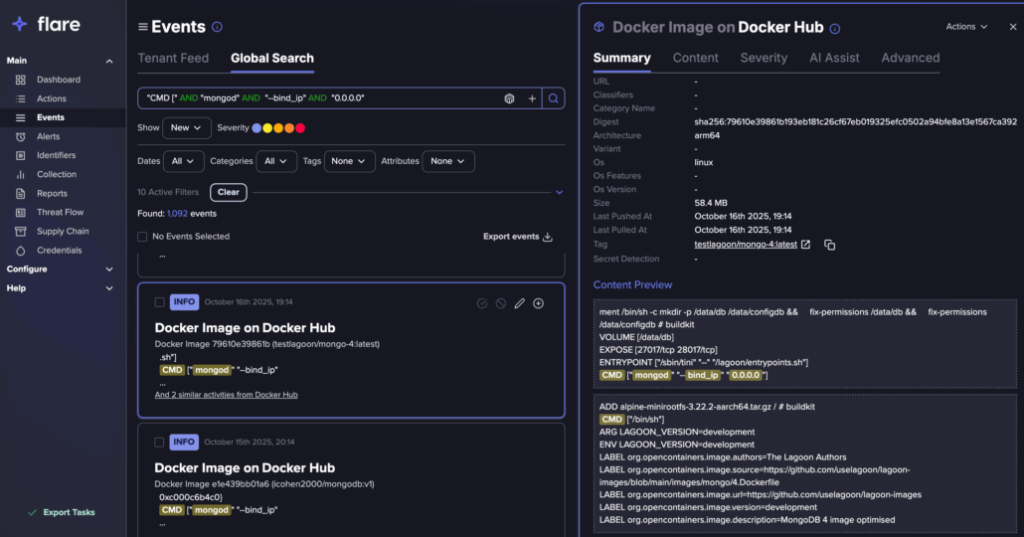
Security researchers from Flare also analysed Docker Hub and GitHub repositories, identifying 763 container images containing insecure MongoDB configurations that bind the database to all network interfaces (0.0.0.0) without authentication.
These images spanned 30 distinct namespaces over three months, with two widely-used projects each exceeding 15,000 pulls.
This distribution mechanism enables insecure configurations to propagate rapidly through copy-paste deployment practices.

Furthermore, searches for exposed MongoDB credentials yielded 17,909 potential results, of which approximately half were validated as functional credentials that attackers could exploit.
These credentials appeared across coding repositories (GitHub, Docker Hub), dark web forums, paste sites, and breach databases.
MITRE ATT&CK Framework Mapping
The MongoDB ransom campaign demonstrates a complete attack lifecycle aligned with the MITRE ATT&CK framework, despite its technical simplicity.
| Tactic | Technique ID | Technique Name | Description |
|---|---|---|---|
| Initial Access | T1190 | Exploit Public-Facing Application | Connect to exposed MongoDB without authentication |
| Discovery | T1046 | Network Service Discovery | Scan IP ranges for open MongoDB port 27017 |
| Discovery | T1087 | Account Discovery | Enumerate databases and collections |
| Collection | T1213 | Data from Information Repositories | Dump databases to assess value |
| Impact | T1485 | Data Destruction | Drop/wipe collections and databases |
| Impact | T1489 | Service Disruption | Disrupt business operations |
| Impact | T1657 | Extortion | Insert ransom note demanding Bitcoin payment |
Notably, the attack requires no privilege escalation, lateral movement, or malware deployment.
Attackers operate entirely within permissions granted by insecure default configurations, making detection challenging and favoring reactive responses over preventative measures.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.